
Who Is a Penetration Tester? Roles, Skills, Salary, and How to Start
Who Is a Penetration Tester? Roles, Skills, Salary, and How to Start
A penetration tester, often referred to as an ethical hacker, plays an important role in modern cybersecurity. They simulate real-world attacks on systems, networks, and applications to uncover weaknesses before malicious hackers exploit them. With cyberattacks growing in scale and sophistication, organizations rely on penetration testers to translate technical risks into actionable fixes.
This guide explains what the role entails, how it differs from other security assessments, the tools and techniques involved, and what it takes to build a career in this field.

Start a Life-Changing Career in Cybersecurity Today
What a Penetration Tester Actually Does (and Why It Matters)
A penetration tester is a security professional hired to probe systems for vulnerabilities in a controlled, authorized way. Unlike automated scans that simply list flaws, pen testers validate, exploit, and demonstrate what attackers could achieve in practice.
Their work isn’t the same as red teaming, which emulates full-scale adversary campaigns, or vulnerability assessments, which provide broad but shallow scans. Pen testers focus on proving real impact, showing whether weaknesses could lead to stolen data, disrupted services, or compromised systems.
Inside most organizations, penetration testers sit within offensive security or application security teams. They work closely with defenders and governance experts, turning technical findings into business insights leadership can act on.
Penetration Testing vs. Other Security Assessments
It’s easy to confuse penetration testing with other forms of security testing, but the goals differ.
- Vulnerability assessments: Primarily automated scans that identify known flaws but don’t confirm whether they’re exploitable.
- Penetration tests: Controlled simulations that validate and exploit vulnerabilities to show business impact.
- Red team exercises: Long-term, stealthy campaigns designed to test detection and response capabilities.
- Purple teams: A collaborative blend where attackers and defenders work together in real time.
Organizations often combine these methods depending on maturity. For example, a company launching a new app may run a pen test, while a mature financial institution might add red and purple team exercises to stress-test defenses continuously.
RELATED: Cybersecurity Salary: A Comprehensive Guide
Core Workflow: How a Professional Pen Test Runs

Every professional pen test begins with scoping and rules of engagement. These agreements define which systems can be tested, the depth of testing, and safety protocols. With boundaries in place, testers typically follow five key phases:
- Reconnaissance – Collecting intelligence about the target through public data, network scans, or metadata leaks.
- Scanning – Using tools to identify vulnerabilities, open ports, and weak entry points.
- Exploitation – Attempting controlled attacks such as SQL injection or privilege escalation to prove a weakness is real.
- Post-Exploitation – Exploring what an attacker could do if access is maintained, from lateral movement to data exfiltration.
- Reporting – Delivering a clear document that outlines findings, their severity, and remediation steps in business language.
The process is designed to mimic real attackers without causing harm, making ethics and legality central to the profession.
Types of Pen Tests
Not all pen tests look the same. The scope varies depending on what systems or assets are most at risk:
- Web Applications – Testing for issues like SQL injection, cross-site scripting, and authentication flaws.
- Mobile Applications – Checking for insecure storage, weak encryption, and unsafe server interactions.
- Networks and Wireless – Examining firewalls, routers, and Wi-Fi setups for misconfigurations or outdated protocols.
- Cloud Environments – Assessing access controls, storage configurations, and identity management within AWS, Azure, or Google Cloud.
- Containers and DevOps Pipelines – Evaluating Docker/Kubernetes configurations and CI/CD pipelines for leaks or code injection risks.
- APIs – Probing endpoints for excessive data exposure, poor authentication, and injection vulnerabilities.
- Physical and Social Engineering – Simulating phishing, pretexting, or even physical intrusion where authorized.
By tailoring tests to specific environments, organizations gain a realistic picture of their most critical vulnerabilities.
Tools and Techniques That Matter in Practice
A penetration tester’s toolkit is broad, but effective use depends on skill and creativity.
- Reconnaissance: Nmap for mapping networks, Shodan for exposed devices, theHarvester for gathering emails and domains.
- Scanning: Nessus, Qualys, or OpenVAS for identifying vulnerabilities at scale.
- Web Testing: Burp Suite and OWASP ZAP for intercepting traffic and uncovering hidden flaws.
- Exploitation: Metasploit for executing known exploits; custom scripts for unique cases.
- Post-Exploitation: Tools like Mimikatz or BloodHound for privilege escalation and mapping Active Directory.
Automation speeds up discovery, but manual testing uncovers what machines miss—such as logic flaws in payment systems or workflow bypasses. This blend of automation and human intuition is what makes penetration testing both a science and an art.
READ ALSO: Cybersecurity vs Devops Salary: Everything You Need to Know
Skills, Certifications, and a Practical Entry Path
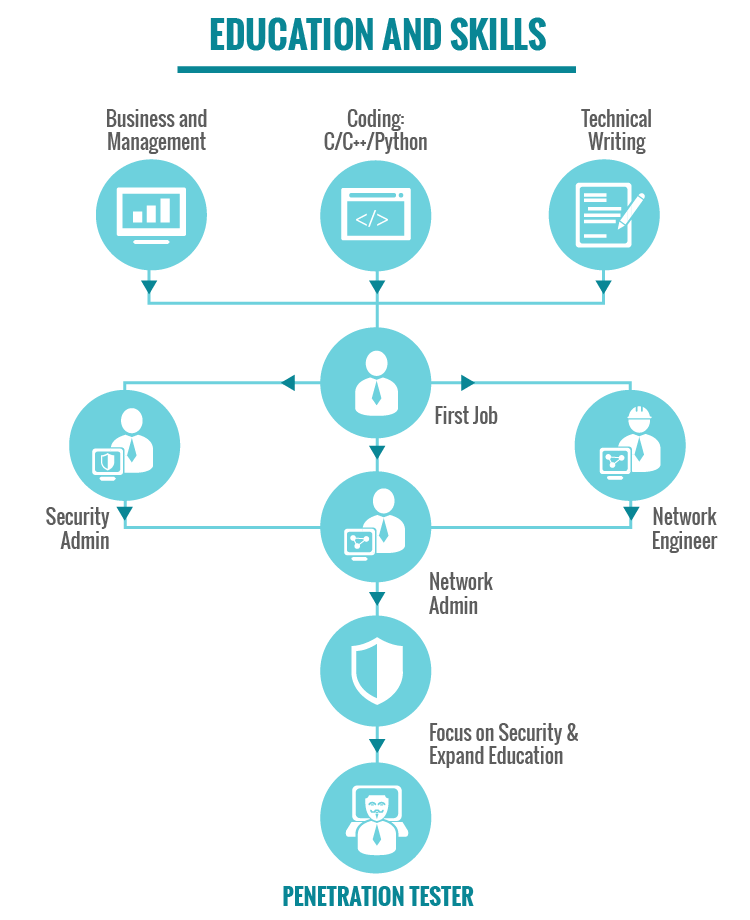
Penetration testing demands both technical mastery and soft skills.
- Technical foundations: Networking, operating systems, and scripting (Python, Bash, PowerShell).
- Soft skills: Clear reporting, critical thinking, and the ability to explain risks to non-technical stakeholders.
- Practice routes: Labs, Capture the Flag (CTF) competitions, platforms like Hack The Box and TryHackMe, or bug bounty programs.
Certifications help validate skills:
- OSCP – Highly regarded for proving hands-on capability.
- CEH – Broad coverage of hacking techniques.
- CompTIA PenTest+ / GIAC GPEN – Solid intermediate-level options.
A simple 90-day starter plan might include: building a home lab, practicing beginner CTFs, documenting findings in report format, and working toward a starter certification.
Careers, Compensation, and Hiring Expectations
Pen testers can start as junior testers or security analysts and advance to senior roles, red team leads, or consultants. Some pivot into adjacent fields like incident response, security architecture, or threat intelligence.
What employers look for: evidence of practical skill, a structured methodology, and strong reporting ability. A candidate with hands-on lab work and polished documentation often outshines someone with theory alone.
Salary outlook:
- Entry-level: $65,000–$85,000
- Mid-level: $95,000–$120,000
- Senior/lead: $130,000–$150,000+
Demand consistently outpaces supply, making penetration testing one of the more lucrative paths in cybersecurity.
Limits of Pen Testing, and How Teams Get More Value
Despite its importance, penetration testing has limits. Tests are time-bound and scoped, meaning some vulnerabilities may remain undiscovered. Live exploitation also carries a small risk of system disruption, and findings can quickly become outdated as software and threats evolve.
Organizations get the most value when pen testing is part of a continuous security strategy. That means combining it with vulnerability management, scheduling follow-up tests after remediation, and aligning results with broader risk management frameworks. Done right, pen testing becomes a catalyst for measurable, ongoing improvements rather than a one-off checkbox exercise.
SEE MORE: What Is Blockchain Security? A Comprehensive Breakdown
What’s Next: AI-Assisted Testing, Cloud-First, and Continuous Security
The field is shifting quickly:
- AI and automation are speeding up reconnaissance and analysis, though human oversight remains essential.
- Cloud and IoT testing are rising in importance as organizations migrate workloads and expand attack surfaces.
- APIs and CI/CD pipelines are emerging as critical areas requiring specialized testing.
- Continuous validation is replacing annual tests, with security integrated directly into DevOps pipelines.
- Advanced simulations involving phishing, insider threats, and multi-stage campaigns are becoming more common to match the tactics of real-world adversaries.
These trends will not replace human testers but will augment them, allowing professionals to focus on creativity, strategy, and business alignment.
Is Pen Testing Right for You?
Penetration testing is challenging, dynamic, and deeply rewarding. It’s a career for problem-solvers who thrive on uncovering hidden flaws and who can think like attackers while defending like guardians. Success requires technical skill, ethical responsibility, and the drive to keep learning as threats increase.
For aspiring professionals, the path forward is clear: start small, build hands-on experience, pursue certifications that prove skill, and join the cybersecurity community. With organizations worldwide facing growing cyber risks, the demand for skilled penetration testers isn’t slowing down. If you’re motivated to turn curiosity into defense, this role offers not just a job but a future-proof career.
FAQ
What degree do you need for penetration testing?
There’s no single degree required to become a penetration tester. Many professionals come from computer science, information technology, or cybersecurity backgrounds, but others enter the field through hands-on training, labs, and certifications.
Employers often value practical skills and proof of ability, such as completing the OSCP, over formal degrees. That said, having a bachelor’s in cybersecurity or related fields can open more doors, especially in large enterprises or government roles.
Is penetration testing a good career?
Yes, penetration testing is widely considered a strong career choice. It combines technical challenge, creativity, and high demand across industries. The role is well-paid, offers opportunities to specialize (web, cloud, red teaming), and provides career progression into senior security, consulting, or leadership roles. With cyberattacks increasing globally, penetration testers enjoy both job security and diverse career paths.
How long does it take to learn pentesting?
The timeline depends on your starting point. Someone with a solid IT or networking background may become job-ready in 6 to 12 months with focused training, labs, and certifications.
For complete beginners, the journey might take closer to 18–24 months, especially if building foundational knowledge in networking, operating systems, and coding. Continuous learning is key; new tools and attack methods emerge regularly, so even seasoned testers are always updating their skills.
Does penetration testing require coding?
Yes, but not at an advanced software engineering level. Pen testers benefit from knowing scripting languages like Python, Bash, or PowerShell to automate tasks, build custom exploits, or adapt tools.
Understanding how applications are coded also helps identify logic flaws or injection points. While you can start without deep coding knowledge, progressing to mid-level and senior roles typically requires at least intermediate programming and scripting skills.
