
Risk Analysis in Cyber Security: 2025 Complete Analysis
Risk Analysis in Cyber Security: 2025 Complete Analysis
The rise of data breaches, ransomware attacks, and insider threats has made risk analysis in cybersecurity a cornerstone of modern defense strategies. According to IBM’s 2024 Cost of a Data Breach Report, the global average cost of a breach has climbed to nearly $5 million, underscoring how devastating a single incident can be for organizations of any size.
At its core, risk analysis means systematically identifying, evaluating, and prioritizing threats that could compromise an organization’s information systems. It is a technical exercise and a business necessity. Without proper risk identification in cybersecurity, companies struggle to allocate resources effectively, comply with regulatory requirements, and maintain the trust of customers and stakeholders.
This article examines the importance of risk analysis in cyber security, breaking down the types of risks organizations face, the frameworks that guide them, and the step-by-step process for conducting an effective cybersecurity risk assessment. Along the way, we’ll examine real-world case studies, highlight common challenges, and show how businesses can use insights from a cybersecurity risk assessment report to strengthen resilience.

Start a Life-Changing Career in Cybersecurity Today
What Are Cybersecurity Risks?
Cybersecurity risks are potential threats that exploit weaknesses in an organization’s digital systems, leading to unauthorized access, theft, or damage. They can stem from malicious actors, technical flaws, or even unintentional employee mistakes. Understanding these risks is the first step in effective risk management in cybersecurity.
Common Types of Cybersecurity Threats
- Malware and Ransomware: Malicious software that corrupts systems or locks data until a ransom is paid.
- Phishing Attacks: Deceptive emails or messages designed to trick users into revealing sensitive information.
- Insider Threats: Employees or contractors who intentionally or unintentionally expose data to unauthorized parties.
- Data Breaches: Large-scale incidents where sensitive information is accessed or stolen by attackers.
Each of these threats has far-reaching consequences. A ransomware attack, for instance, can halt operations for days. A phishing email that compromises employee credentials might expose customer records, resulting in legal liabilities and reputational harm.
The Business Impact of Cybersecurity Risks
- Financial Loss: Fraudulent transactions, ransom payments, and regulatory fines can cripple budgets.
- Reputational Damage: Customers lose trust quickly after a breach, making recovery difficult.
- Operational Disruption: Attacks can shut down entire systems, halting productivity and revenue streams.
- Legal and Compliance Penalties: Failing to protect sensitive data may violate standards like GDPR, HIPAA, or PCI DSS, attracting heavy fines.
The Role of Risk Analysis in Cybersecurity
Risk analysis goes beyond simply listing threats. It provides a structured way to measure the likelihood of those threats occurring and the severity of their potential impact. This process ensures that organizations aren’t just reacting to cyber incidents but are proactively shaping defenses.
Why Risk Analysis Matters
The importance of risk analysis in cybersecurity lies in its ability to align security with business priorities. Not every risk deserves the same level of attention; some can be tolerated, while others could severely damage operations. Through proper analysis, companies can:
- Identify risks that pose the greatest threat to critical assets.
- Prioritize resources so the most dangerous vulnerabilities are addressed first.
- Support compliance efforts by providing documented evidence of a systematic approach to security.
From Risk Assessment to Risk Analysis
It’s easy to confuse a cybersecurity risk assessment with risk analysis, but they play different roles. A risk assessment is broader: it identifies and catalogs all possible risks. Risk analysis is the deeper step; it evaluates those risks in detail, measuring their likelihood and impact.
Together, they provide the foundation for:
- Risk Mitigation: Reducing the chance or effect of an attack.
- Risk Transfer: Shifting responsibility through methods like cyber insurance.
- Risk Acceptance: Choosing to tolerate low-impact risks.
- Risk Avoidance: Removing risky activities altogether.
Integrating Into Risk Management
When performed regularly, risk analysis strengthens overall risk management in cybersecurity. It turns abstract threats into actionable insights and helps leadership make informed decisions about investments, policies, and employee training. A good cybersecurity risk assessment tool can automate parts of this process, ensuring consistency and scalability across the organization.
In short, risk analysis is not just a defensive measure; it is a strategic enabler that ties cybersecurity directly to business continuity and growth.
RELATED: Vendor Risk Management (VRM) in 2025
Frameworks and Standards Guiding Risk Analysis
Organizations don’t have to start from scratch when conducting a cybersecurity risk assessment. Several international frameworks and standards provide proven models for carrying out consistent and repeatable risk analysis processes. These frameworks also make it easier to generate a defensible cybersecurity risk assessment report that satisfies regulators, auditors, and stakeholders.
NIST (National Institute of Standards and Technology)
NIST’s SP 800-30 Guide for Conducting Risk Assessments remains one of the most widely used references. It outlines practical steps for identifying risks, estimating likelihood, and determining potential impact. The broader NIST Cybersecurity Framework (CSF) helps organizations integrate analysis into a continuous cycle of identifying, protecting, detecting, responding, and recovering.
Strengths: Flexibility and adaptability for organizations of all sizes.
Limitations: Requires tailoring; it’s not a plug-and-play tool.
ISO/IEC 27001 and 27005
ISO standards bring a global perspective. ISO/IEC 27001 defines the requirements for an information security management system (ISMS), while ISO 27005 focuses specifically on risk management in cybersecurity. Together, they provide a structured, process-driven approach that emphasizes continual improvement.
Strengths: Recognized globally; highly structured and process-oriented.
Limitations: Can be resource-intensive to implement and maintain.
ISACA’s COBIT
COBIT (Control Objectives for Information and Related Technologies) integrates cybersecurity risk into broader IT governance. It is particularly valuable for enterprises that need to align IT risk analysis with business goals, compliance obligations, and performance outcomes.
Strengths: Business-focused, linking cybersecurity risks with strategic objectives.
Limitations: May be too high-level without complementary technical frameworks.
Why Frameworks Matter
Choosing the right framework, or combining elements of several, gives organizations a consistent methodology for analysis. It also simplifies adoption of cybersecurity risk assessment tools, which are often designed to align with these standards. Ultimately, frameworks reduce guesswork, improve accountability, and ensure that risk analysis supports both compliance and resilience.
READ ALSO: How Long Does It Take to Get a Cybersecurity Certificate Online?
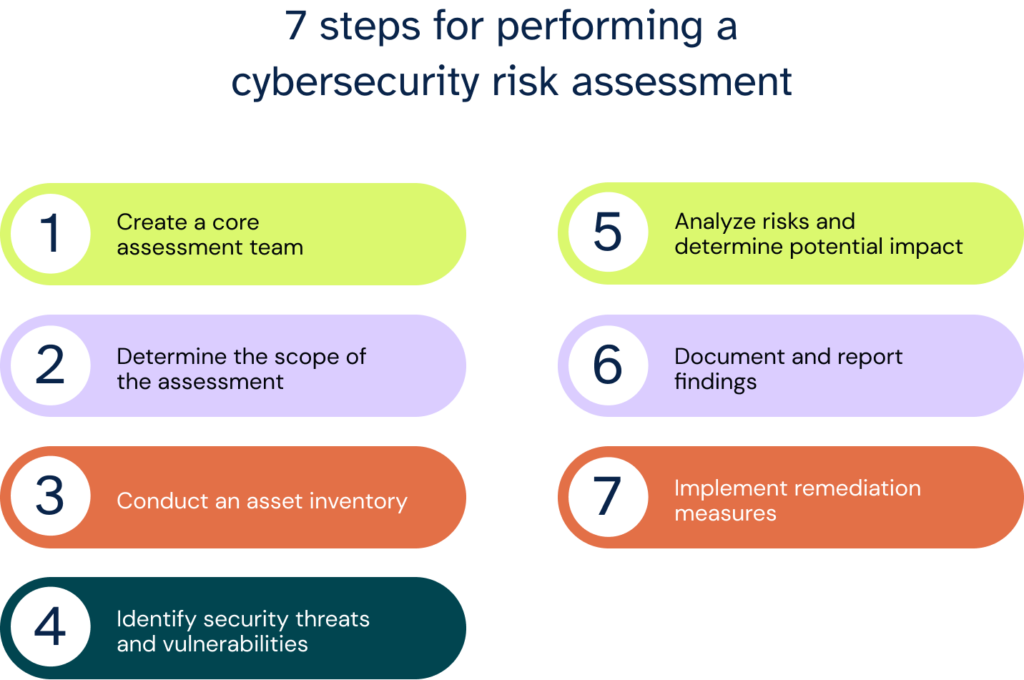
Steps in Conducting a Cybersecurity Risk Analysis
Carrying out a thorough cybersecurity risk assessment involves more than just identifying threats. It follows a series of structured steps that ensure risks are not only recognized but also measured, prioritized, and documented in a way that leads to action. These steps also form the backbone of any credible cybersecurity risk assessment report.
1. Identify Assets and Resources
The process begins with a complete inventory of digital assets, servers, applications, endpoints, data repositories, and cloud services. Understanding what needs protection helps narrow the focus of risk analysis.
2. Risk Identification in Cybersecurity
Once assets are clear, the next step is to identify risks that could compromise them. This includes external threats (hackers, malware, ransomware), internal threats (employee errors, malicious insiders), and environmental factors (natural disasters, power outages). Risk identification in cybersecurity ensures organizations can map potential attack vectors before they are exploited.
3. Vulnerability Assessment
Organizations must evaluate where weaknesses exist, whether in outdated software, weak passwords, poor access controls, or misconfigured networks. Vulnerability scanning tools and penetration testing are commonly used here.
4. Impact and Likelihood Assessment
Each identified risk must be analyzed to determine two factors:
- Impact: How damaging would the risk be if exploited? (e.g., data loss, financial penalties, reputational harm)
- Likelihood: How probable is the risk, based on trends, historical incidents, and industry benchmarks?
This stage is where qualitative and quantitative types of risk analysis in cybersecurity come into play. Qualitative methods categorize risks as “high,” “medium,” or “low,” while quantitative methods use numerical models to estimate financial costs or probabilities.
5. Risk Prioritization
Using a risk matrix or heat map, organizations rank risks by severity. High-impact, high-likelihood risks rise to the top, guiding leadership on where to allocate budget and staff.
6. Documentation and Reporting
The insights from the above steps must be captured in a structured cybersecurity risk assessment report. This report acts as both a roadmap for mitigation and an accountability tool for regulators, executives, and stakeholders.
Developing a Risk Management Plan
Once risks are identified, assessed, and prioritized, the next step is to decide how to handle them. A strong risk management plan in cybersecurity outlines strategies for addressing threats in ways that balance cost, practicality, and business objectives.
Core Strategies for Managing Risks
- Accept: Some risks are tolerable if the potential impact is low or the cost of mitigation outweighs the benefits.
- Avoid: Stop activities that introduce excessive risk, such as retiring outdated systems that cannot be secured.
- Transfer: Shift the risk to a third party, cyber insurance or outsourcing certain functions are common examples.
- Mitigate: Apply technical, administrative, and physical controls to reduce either the likelihood or the impact of the threat.
The Role of Cybersecurity Controls
Controls are the backbone of mitigation strategies. They are typically grouped into three categories:
- Technical Controls: Firewalls, multi-factor authentication, intrusion detection systems, and encryption.
- Administrative Controls: Policies, training programs, and incident response procedures.
- Physical Controls: Access badges, surveillance cameras, and secure server rooms.
Risk Analysis in Cybersecurity Example
Consider a mid-sized financial services company that identifies phishing attacks as a high-priority risk. Its cybersecurity risk assessment report shows frequent phishing attempts targeting employees. The company responds by:
- Mitigating the risk through employee awareness training and advanced email filtering tools.
- Transferring part of the risk by purchasing cyber insurance.
- Documenting residual risks that cannot be fully eliminated.
This example shows how risk management in cybersecurity is not about eliminating every risk, but about applying layered strategies to bring risk down to an acceptable level.
ALSO: Is Cybersecurity Hard to Learn? A Complete Analysis
Implementation and Monitoring
Designing a risk management plan in cybersecurity is only half the job. The real test lies in implementation and ongoing monitoring, where strategies become everyday practices that evolve with threats.
Implementing the Plan
Once risks are prioritized and controls selected, organizations must roll them out systematically:
- Deploy technical safeguards: Configure firewalls, enable encryption, and roll out multi-factor authentication across systems.
- Update policies and procedures: Align business processes with risk analysis findings, ensuring clear guidelines for employees.
- Train the workforce: Since human error remains a leading cause of breaches, regular training helps staff recognize phishing attempts and follow security protocols.
Continuous Monitoring
Cyber threats are dynamic, so defenses must be too. Using automated cybersecurity risk assessment tools, companies can monitor network traffic, detect anomalies, and generate alerts in real time. This proactive approach allows faster detection and containment of incidents before they escalate.
Key monitoring practices include:
- Performance Metrics: Tracking the number of incidents detected, response times, and compliance rates.
- Audits and Reviews: Conducting regular audits ensures that controls are effective and identifies areas needing improvement.
- Policy Updates: Revisiting and refining security rules based on new technologies, regulatory changes, or lessons from past incidents.
Building a Cycle of Improvement
Implementation and monitoring are not one-off tasks. Each cycle of monitoring feeds into the next cybersecurity risk assessment report, ensuring that risks are reevaluated, new vulnerabilities are addressed, and strategies remain effective. This creates a feedback loop where the organization becomes more resilient over time.
In practice, this stage is what transforms a static risk analysis into a living, adaptive framework for security.
Benefits of Cybersecurity Risk Analysis
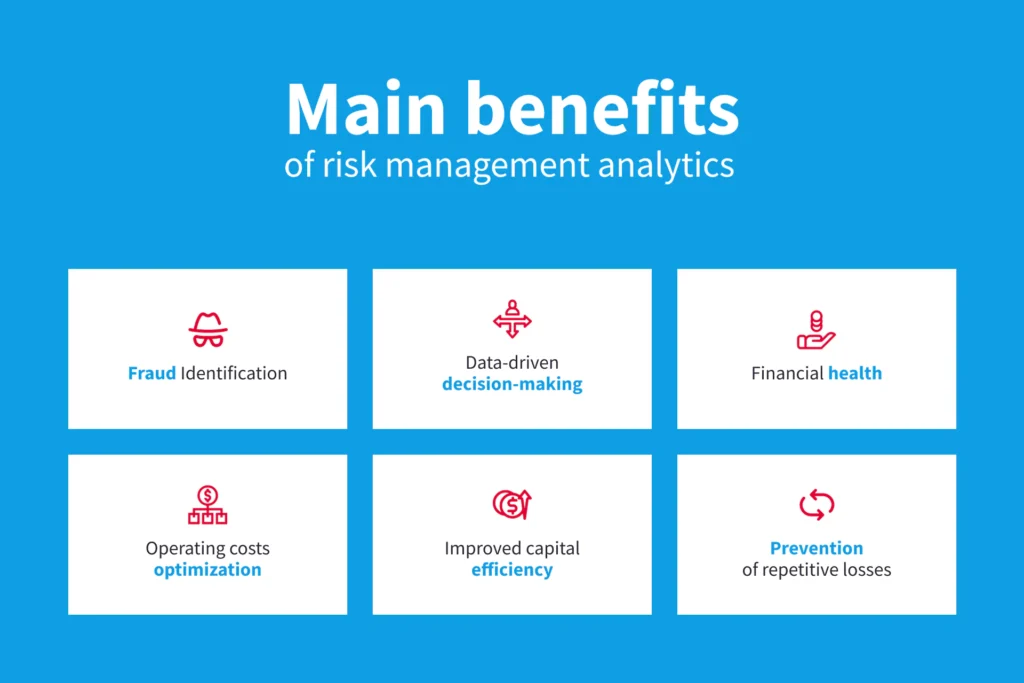
Investing in a structured cybersecurity risk assessment pays dividends beyond just preventing breaches. The insights from analysis help organizations save money, strengthen operations, and build trust with customers and regulators.
1. Long-Term Cost Reduction
By identifying vulnerabilities early, businesses can prevent costly incidents. The cost of implementing preventive controls is typically far less than the financial damage from a successful breach. A proactive approach also reduces downtime, ensuring continuous operations.
2. Informed Decision-Making
A well-documented cybersecurity risk assessment report equips executives with the data they need to allocate resources strategically. Instead of spreading budgets thin across all areas, organizations can focus on high-impact risks. This makes cybersecurity spending more efficient and justifiable to stakeholders.
3. Regulatory Compliance
Many industries, from healthcare to finance, mandate regular risk assessments. Conducting risk analysis helps companies stay compliant with standards like GDPR, HIPAA, or PCI DSS. Having structured processes, and in some cases, evidence generated by a cybersecurity risk assessment tool, ensures readiness for audits and reduces the likelihood of fines.
4. Stronger Organizational Awareness
Risk analysis fosters a culture of security. Employees gain a clearer understanding of their role in protecting assets, from recognizing phishing emails to following access control policies. This shared responsibility strengthens overall defenses.
5. Continuous Improvement
One of the less obvious but critical benefits is scalability. Once a process is established, it can be repeated and refined. Each cycle of analysis enhances the organization’s ability to adapt to new threats, ensuring long-term resilience.
In short, the importance of risk analysis in cybersecurity is not only in defending against today’s threats but in building a foundation for sustainable, secure growth.
SEE MORE: What Is Enterprise Risk Management (ERM)? Types, Pillars, Stakeholders
Challenges in Cybersecurity Risk Analysis
While the value of conducting a cybersecurity risk assessment is clear, organizations often encounter significant hurdles when putting theory into practice. These challenges range from limited resources to the complexity of today’s digital environments.
1. Resource Constraints
Small and mid-sized businesses frequently struggle with limited budgets and staff. Comprehensive risk analysis requires skilled professionals, specialized tools, and time, resources that many organizations cannot easily spare.
2. Technical Complexities
Modern IT environments are sprawling, with cloud platforms, remote workers, and third-party vendors creating new vulnerabilities. Integrating results from different cybersecurity risk assessment tools can be challenging, especially when systems are fragmented.
3. Emerging and Evolving Threats
Cybercriminals constantly adapt, using new techniques like AI-driven phishing or zero-day exploits. This dynamic landscape makes it difficult to keep a risk analysis current. An outdated cybersecurity risk assessment report may quickly lose relevance.
4. Compliance and Regulatory Pressure
Industries face evolving legal obligations, from data privacy regulations in the EU to sector-specific mandates in finance or healthcare. Aligning with multiple frameworks can be costly and confusing, particularly for organizations operating across regions.
5. Organizational Silos
Departments often operate independently, creating gaps in communication. For instance, IT may identify vulnerabilities, but without buy-in from finance or leadership, the necessary investments may not be approved. Misaligned priorities weaken the overall risk management in cybersecurity.
Overcoming these challenges requires a combination of leadership commitment, investment in skilled talent, and the adoption of frameworks that ensure consistency. Without this, even well-intentioned risk analysis efforts may fall short of delivering lasting protection.
Case Studies and Real-World Examples
The true impact of risk analysis becomes clear when looking at how different sectors apply it. These risk analysis in cybersecurity examples show how structured assessments and planning can turn vulnerabilities into stronger defenses.
Healthcare Sector: Protecting Patient Data
A large hospital network in West Africa conducted a cybersecurity risk assessment after a minor data breach involving patient records. The risk identification in cybersecurity revealed gaps in access controls and outdated systems.
By implementing stronger encryption, stricter authentication, and staff training, the hospital not only secured sensitive data but also ensured compliance with healthcare regulations. This proactive approach reduced exposure to fines and lawsuits.
Financial Services: Combating Phishing
A multinational bank faced repeated phishing campaigns targeting both staff and customers. Through detailed analysis, it identified phishing as a high-likelihood, high-impact threat in its cybersecurity risk assessment report.
The bank responded with advanced email filtering, customer education programs, and mandatory multi-factor authentication. As a result, phishing incidents dropped significantly, safeguarding customer accounts and maintaining the bank’s reputation.
Retail Business: Ransomware Recovery
A regional retail chain experienced a ransomware attack that disrupted operations and locked critical business data. Post-incident, the company used a structured cybersecurity risk assessment tool to evaluate vulnerabilities and prioritize fixes.
Actions included upgrading endpoint protection, deploying automated backups, and creating an incident response plan. These measures not only helped the retailer recover but also built resilience against future attacks.
Lessons Learned Across Industries
These case studies highlight a common theme: effective risk management in cybersecurity is not optional. Whether protecting patient data, financial assets, or retail operations, organizations that regularly conduct risk analysis can detect weaknesses early, respond faster to incidents, and build long-term trust with stakeholders.
Conclusion
The growing complexity of cyber threats makes risk analysis in cybersecurity a necessity, not a choice. From ransomware to insider threats, organizations face risks that can disrupt operations, drain finances, and damage reputations. By systematically identifying, evaluating, and prioritizing these risks, businesses create a roadmap for stronger defenses and smarter investments.
The importance of risk analysis in cybersecurity lies in its proactive nature. Rather than waiting for an incident to strike, companies use structured frameworks and tools to anticipate threats and reduce their impact. A well-prepared cybersecurity risk assessment report provides decision-makers with actionable insights, while modern cybersecurity risk assessment tools ensure the process remains efficient and repeatable.
As the case studies show, whether in healthcare, finance, or retail, effective risk analysis leads to tangible outcomes: fewer breaches, faster recovery, and greater stakeholder confidence. In practice, this means organizations that embed risk management in cybersecurity into their culture are better positioned to thrive in the digital economy.
Risk analysis is not just about preventing attacks; it is about enabling resilience. By committing to continuous evaluation and improvement, businesses can safeguard critical assets today while preparing for the threats of tomorrow.
FAQ
What are the 4 stages of risk analysis?
The four stages of risk analysis typically include:
Identification: Pinpointing potential threats and vulnerabilities within an organization’s systems.
Assessment: Evaluating the likelihood of each threat and its potential impact.
Mitigation: Implementing controls or strategies to reduce the risk to an acceptable level.
Monitoring: Continuously reviewing and updating risk findings to adapt to new threats and business changes.
Together, these stages ensure that risk analysis is not a one-time exercise but a continuous cycle.
What does a cybersecurity risk analyst do?
A cybersecurity risk analyst is responsible for evaluating and managing the security posture of an organization. Their role involves conducting cybersecurity risk assessments, preparing reports for leadership, recommending security controls, and ensuring compliance with frameworks like NIST or ISO 27001.
Analysts also monitor emerging threats and help design strategies to minimize the likelihood and impact of attacks, making them critical players in protecting both digital assets and business continuity.
What are the 5 C’s of cybersecurity?
The 5 C’s of cybersecurity are often cited as:
Change: Adapting to evolving threats and technologies.
Compliance: Meeting regulatory and industry requirements.
Cost: Balancing security investments against potential risks.
Continuity: Ensuring business operations remain resilient after an incident.
Coverage: Making sure defenses protect all areas of the IT environment, not just the most obvious ones.
These five principles guide organizations in maintaining a comprehensive and effective security strategy.
What are the three types of risk analysis?
The three main types of risk analysis in cybersecurity are:
Qualitative Risk Analysis: Uses subjective judgments, categorizing risks as high, medium, or low.
Quantitative Risk Analysis: Relies on numerical data and models to estimate financial impact and probability.
Semi-Quantitative Risk Analysis: Combines both approaches, applying numerical scoring to qualitative scales for a balanced view.
Each method has advantages depending on the size of the organization, the availability of data, and the nature of the risks being assessed.
