
Difference Between Risk Assessment and Risk Management: 2026 Complete Guide
Difference Between Risk Assessment and Risk Management: 2026 Complete Guide
The difference between risk assessment and risk management is one of the most misunderstood topics in governance, compliance, and cybersecurity, and the confusion is not harmless. Many organizations believe they are “managing risk” when they are only documenting it. Others complete detailed assessments yet fail to act on the findings, leaving the same risks to resurface year after year.
This misunderstanding has become more costly as regulatory pressure increases and digital exposure expands. From data privacy laws to cybersecurity obligations, businesses are now expected to show not only that risks were identified, but that they were actively addressed, monitored, and reviewed. That expectation requires a clear understanding of how risk assessment and risk management differ, and how they work together.
Risk assessment focuses on identifying and evaluating potential threats, what could go wrong, how likely it is, and how severe the impact might be. Risk management, on the other hand, is the broader, ongoing process of deciding what to do about those risks and ensuring controls remain effective over time.
This guide explains the difference in practical terms, clarifies their relationship, and uses real-world examples, including cybersecurity contexts, to show how organizations should apply both correctly.

Start a Life-Changing Career in Cybersecurity Today
What Is Risk Assessment?
Risk assessment is the structured process used to identify, analyze, and evaluate potential risks that could negatively affect an organization, a project, or a specific activity. Its primary purpose is to help decision-makers understand what could go wrong, how likely it is to happen, and how serious the consequences would be if it did.
In practice, risk assessment answers three fundamental questions:
- What are the risks?
- How likely are they to occur?
- What impact would they have on people, operations, finances, or data?
Risk assessment is not about fixing problems. It is about clarity and measurement. Organizations rely on it to create a clear picture of their risk landscape before deciding what actions to take. This is why risk assessment is considered the foundation of effective risk management.
Key Components of Risk Assessment
A standard risk assessment process is built around three core components.
Risk identification involves recognizing potential sources of harm or failure. These could include operational breakdowns, safety hazards, compliance gaps, cybersecurity threats, or supplier dependencies.
Risk analysis focuses on understanding the nature of each identified risk. This step examines the likelihood of occurrence and the potential consequences if the risk materializes.
Risk evaluation compares analyzed risks against predefined criteria, such as severity thresholds or risk tolerance levels. This allows organizations to prioritize risks and determine which ones require immediate attention and which can be monitored.
Risk Assessment Example
A simple risk assessment example can be seen in cybersecurity. An organization may identify customer data as a critical asset, recognize phishing attacks as a threat, and analyze the likelihood of such attacks based on past incidents. The evaluation step then determines whether the risk level is acceptable or requires further action.
At this stage, no controls are implemented yet. The outcome is insight, not intervention. That distinction is what separates risk assessment from risk management.
What Is Risk Management?
Risk management is the ongoing, organization-wide process of controlling, reducing, or responding to risks after they have been identified and assessed. While risk assessment helps an organization understand its exposure, risk management determines what actions to take and how to sustain those actions over time.
In simple terms, risk assessment identifies and measures risk. Risk management decides how that risk will be handled, who is responsible, and how effectiveness will be monitored. This makes risk management a strategic and operational discipline, not a one-time activity.
Risk management extends beyond documentation. It involves decision-making, resource allocation, and continuous oversight to ensure risks remain within acceptable limits defined by leadership.
Core Stages of Risk Management
An effective risk management process typically includes several interconnected stages.
Risk identification and assessment form the entry point. Organizations rely on risk assessment outputs to understand exposure and priority.
Risk treatment or response is where action begins. This may involve avoiding the risk entirely, reducing its likelihood or impact through controls, transferring the risk through insurance or outsourcing, or formally accepting it when mitigation is not practical.
Implementation of controls ensures that chosen responses are embedded into processes, systems, and behaviors. This could include technical safeguards, policy updates, training programs, or operational changes.
Monitoring and review keep the process alive. Risks evolve, controls weaken, and business environments change. Continuous monitoring ensures that controls remain effective and that new risks are identified early.
Risk Assessment and Management Example
Consider a financial services company that identifies unauthorized system access as a high-risk issue during a risk assessment. Risk management begins when the organization decides to implement multi-factor authentication, assign ownership to the IT security team, train staff on access protocols, and review access logs regularly.
In this example, risk assessment provides awareness. Risk management delivers action, accountability, and continuity.
RELATED: Vendor Risk Management (VRM) in 2025
Difference Between Risk Assessment and Risk Management
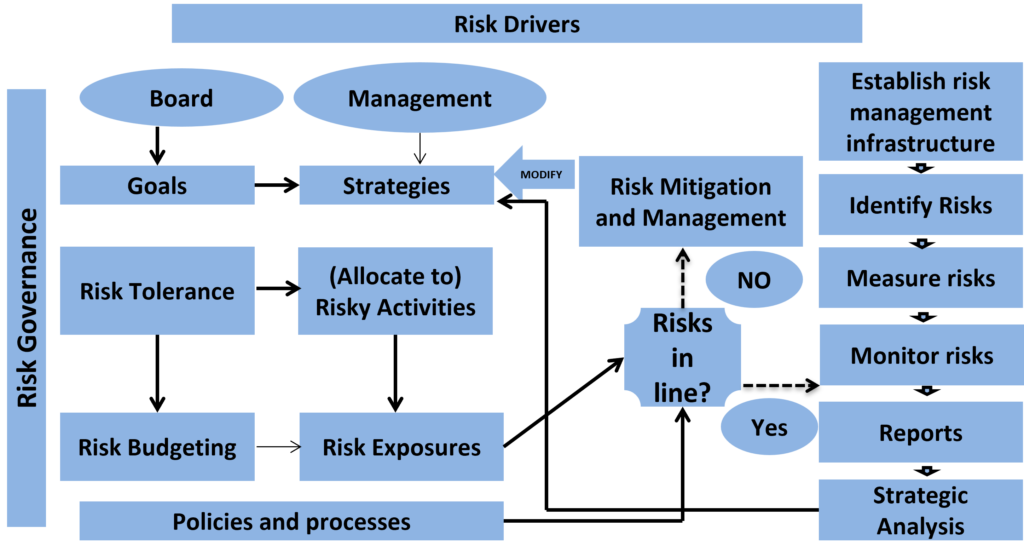
Although risk assessment and risk management are closely connected, they serve distinct roles within an organization’s risk framework. Confusing the two often leads to incomplete controls, repeated incidents, and a false sense of security. Understanding the difference between risk assessment and risk management is essential for applying both correctly.
Scope and Purpose
Risk assessment is focused and analytical. Its purpose is to identify, analyze, and evaluate risks so decision-makers clearly understand potential threats and their severity. It answers the question: What could go wrong, and how bad would it be?
Risk management is broader and action-oriented. It uses the output of risk assessments to design, implement, and maintain responses to those risks. Its purpose is to ensure risks are handled in a way that aligns with the organization’s objectives and risk appetite.
In short, risk assessment provides insight. Risk management provides control.
Timing and Frequency
Risk assessment is typically conducted at specific points in time. This may occur before launching a new project, introducing new technology, responding to regulatory changes, or after an incident. While it should be reviewed periodically, it is not inherently continuous.
Risk management, on the other hand, is a continuous process. It operates alongside daily business activities and evolves as new risks emerge or existing risks change. Monitoring, reporting, and improvement are constant features of effective risk management.
Output and Decision-Making
The output of risk assessment is usually a documented evaluation, such as a risk register or matrix, showing risk levels, likelihood, and impact. These outputs inform decisions but do not execute them.
Risk management translates those findings into decisions and actions. It assigns ownership, implements controls, allocates resources, and tracks performance. It also ensures that leadership can see whether risk responses are working as intended.
What Is the Difference Between Risk Assessment and Risk Management? Two Examples of Each
Risk assessment examples:
- Identifying ransomware as a potential threat to customer data and evaluating its likelihood and financial impact.
- Reviewing workplace operations to assess the probability and severity of employee injury during equipment use.
Risk management examples:
- Deploying endpoint protection, enforcing backup policies, and monitoring systems to reduce ransomware risk.
- Introducing safety procedures, training programs, and inspections to reduce the likelihood of workplace injuries.
These examples show the practical difference clearly. Risk assessment identifies and measures risk. Risk management acts on that information to reduce harm and maintain control.
ALSO READ: What Are Capture-the-Flag Competitions in Cybersecurity?
Relationship Between Risk Assessment and Risk Management
Risk assessment and risk management are not separate or competing activities. They are interdependent parts of the same risk discipline, each relying on the other to be effective. Understanding their relationship helps organizations avoid treating risk as a one-time exercise instead of a living process.
Risk assessment acts as the starting point. It provides structured insight into what could go wrong, how likely it is to happen, and what the consequences might be. Without this clarity, risk management decisions are often based on assumptions, intuition, or incomplete information.
Risk management builds directly on those assessment results. It uses the findings to determine which risks require action, what type of response is appropriate, and how resources should be allocated. In this sense, risk assessment informs risk management, while risk management operationalizes risk assessment.
The relationship is cyclical rather than linear. Once risk management controls are implemented, their effectiveness must be monitored. Changes in the business environment, technology, regulations, or threat landscape can alter risk levels. When that happens, new or updated risk assessments are required, feeding fresh data back into the risk management process.
A simple way to view the relationship is this:
Risk assessment defines the problem.
Risk management delivers and sustains the solution.
When organizations separate the two or treat risk assessment as an endpoint, risk management becomes reactive. When they are properly linked, risk decisions become consistent, auditable, and aligned with strategic goals.
Risk Assessment and Management in Cyber Security
Cybersecurity is one area where the distinction, and connection, between risk assessment and risk management becomes especially clear. Threats evolve quickly, systems change frequently, and the impact of failure can extend beyond financial loss to legal penalties and reputational damage. As a result, organizations must apply both processes correctly to stay resilient.
Why Cybersecurity Requires Both
In cybersecurity, risk assessment helps organizations understand where they are exposed. This includes identifying critical assets such as customer data, intellectual property, or operational systems, and evaluating threats like phishing, ransomware, insider misuse, or third-party breaches. Without this step, security efforts often focus on tools rather than actual risk.
Risk management ensures that cybersecurity does not stop at awareness. It turns assessment findings into controls, policies, and ongoing oversight. This includes deciding which risks must be reduced immediately, which can be monitored, and which are acceptable given business objectives.
Cybersecurity Risk Assessment Example
A typical risk assessment example in cybersecurity begins with identifying a core asset, such as a customer database containing personal information. The organization then identifies potential threats, such as credential theft or unauthorized access through phishing attacks.
Next, the likelihood of those threats is analyzed based on factors like past incidents, employee behavior, and existing safeguards. The impact is also evaluated, considering regulatory fines, operational disruption, and loss of customer trust. The result is a risk rating that shows whether the exposure is low, medium, or high.
At this stage, the organization has not yet acted. It has only measured and prioritized the risk.
Cybersecurity Risk Management in Practice
Risk management begins once decisions are made about how to respond to the assessed risk. Using the previous example, the organization may choose to reduce the risk by implementing multi-factor authentication, strengthening email security, conducting staff awareness training, and assigning responsibility to a security team for ongoing monitoring.
Risk management also includes tracking whether these controls are effective, reviewing logs, testing incident response plans, and reassessing risks when systems or regulations change. This ongoing cycle ensures that cybersecurity remains aligned with real-world threats rather than static assumptions.
In cybersecurity, risk assessment provides visibility. Risk management provides protection.
SEE MORE: What Are Governance Risk and Compliance GRC Certifications?
Difference Between Risk Assessment and JSA (Job Safety Analysis)

Risk assessment is often confused with Job Safety Analysis (JSA), especially in industries such as construction, manufacturing, oil and gas, and utilities. While both focus on preventing harm, they differ significantly in scope, application, and purpose.
What Is a Job Safety Analysis (JSA)?
A Job Safety Analysis is a task-specific safety tool used to identify hazards associated with a particular job or activity before work begins. It breaks a task into individual steps, examines the hazards at each step, and defines safe work practices to prevent accidents or injuries.
JSAs are commonly used for high-risk activities such as operating heavy machinery, performing maintenance work, working at heights, or handling hazardous materials. Their focus is narrow and immediate: keeping workers safe while performing a specific task.
How JSA Differs from Risk Assessment
The primary difference between risk assessment and JSA lies in breadth and intent. Risk assessment takes a broader view of potential risks across an organization, process, system, or project. It may include safety risks, but it also covers operational, financial, compliance, environmental, and cybersecurity risks.
JSA, by contrast, is limited to occupational safety and specific job tasks. It does not typically assess wider business impacts, regulatory exposure, or long-term risk trends.
Another key difference is timing. JSAs are usually performed immediately before work begins and may be repeated daily or per task. Risk assessments are conducted at defined intervals or when significant changes occur, such as new processes, equipment, or regulations.
When Risk Assessment and JSA Overlap
In safety-critical environments, JSAs often draw input from broader risk assessments. For example, a risk assessment may identify hot work as a high-risk activity across a facility. A JSA is then used at the task level to ensure specific controls are applied every time that work is performed.
In this way, risk assessment sets the context, while JSA enforces safe execution on the ground.
READ: Risk Analysis in Cyber Security: 2025 Complete Analysis
Common Mistakes Organizations Make
Even organizations that invest time and resources into risk programs often undermine their effectiveness through avoidable mistakes. These errors usually stem from misunderstanding the difference between risk assessment and risk management or failing to connect the two properly.
One common mistake is treating risk assessment as a checkbox exercise. Teams complete assessments to satisfy audits or regulatory requirements, then file the reports away without translating findings into concrete actions. When this happens, risks remain unchanged despite being well documented.
Another frequent issue is failing to assign ownership. Identifying risks without clearly defining who is responsible for managing them leads to stalled mitigation efforts. Risk management requires accountability, not just awareness.
Some organizations also rely on outdated assessments. Risks evolve as technologies, regulations, and business models change. Using old data to make current decisions creates blind spots, especially in fast-moving areas like cybersecurity.
Siloed risk management is another challenge. When departments manage risks independently without coordination, critical connections are missed. A technical risk in one area may trigger compliance or operational risks elsewhere, but those linkages go unnoticed.
Finally, many organizations underestimate the importance of continuous monitoring. Controls that are effective today may fail tomorrow if they are not reviewed and tested regularly. Risk management is not static, and treating it as such weakens the entire framework.
Conclusion
The difference between risk assessment and risk management becomes clear once their roles are properly separated. Risk assessment is about understanding risk, identifying what could go wrong, how likely it is to happen, and how severe the impact could be. Risk management is about controlling risk, deciding what actions to take, implementing those actions, and ensuring they remain effective over time.
Risk assessment provides the insight organizations need to make informed decisions. Risk management turns that insight into structured action, accountability, and continuous oversight. One without the other leaves gaps: assessment without management leads to inaction, while management without assessment leads to guesswork.
In practice, both must work together as part of a continuous cycle, especially in areas like cybersecurity, compliance, and operational safety. Organizations that clearly understand and apply both processes are better positioned to reduce uncertainty, meet regulatory expectations, and protect their assets.
FAQ
What are the 5 Rs of risk assessment?
The 5 Rs of risk assessment describe how an organization can respond to identified risks:
Recognize – Identify and acknowledge the risk.
Rate – Assess the likelihood and impact of the risk.
Respond – Decide on the appropriate action (avoid, reduce, transfer, or accept).
Record – Document the risk, analysis, and decisions made.
Review – Reassess the risk regularly to ensure controls remain effective.
These steps help ensure risk assessment is not a one-off activity but part of a structured cycle.
What are the 5 P’s of risk assessment?
The 5 P’s of risk assessment are commonly used to analyze operational and workplace risks:
People – Risks related to employees, contractors, or human behavior.
Plant – Machinery, tools, and equipment risks.
Procedures – Risks arising from poor or unclear processes.
Place – Environmental or location-based risks.
Products – Risks linked to materials, outputs, or services.
This framework is especially useful in safety, manufacturing, and operational settings.
What are the four risk assessment tools?
Commonly used risk assessment tools include:
Risk Matrix – Visualizes risk based on likelihood and impact.
Checklists – Structured lists to identify common or known risks.
Failure Modes and Effects Analysis (FMEA) – Identifies how processes can fail and the impact of those failures.
SWOT Analysis – Evaluates risks and opportunities from internal and external factors.
Each tool supports different levels of risk complexity and decision-making.
Who is responsible for risk assessment?
Responsibility for risk assessment typically sits with management, but it is a shared responsibility across the organization.
– Senior leadership defines risk appetite and ensures assessments are conducted.
– Managers and supervisors assess risks within their areas of control.
– Employees contribute by identifying hazards and reporting issues.
– In regulated environments, compliance, safety, or cybersecurity teams often coordinate and document the process.
– Effective risk assessment works best when accountability is clear, and participation is collective.
