
What Is Third-Party Vendor Risk Management (TPRM)? Complete Guide
What Is Third-Party Vendor Risk Management (TPRM)? Complete Guide
Companies rarely operate in isolation when it comes to business operations. When you talk of logistics provision, cloud platform, or outsourced IT team, third-party vendors now form a critical part of daily operations. But with that reliance comes a new wave of risks, ranging from cyber threats and data leaks to compliance failures and reputational damage.
This is where Third-Party Vendor Risk Management (TPRM) comes in.
TPRM refers to the structured process of identifying, evaluating, mitigating, and monitoring the risks associated with external vendors or service providers. The goal is simple but crucial: protect your organization from the vulnerabilities these external relationships may introduce, without slowing down growth or innovation.
Think of it this way—when your vendors handle sensitive data, access internal systems, or support critical services, their weaknesses become your exposure. A data breach at their end could lead to legal trouble, customer churn, or financial loss at yours.
And the stakes are rising. In recent years, the world has witnessed a sharp rise in third-party related data breaches. Regulatory bodies like GDPR (EU), NDPR (Nigeria), and CCPA (California) are tightening their grip, requiring companies not only to manage their internal risks but also to extend that governance to third-party vendors.
Organizations that implement a robust TPRM program gain more than protection; they build resilience. With the right tools and processes in place, businesses can:
- Reduce the chance of vendor-related cybersecurity incidents.
- Ensure compliance with evolving data protection laws.
- Maintain operational continuity during third-party disruptions.
- Protect their brand reputation from the fallout of vendor failures.
- Gain a competitive edge by demonstrating due diligence and trustworthiness.

Start a Life-Changing Career in Cybersecurity Today
Understanding Third-Party Relationships
Before you can manage third-party risk, you must first understand who qualifies as a third party and why these relationships matter.
At its core, a third party is any external entity your organization partners with to deliver a product, service, or function. This could be a cloud provider like AWS, a payroll service, a marketing agency, or even a logistics partner. But the risk doesn’t stop at direct vendors. Today’s supply chains are layered, making the third-party ecosystem more complex than ever.
Here’s how these relationships break down:
1. Upstream vs Downstream Entities
- Upstream entities are the providers you rely on, think software vendors, payment processors, or raw material suppliers. These partners plug directly into your operations and can impact data flow, compliance, and availability.
- Downstream entities are your resellers, distributors, or partners that bring your products and services to market. If they fail to deliver or compromise customer trust, it reflects directly on your brand.
2. Non-Contractual Entities
Some third parties exist outside of direct contractual relationships but still affect your business. These might be subcontractors hired by your primary vendor. Even if you don’t engage them directly, their failures (e.g. in security, delivery, or ethics) can ripple up to you.
For example, if your outsourced IT provider uses a freelance developer who leaves security vulnerabilities in the code, your organization could still face the breach.
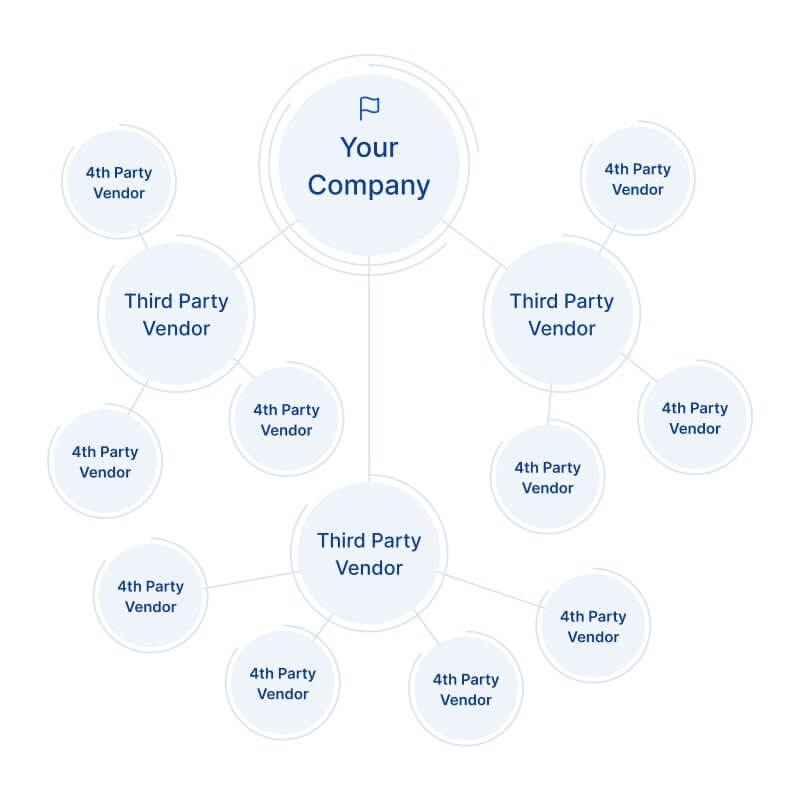
3. Fourth Parties and Nth-Party Risk
The fourth-party conundrum refers to the vendors of your vendors, the ones buried deeper in the supply chain. You might not even know they exist, yet they could be managing, processing, or storing your data.
If your HR software vendor uses a third-party API for payroll processing, and that service gets breached, your data could still be exposed, even though you had no direct contact with the breached party.
4. Why Understanding These Layers Matters
Each layer of this ecosystem introduces unique vulnerabilities. Mismanaging these relationships can lead to:
- Cybersecurity breaches.
- Regulatory violations.
- Operational disruptions.
- Brand and reputation damage.
And because third-party relationships are often fluid and growing, a static vendor list isn’t enough. Organizations need real-time visibility into who their vendors are, what data they handle, and which fourth parties are lurking in the background.
Every third-party relationship is a potential entry point for risk. Understanding the full scope, upstream, downstream, and beyond, is the first and most vital step in managing third-party vendor risk.
RELATED: Vendor Risk Management (VRM) in 2025
The Significance of Third-Party Risk Management
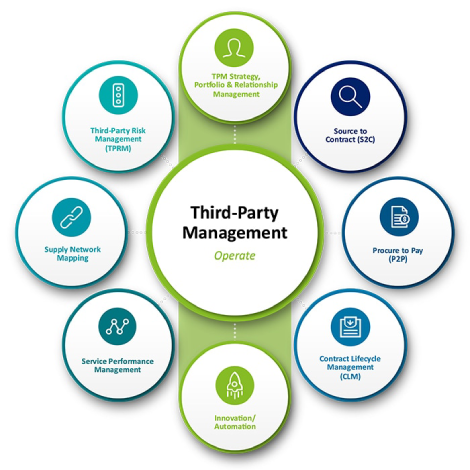
As organizations become more digitized, distributed, and dependent on vendors, the risks introduced by third parties are no longer theoretical, they’re tangible, measurable, and in many cases, already inside the perimeter.
That’s why Third-Party Risk Management (TPRM) is not just a technical or compliance function, it’s a strategic necessity.
Here’s why TPRM deserves a permanent seat at the leadership table:
1. Protecting Cybersecurity Posture
Third-party vendors often have access to internal systems, APIs, cloud environments, or sensitive customer data. If their cybersecurity is weak, they can become the backdoor that attackers use to breach your defenses.
Real-world example: In 2013, a Target HVAC vendor was compromised, allowing attackers to infiltrate Target’s network and steal 40+ million customer records. This wasn’t a technical failure inside Target; it was a third-party security gap.
TPRM helps by enforcing:
- Security assessments before onboarding.
- Continuous monitoring post-contract.
- Minimum cybersecurity standards in contracts.
2. Meeting Regulatory and Legal Requirements
Regulations like GDPR, NDPR, HIPAA, and CCPA don’t stop at your organization’s border; they extend to every third party you share data with.
In other words, if your vendor mishandles user data, you could still be fined or publicly penalized.
TPRM ensures:
- Vendors follow data protection laws.
- Risk assessments are documented.
- Vendor compliance is auditable.
By proactively managing vendor compliance, organizations reduce their legal exposure and protect themselves from high-cost lawsuits or regulatory sanctions.
3. Ensuring Operational Resilience
A vendor’s failure, whether due to downtime, financial collapse, or internal disruption, can interrupt your services. In industries like finance, healthcare, or education, these disruptions aren’t just inconvenient; they’re catastrophic.
TPRM contributes to business continuity by:
- Assessing a vendor’s financial and operational health.
- Reviewing business continuity plans.
- Creating backup vendor strategies.
4. Safeguarding Brand Reputation
Your customers don’t know the name of your payroll software vendor or your outsourced marketing firm. But when something goes wrong, you are the brand they blame.
A third-party service outage or data breach can damage trust, erode brand equity, and trigger public backlash. TPRM reduces reputational risk by ensuring:
- Only trusted, verified vendors are used.
- Vendors meet ethical and performance standards.
- You have an incident response plan involving all third parties.
5. Aligning Third Parties with Strategic Goals
TPRM is useful for choosing the right vendor relationships, without limits.
A mature TPRM program allows your company to:
- Partner with vendors who enhance your strengths.
- Avoid partnerships that introduce misalignment or unnecessary risk.
- Create value-driven, secure, and scalable vendor ecosystems.
READ ALSO: What Is Enterprise Risk Management (ERM)? Types, Pillars, Stakeholders
Types of Risks Introduced by Third Parties
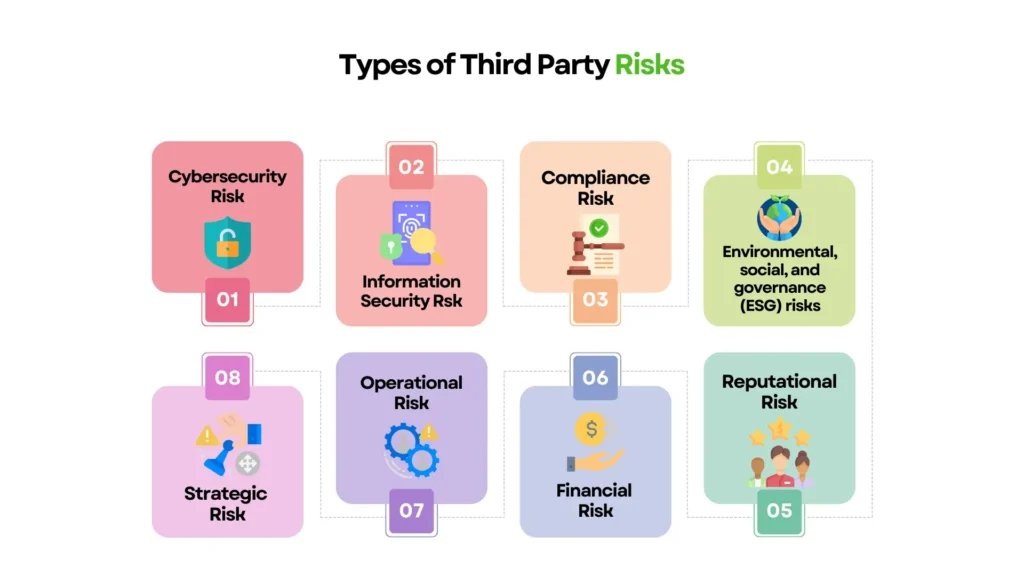
Working with third-party vendors brings undeniable benefits, cost savings, efficiency, and access to specialized expertise. But every new vendor relationship also introduces new risk vectors that can threaten your organization’s security, reputation, and bottom line.
Here are the major categories of risk that a Third-Party Risk Management (TPRM) program is designed to identify and control:
1. Cybersecurity Risk
This is the most high-profile and immediate concern. When a third party has access to your network, applications, or data, any weakness in their systems becomes a direct threat to yours.
Risks include:
- Malware or ransomware infections introduced via vendor systems.
- Weak authentication or encryption on their side.
- Breaches caused by social engineering or phishing attacks targeting vendors.
Example: The infamous SolarWinds breach exposed thousands of organizations because hackers targeted the software vendor’s update system, a classic third-party attack vector.
2. Operational Risk
Third parties often deliver critical services. If they experience delays, outages, or mismanagement, your operations suffer.
Risks include:
- Downtime in outsourced IT services.
- Failure to meet service-level agreements (SLAs).
- Poor quality control in manufacturing or logistics partners.
Operational risks can disrupt customer service, delay projects, or even halt business continuity in severe cases.
3. Legal, Regulatory, and Compliance Risk
Every vendor you engage must comply with the same regulations you do, especially if they handle sensitive data or operate in a regulated industry.
Risks include:
- Violations of data protection laws (GDPR, NDPR, HIPAA, etc.).
- Failure to report breaches within required timelines.
- Lack of required certifications or licenses.
If a vendor is non-compliant, your organization could be liable—even if you followed all rules internally.
4. Reputational Risk
Your brand reputation is only as strong as your weakest vendor.
Risks include:
- Data breaches that make headlines—even if they happened to a vendor.
- Vendor misconduct (fraud, corruption, unethical behavior).
- Service delivery failures that impact your customers.
One misstep by a partner can undo years of brand trust and customer loyalty.
5. Financial Risk
If your vendor is in financial distress or mismanages funds, it could affect your own financial planning or service delivery.
Risks include:
- Unexpected price hikes or renegotiations.
- Bankruptcy or insolvency leading to service gaps.
- Inability to scale alongside your business needs.
TPRM helps assess vendor financial stability and plan contingencies.
6. Strategic Risk
This arises when a vendor’s capabilities, direction, or limitations conflict with your organization’s long-term strategy.
Risks include:
- Misalignment in values or technology standards.
- Inflexibility to support future goals or scaling.
- Choosing a vendor that fails to innovate or adapt.
Strategic risk is harder to quantify but just as critical to long-term resilience.
By identifying and categorizing these risks, organizations can apply targeted controls, negotiate stronger contracts, and choose partners that enhance, rather than endanger, the business.
SEE MORE: Cybersecurity vs Cloud Computing: A Comprehensive Comparison
Why Invest in Third-Party Risk Management?
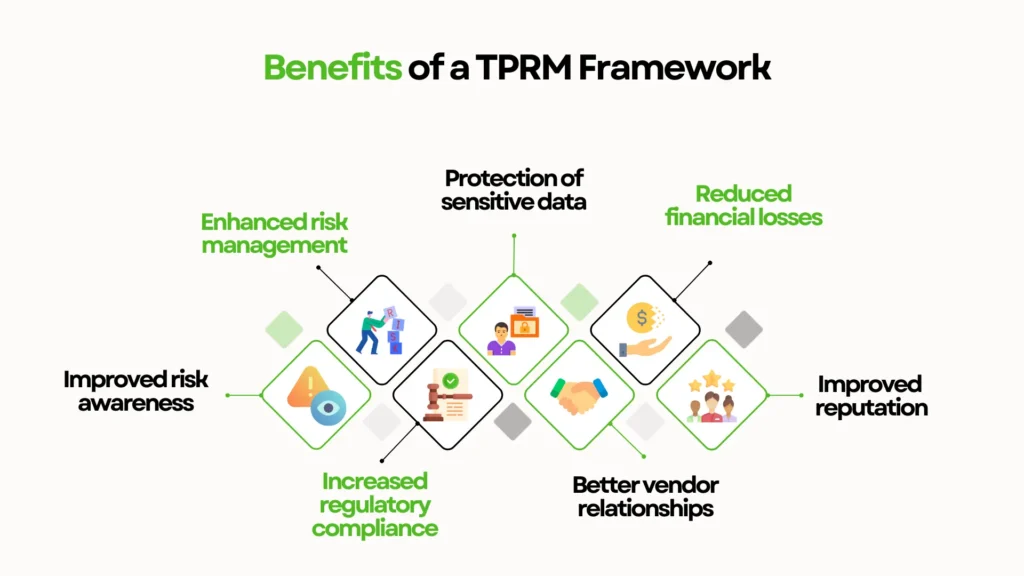
At a glance, managing vendor risks might seem like a technical or legal formality, but in reality, it’s a high-leverage investment that protects your organization on multiple fronts.
Here’s why leading organizations are investing heavily in Third-Party Risk Management (TPRM), and why you should too.
1. Cost Savings and Risk Avoidance
Data breaches tied to vendors are not just embarrassing, they’re expensive. The average cost of a breach involving a third party can run into millions, factoring in legal fees, regulatory fines, forensic investigations, and lost customer trust.
TPRM doesn’t just help you prevent these incidents. It saves you money by:
- Identifying risky vendors before they cause damage.
- Streamlining onboarding and reducing due diligence redundancies.
- Preventing operational disruptions that could halt revenue.
Think of TPRM as insurance, but smarter. You’re not just reacting to risk; you’re actively minimizing it.
2. Regulatory Compliance and Legal Defense
With stricter regulations like GDPR, NDPR, CCPA, and PCI-DSS, organizations are now responsible for their vendors’ mistakes, especially when it comes to data handling and breach notifications.
TPRM helps demonstrate:
- Due diligence: That you assessed the vendor before sharing data.
- Ongoing oversight: That you continue to monitor their security and compliance.
- Documented governance: That you have policies, contracts, and audit trails in place.
This not only avoids fines but strengthens your legal defense if a breach occurs.
3. Improved Cybersecurity Posture
Most cybersecurity programs focus internally, firewalls, endpoint protection, and employee training. But if your vendor is compromised, none of that will matter.
TPRM extends your cybersecurity perimeter by:
- Requiring vendors to meet minimum standards.
- Conducting security assessments or requiring certifications (e.g., ISO 27001).
- Monitoring vendor networks for vulnerabilities and breaches.
Instead of plugging holes after an incident, TPRM helps you prevent the leaks altogether.
4. Strategic Alignment and Scalability
Not all vendors are equal. Some are critical to your operations; others are replaceable. TPRM helps you evaluate vendors not just by what they offer, but by how well they align with your strategic goals and risk appetite.
This ensures:
- The right vendors are onboarded for the right reasons.
- You’re not scaling with insecure or non-compliant partners.
- Your vendor ecosystem evolves in step with your business.
5. Reputation Protection and Stakeholder Trust
Customers, partners, and investors care about your brand’s reliability. One public failure, like a vendor-related breach or scandal, can undo years of reputation-building.
TPRM helps build a defensible brand by:
- Holding vendors accountable to ethical and operational standards.
- Responding swiftly to incidents through prepared contingency plans.
- Showing stakeholders you take risk seriously, even beyond your walls.
In an era of cancel culture and fast news cycles, trust is your currency. TPRM helps you protect it.
READ: HR vs Cybersecurity: Which Career Path Offers More Opportunity in 2025?
Implementing a Third-Party Risk Management Program
Establishing a Third-Party Risk Management (TPRM) program is more than just a checkbox exercise. It requires a structured, step-by-step framework that integrates risk awareness into every stage of the vendor lifecycle, from onboarding to offboarding.
Whether you’re building from scratch or strengthening an existing process, here’s how to implement a TPRM program that actually works:
Step 1: Define Your TPRM Framework
Start by laying a solid foundation:
- Clarify your objectives: Is your priority compliance? Operational resilience? Cybersecurity?
- Establish governance: Assign ownership across departments, IT, Legal, Procurement, Compliance, and create a centralized risk team or steering committee.
- Document your policies: Define how vendors are selected, assessed, monitored, and offboarded.
Your framework is the blueprint. Without it, risk management becomes reactive instead of proactive.
Step 2: Identify and Categorize Vendors
Not all vendors pose the same level of risk. Start by:
- Creating an inventory of all third-party relationships.
- Categorizing vendors based on:
- Access to sensitive data.
- Criticality to operations.
- Regulatory exposure.
- Access to sensitive data.
For example, your cloud storage provider is likely high risk, while a coffee supply vendor might be low risk.
This categorization helps you prioritize resources and tailor your assessments accordingly.
Step 3: Conduct Risk Assessments
Once vendors are categorized, perform thorough evaluations:
- Use security questionnaires, audits, and external tools like security ratings.
- Assess their:
- Cybersecurity controls.
- Regulatory compliance.
- Financial health.
- Business continuity plans.
- Cybersecurity controls.
Risk assessment shouldn’t be a one-time task. It should happen before onboarding and regularly after, especially if their services or risk profile changes.
Step 4: Develop and Apply Risk Treatment Plans
When risks are identified, don’t just document them, act on them:
- Set expectations for risk remediation.
- Negotiate stronger contract terms.
- Require certifications (e.g., SOC 2, ISO 27001).
- Replace vendors who pose unacceptable risk.
All actions should be logged for transparency and to satisfy audit requirements.
Step 5: Monitor and Review Continuously
TPRM isn’t a “set it and forget it” system.
You need tools that allow for:
- Ongoing monitoring of vendor cybersecurity posture, compliance status, and financial health.
- Automated alerts when risks increase (e.g., a new breach or public controversy).
- Regular reviews and reassessments tied to contract renewals or key milestones.
This continuous loop is what keeps your program agile and responsive.
Step 6: Train Internal Teams
Third-party risk touches multiple departments. Make sure your internal stakeholders:
- Know how to report concerns or incidents.
- Understand the importance of vendor compliance.
- Are equipped to manage vendor relationships securely.
TPRM training ensures that risk awareness is part of your company culture—not just a siloed checklist in procurement.
Step 7: Build Strong Vendor Relationships
A successful TPRM program is not adversarial, it’s collaborative.
Foster open communication with vendors by:
- Sharing expectations early.
- Providing guidance on meeting compliance goals.
- Encouraging transparency around incidents and improvements.
When vendors feel like partners, not liabilities, they’re more likely to uphold your standards.
SEE: Accounting vs Cybersecurity: Everything You Need to Know
Creating a Vendor Management Policy
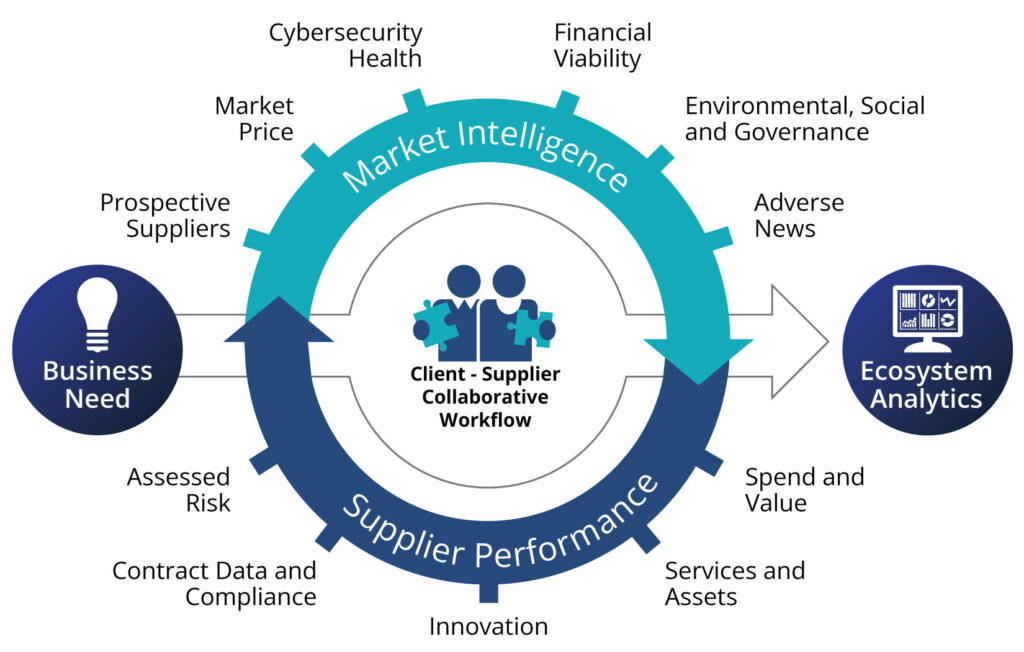
A Vendor Management Policy is not just paperwork; it’s the operating manual for how your organization manages external relationships. Without it, third-party oversight becomes reactive, inconsistent, and risky.
This policy creates a standardized approach to how you select, onboard, monitor, and offboard vendors, while ensuring regulatory compliance, data protection, and operational integrity.
Here’s how to build an effective, enforceable Vendor Management Policy:
1. Define the Policy’s Purpose and Scope
Start by clearly stating:
- Why this policy exists (e.g., to mitigate risk, ensure compliance, protect data).
- Who it applies to (e.g., all departments, all vendors).
- What types of vendor relationships it covers, IT, logistics, cloud providers, freelancers, etc.
A well-defined scope keeps your team aligned and prevents ambiguity.
2. Establish Vendor Selection Criteria
Not all vendors are created equal. Your policy should outline who qualifies as an acceptable vendor.
Criteria may include:
- Financial stability and reputation.
- Regulatory compliance history.
- Cybersecurity posture and certifications (e.g., SOC 2, ISO 27001).
- Capacity to meet SLAs and scale with your organization.
By screening early, you reduce long-term risk and avoid costly onboarding mistakes.
3. Outline the Due Diligence Process
Before any contract is signed, your organization must assess the vendor.
This section should detail:
- The type of due diligence required based on risk category.
- Tools or assessments used (questionnaires, security ratings, background checks).
- Who performs the due diligence (procurement, legal, IT).
Make sure your policy scales, low-risk vendors shouldn’t go through the same checks as high-risk ones.
4. Detail Risk Assessment and Risk Response Procedures
Your policy should describe how vendor risks are:
- Identified (during onboarding and ongoing monitoring).
- Categorized (e.g., low, medium, high risk).
- Mitigated (e.g., by requiring remediation, limiting access, or rejecting the vendor).
Include thresholds that trigger remediation plans, contract reviews, or escalations to leadership.
5. Define Ongoing Monitoring Requirements
TPRM doesn’t end at onboarding.
This part of the policy should establish:
- Monitoring frequency (e.g., quarterly for high-risk vendors).
- KPIs and metrics to track vendor performance and risk.
- Triggers for re-assessment (e.g., breach notification, poor SLA performance).
Tools like automated risk platforms can simplify this step.
6. Include Contract Management Guidelines
This section ensures every vendor contract contains the necessary protections, such as:
- Data privacy and security obligations.
- Right to audit and monitor.
- Breach notification timelines.
- Termination clauses in case of non-compliance.
Legal and compliance teams should review all contracts using a shared checklist based on this policy.
7. Establish Roles and Accountability
Who’s responsible for enforcing this policy? Define roles across:
- Procurement
- Legal
- Risk and Compliance
- IT
- Business Unit Owners
Clear accountability eliminates confusion and ensures follow-through.
8. Plan for Incident Response and Contingency
Vendors may still fail despite your best efforts. Your policy should outline:
- How incidents involving vendors are managed.
- Escalation paths and communication plans.
- Steps to activate contingency vendors or switch providers.
This ensures business continuity and rapid recovery when needed.
By developing a clear, actionable Vendor Management Policy, your organization lays the groundwork for consistent and secure vendor governance. It becomes your first line of defense, ensuring every third-party relationship is strategic, compliant, and controlled.
MORE: What Coding Language is Best for Cybersecurity?
How to Evaluate Third Parties
Before a vendor gets access to your systems, data, or customers, you need to know one thing: Can they be trusted?
Evaluating third-party vendors is a critical step in any TPRM program. It ensures that the vendors you choose will not expose your organization to unnecessary risks, whether through negligence, poor security, or financial instability.
Here’s a structured approach to evaluating third parties before and after they’re onboarded:
1. Set Clear Evaluation Criteria
Start by defining what matters most to your organization. These criteria should align with:
- Your industry’s compliance requirements.
- Your cybersecurity framework.
- Your operational expectations.
Typical evaluation areas include:
- Security controls and certifications.
- Data protection practices.
- Financial health and credit history.
- Regulatory compliance status.
- Service delivery reputation.
By standardizing your criteria, you reduce bias and ensure fairness across all vendors.
2. Conduct Due Diligence
Before signing anything, dig deep. Gather information through:
- Vendor questionnaires (covering security, legal, and financial areas).
- Review of publicly available information (e.g., past breaches or lawsuits).
- Risk ratings from third-party platforms.
- Background checks and reference calls.
Your goal is to understand:
- How the vendor handles risk.
- Whether they’ve had previous incidents.
- If they meet your baseline requirements.
For high-risk vendors, deeper evaluations (e.g., audits or site visits) may be necessary.
3. Assess Cybersecurity Posture
Since most third-party risks are now digital, evaluating cybersecurity is non-negotiable.
Key areas to check:
- Use of encryption (in transit and at rest).
- Access controls and authentication protocols.
- Incident response readiness.
- Past history of breaches.
- Independent certifications like ISO 27001, SOC 2, or NIST alignment.
You can also use automated threat intelligence tools to analyze their external risk footprint (e.g., exposed ports, phishing domains, expired certificates).
4. Review Legal and Regulatory Compliance
If the vendor is handling data, especially personal, financial, or healthcare-related, ensure they comply with:
- GDPR (EU)
- NDPR (Nigeria)
- HIPAA (U.S. healthcare)
- PCI-DSS (for payment processors)
Ask to see audit reports, data protection policies, or proof of breach notification processes. Non-compliance here could result in fines for your company.
5. Evaluate Financial and Operational Health
If a vendor goes bankrupt, your services could go down with them. Assess their:
- Financial statements (if public).
- Credit ratings or D&B scores.
- Employee capacity to handle workload.
- Business continuity plans and SLAs.
This ensures they have the resources to support your organization long-term.
6. Get References and Customer Feedback
Ask for references from other clients in your industry or similar size. You’ll learn more from real-world experiences than any datasheet.
Ask:
- How quickly does the vendor respond to issues?
- Have there been any service outages?
- Would you recommend them?
This qualitative feedback often reveals red flags hidden behind polished sales decks.
7. Monitor Performance Over Time
Evaluation doesn’t end after onboarding. Maintain ongoing visibility through:
- Performance reviews (quarterly or annually).
- Automated alerts from security platforms.
- Contract compliance checks.
- Incident tracking dashboards.
Risk profiles change. A vendor who was secure last year might be vulnerable today.
MORE READ: CompTIA Security Vs Google Cybersecurity Certification
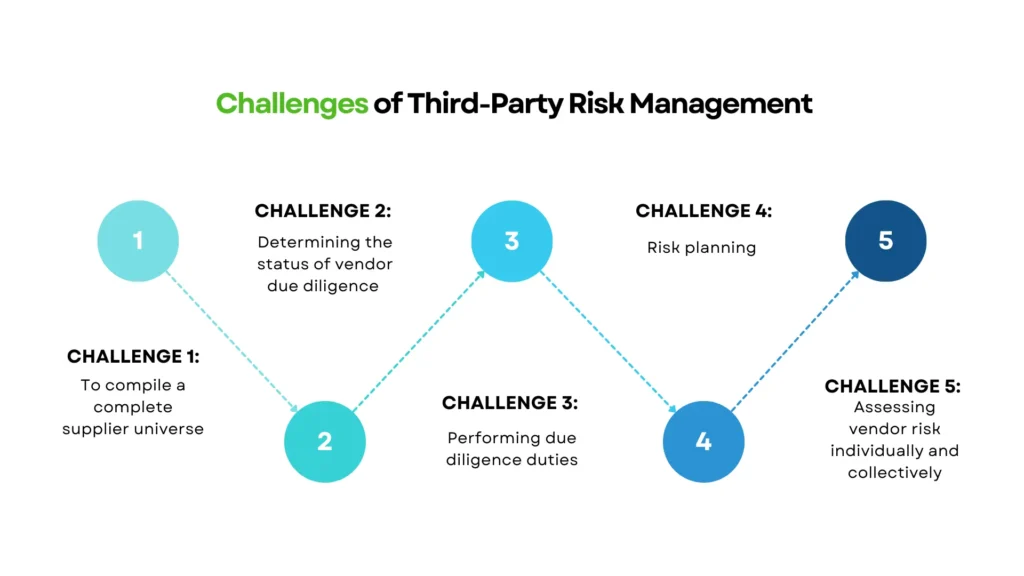
Common Challenges of Third-Party Risk Management
Third-Party Risk Management (TPRM) is essential, but it’s far from easy. As organizations grow, so do their vendor networks, risk exposure, and regulatory responsibilities. This creates a complex web of risks that can’t be managed with spreadsheets or surface-level audits alone.
Here are the most common challenges organizations face when trying to manage third-party risks, and how to address them:
1. Complex Vendor Ecosystems
Modern businesses engage with dozens (sometimes hundreds) of vendors, contractors, and SaaS providers. Add subcontractors and fourth parties into the mix, and visibility becomes nearly impossible.
The challenge: Without a centralized view of your entire vendor ecosystem, it’s difficult to understand where the real risks lie.
Solution: Use TPRM platforms that map your vendor relationships, including fourth parties, and give you real-time insights across your entire network.
2. Inconsistent Risk Assessments
When different departments use different methods to evaluate vendors, the result is scattered data and unpredictable decision-making.
The challenge: One vendor might go through a strict security audit, while another slips through with a one-page form.
Solution: Standardize risk assessment templates and workflows across the organization. Define what’s required based on risk tiers (low, medium, high).
3. Changing Regulatory Landscape
From GDPR and NDPR to HIPAA and CCPA, the list of data protection laws keeps growing. Each law has its own requirements—and they change frequently.
The challenge: Staying up to date and ensuring vendors remain compliant under new rules.
Solution: Establish a compliance monitoring system that flags regulatory changes and automatically prompts re-assessments or contract updates when necessary.
4. Limited Visibility into Fourth Parties
Many breaches don’t come from your direct vendors—they come from their vendors (fourth parties), whom you didn’t vet and don’t control.
The challenge: You’re legally and reputationally exposed to risks that may not even be on your radar.
Solution: Require third parties to disclose their key subcontractors and extend your monitoring practices to high-impact fourth parties using automated discovery tools.
5. Manual and Slow Processes
Traditional TPRM often relies on spreadsheets, back-and-forth emails, and siloed tools. This slows down onboarding, risk scoring, and remediation.
The challenge: By the time you complete due diligence, the vendor might already be active in your systems.
Solution: Automate vendor assessments, security questionnaires, and approval workflows with dedicated TPRM software. Speed shouldn’t come at the cost of security.
6. Low Engagement from Vendors
Some vendors resist security reviews or are slow to respond to risk questionnaires—especially smaller firms without dedicated compliance teams.
The challenge: Without cooperation, you can’t complete your assessments or track remediation.
Solution: Educate vendors on why TPRM matters. Use contract clauses to require cooperation and consider offering shared portals for easier collaboration.
7. Lack of Internal Coordination
Risk management touches many departments, legal, compliance, procurement, IT, but if those teams aren’t aligned, the program breaks down.
The challenge: Gaps in communication can lead to duplicate work, missed risks, or unapproved vendors slipping through.
Solution: Create a cross-functional TPRM committee, define roles and responsibilities, and use a single platform to unify vendor oversight.
8. Limited Budget and Resources
TPRM teams are often small, yet expected to manage a growing number of vendors with increasing scrutiny.
The challenge: It becomes impossible to scale assessments or monitoring with limited staff.
Solution: Focus first on critical vendors and automate as much of the process as possible. Prioritize risk-based efforts and prove ROI to justify resource expansion.
What Features Should I Look For in a TPRM Platform?
Choosing the right Third-Party Risk Management (TPRM) platform is a game-changer. The right solution doesn’t just help manage risks—it can streamline workflows, boost visibility, and keep your organization ahead of regulatory and cyber threats.
Here are the essential features every strong TPRM platform should have:
1. Automated Risk Assessment Tools
A great platform simplifies the risk assessment process with:
- Pre-built questionnaires aligned with industry standards (e.g., NIST, ISO, SIG).
- Customizable forms to match your organization’s specific needs.
- Automated scoring that flags high-risk vendors based on responses.
This ensures speed, consistency, and coverage, especially when handling hundreds of vendors.
2. Continuous Monitoring and Alerts
Risk doesn’t pause after onboarding. You need a system that:
- Tracks changes in vendor cybersecurity posture.
- Monitors for breaches, financial instability, or compliance violations.
- Sends real-time alerts when a vendor’s risk level increases.
This allows you to act before the damage is done.
3. Vendor Inventory and Centralized Repository
Managing vendors across spreadsheets and emails is a recipe for oversight.
Your platform should offer:
- A centralized dashboard to view all vendors, risk levels, and contracts.
- Ability to tag, filter, and categorize vendors by risk tier or business unit.
- A timeline of engagements and activities per vendor.
This makes it easier to track performance, history, and accountability.
4. Workflow Automation
Manual follow-ups and fragmented processes slow down vendor onboarding and risk remediation.
Look for a platform that supports:
- Automated task assignments (e.g., to Legal, IT, Compliance).
- Escalation rules for overdue or non-compliant responses.
- Approval workflows for onboarding, assessments, and contract renewals.
Automation reduces human error and speeds up every stage of the lifecycle.
5. Regulatory Compliance Management
A good TPRM platform doesn’t just help with risk, it helps you prove compliance.
Must-have features include:
- Regulatory mapping (GDPR, NDPR, HIPAA, PCI-DSS, etc.).
- Document storage for audit trails and assessment history.
- Custom reporting for regulators, auditors, or the Board.
This makes regulatory reporting faster, easier, and defensible.
6. Integration with Other Systems
Your TPRM platform should not operate in a silo. Look for integrations with:
- GRC platforms (Governance, Risk, and Compliance).
- Procurement tools and ERP systems.
- Security tools (SIEM, vulnerability scanners, etc.).
- Identity and access management platforms.
Integration ensures data flows seamlessly across teams and systems.
7. Insightful Reporting and Dashboards
Risk is only manageable when you can see it clearly.
Strong platforms offer:
- Executive dashboards for a high-level overview.
- Detailed analytics on vendor performance, trends, and risk changes.
- Exportable reports for compliance, security, and procurement teams.
Bonus: Look for customizable visualizations that support better decision-making.
8. User-Friendly Interface
Even the most powerful platform is useless if no one wants to use it.
Prioritize tools that are:
- Intuitive and well-designed.
- Easy for non-technical users to navigate.
- Built for collaboration between internal teams and vendors.
Usability drives adoption, and adoption drives results.
9. Fourth-Party Discovery
A modern platform should allow you to:
- Identify the vendors your vendors rely on (i.e., fourth parties).
- Understand how these unknown entities may impact your risk.
- Extend assessments or visibility beyond direct contractual relationships.
This is especially important in complex or global supply chains.
10. Scalability and Flexibility
Your vendor network will grow, and your platform should grow with it.
Look for solutions that:
- Support unlimited vendors and assessments.
- Offer modular add-ons (e.g., AI-powered risk detection, chatbot support).
- Allow customization without constant engineering input.
Scalability ensures your TPRM maturity won’t be capped by your tools.
Conclusion
In a world where partnerships increasingly power businesses, third-party vendors play a vital role in operational success. But with that convenience comes exposure.
Third-Party Risk Management (TPRM) isn’t just a technical add-on or a compliance requirement; it’s a strategic safeguard. It ensures that your organization doesn’t just grow, but grows securely, resiliently, and responsibly.
A well-implemented TPRM program:
- Reduces the likelihood and impact of cyber threats.
- Helps maintain compliance with evolving global regulations.
- Builds operational stability by minimizing vendor disruptions.
- Protects your reputation by holding vendors to your standards.
- Aligns vendor decisions with long-term strategic goals.
But success doesn’t come from reacting to risk; it comes from proactively planning for it. From establishing a vendor management policy to evaluating vendors thoroughly, choosing the right technology platform, and building a culture of risk awareness, every step matters.
If your business works with vendors, partners, or service providers in any form (and it probably does), now is the time to start managing those relationships with the same care and structure you apply internally.
FAQ
What is the difference between vendor risk management and TPRM?
Vendor Risk Management (VRM) and Third-Party Risk Management (TPRM) are closely related, but there’s a slight difference in scope:
VRM focuses specifically on vendors, external companies that provide goods or services under a contract. It addresses risks like delivery delays, compliance gaps, or data breaches tied directly to those vendors.
TPRM is broader. It includes all third-party relationships, such as business partners, affiliates, contractors, resellers, and even the vendors of your vendors (fourth parties). It deals with the entire ecosystem of external relationships and the risks they pose to security, operations, and compliance.
In short: All vendors are third parties, but not all third parties are vendors. TPRM covers a wider risk surface.
What are the four core third-party risks?
While there are many types of risks, the four most critical categories in Third-Party Risk Management are:
Cybersecurity Risk – The risk that a third party may introduce vulnerabilities into your systems or be the entry point for a cyberattack.
Compliance Risk – The risk of violating legal or regulatory requirements due to a vendor’s failure to comply with laws (e.g., GDPR, HIPAA, NDPR).
Operational Risk – The risk of service disruption caused by third-party failures, delays, or poor performance.
Reputational Risk – The risk that a vendor’s actions (e.g., unethical practices or data breaches) could damage your brand’s image and stakeholder trust.
Who is responsible for third-party risk?
Responsibility is shared across the organization, but typically includes:
Chief Risk Officer (CRO) or Chief Information Security Officer (CISO) – oversees the overall risk strategy.
Procurement Teams – responsible for vendor onboarding and initial risk checks.
IT and Security Teams – ensure cybersecurity controls are in place.
Legal and Compliance Teams – enforce contracts and regulatory compliance.
Business Unit Owners – monitor vendor performance and ensure alignment with operational goals.
Accountability should be centralized through a cross-functional TPRM program or committee to ensure nothing falls through the cracks.
What are the 3 C’s of risk?
The 3 C’s of Risk are a simple framework used to assess and communicate risk:
Cause – What could trigger the risk? (e.g., a vendor’s poor security controls).
Consequence – What happens if the risk materializes? (e.g., a data breach, reputational damage).
Control – What safeguards are in place to prevent or mitigate the risk? (e.g., contractual clauses, continuous monitoring).
This model helps organizations define risk clearly and take actionable steps to manage it.
What are the three stages of risk management?
Risk management typically follows these three stages:
Identification – Discover and document risks associated with vendors, contracts, or services.
Assessment – Analyze and prioritize risks based on likelihood, impact, and criticality.
Mitigation/Response – Implement controls, remediation plans, and monitoring strategies to reduce or eliminate the risk.
Some frameworks add a fourth stage, monitoring, to emphasize the need for continuous evaluation, especially in dynamic vendor environments.
