
What Is Blockchain Security? A Comprehensive Breakdown
What Is Blockchain Security? A Comprehensive Breakdown
Blockchain security is a foundational aspect of the decentralized systems that power many modern technologies. Blockchain technology, at its core, provides a secure, transparent, and tamper-resistant way to record transactions. Originally popularized by cryptocurrencies like Bitcoin, blockchain has evolved beyond digital currency to become a transformative force in industries such as supply chain management, healthcare, and governance.
In essence, blockchain is designed to ensure the integrity of transactions through a decentralized network of participants, eliminating the need for a central authority. This unique structure introduces new opportunities for secure digital interactions but also presents challenges that need to be addressed to ensure the safety of blockchain networks.
Blockchain security involves a broad array of strategies and techniques aimed at safeguarding the data stored within the network. Unlike traditional centralized systems, blockchain’s distributed nature allows for higher levels of transparency and security, but this also means that any vulnerability can have widespread consequences. Whether it’s a hacking attempt on a public blockchain or an internal breach in a private system, ensuring the security of blockchain networks is crucial for maintaining trust among participants.
This article will answer the question: What is blockchain security? We will also break down the various facets of blockchain security, from the basic cryptographic principles that underpin its design to the specific threats blockchain systems face.

Start a Life-Changing Career in Cybersecurity Today
The Fundamentals of Blockchain Security
Blockchain security is built upon several key principles that collectively ensure the integrity and trustworthiness of the network. At its core, blockchain relies on cryptography, decentralization, and consensus mechanisms to protect data and validate transactions.
Cryptographic Principles
Cryptography plays a central role in securing blockchain transactions. Two of the most fundamental cryptographic concepts used in blockchain are hash functions and public-private key pairs.
- Hash Functions: These are mathematical algorithms that take an input (or ‘message’) and produce a fixed-size string of characters, which appears random. In blockchain, hash functions are used to create a unique fingerprint for each block. Once a block is added to the blockchain, its hash is linked to the hash of the previous block, creating a chain of blocks that is extremely difficult to alter. Changing any transaction in a block would result in a completely different hash, disrupting the entire blockchain and making tampering easily detectable.
- Public-Private Key Pairs: Blockchain uses asymmetric cryptography, where a user has a public key (an address to send or receive assets) and a private key (used to sign transactions). This combination ensures that only the owner of the private key can authorize transactions, and the public key acts as a pseudonymous identity on the network. This system not only keeps transactions secure but also maintains privacy, as only the owner of the private key can prove ownership of the assets associated with the public key.
Decentralization
One of the defining features of blockchain technology is decentralization. Unlike traditional systems where control is concentrated in the hands of a central authority (such as a bank or a government), blockchain distributes control across a network of nodes. Each node in the blockchain network holds a copy of the entire ledger, making it virtually impossible for a single actor to manipulate or alter the system.
- No Single Point of Failure: In centralized systems, the failure of a single entity can lead to catastrophic consequences. Blockchain eliminates this risk by distributing the ledger across numerous nodes, ensuring that no single point can compromise the entire network. If one node fails or is attacked, the others will continue to validate and secure the network.
- Transparency and Consensus: Every node in a blockchain network has access to the same data, and changes are only made when a consensus is reached. This decentralized model makes blockchain highly transparent, as all participants can verify transactions independently. It also ensures that no single participant has control over the entire network, preventing fraud and abuse.
Consensus Mechanisms
Consensus mechanisms are protocols used to achieve agreement among participants on the state of the blockchain. They are essential for maintaining the integrity of the network by ensuring that only valid transactions are added to the blockchain. There are several consensus models, each with its own security features and vulnerabilities.
- Proof of Work (PoW): In PoW, participants (miners) compete to solve complex mathematical problems, and the first one to solve the problem gets the right to add a new block to the blockchain. This process requires significant computational power and energy, making it costly for attackers to take control of the network. However, it also consumes large amounts of electricity and may lead to scalability issues.
- Proof of Stake (PoS): In PoS, validators are chosen based on the amount of cryptocurrency they hold and are willing to “stake” as collateral. Validators who attempt to cheat the system risk losing their stake. PoS is seen as a more energy-efficient alternative to PoW, but it may centralize power if a small number of entities control most of the cryptocurrency staked.
- Delegated Proof of Stake (DPoS): DPoS is a variation of PoS where stakeholders vote for delegates who validate transactions on their behalf. This system aims to increase scalability and efficiency, but may reduce decentralization since it depends on a smaller number of trusted delegates.
RELATED: CompTIA Security Vs Google Cybersecurity Certification
Types of Blockchain Networks and Their Security Implications
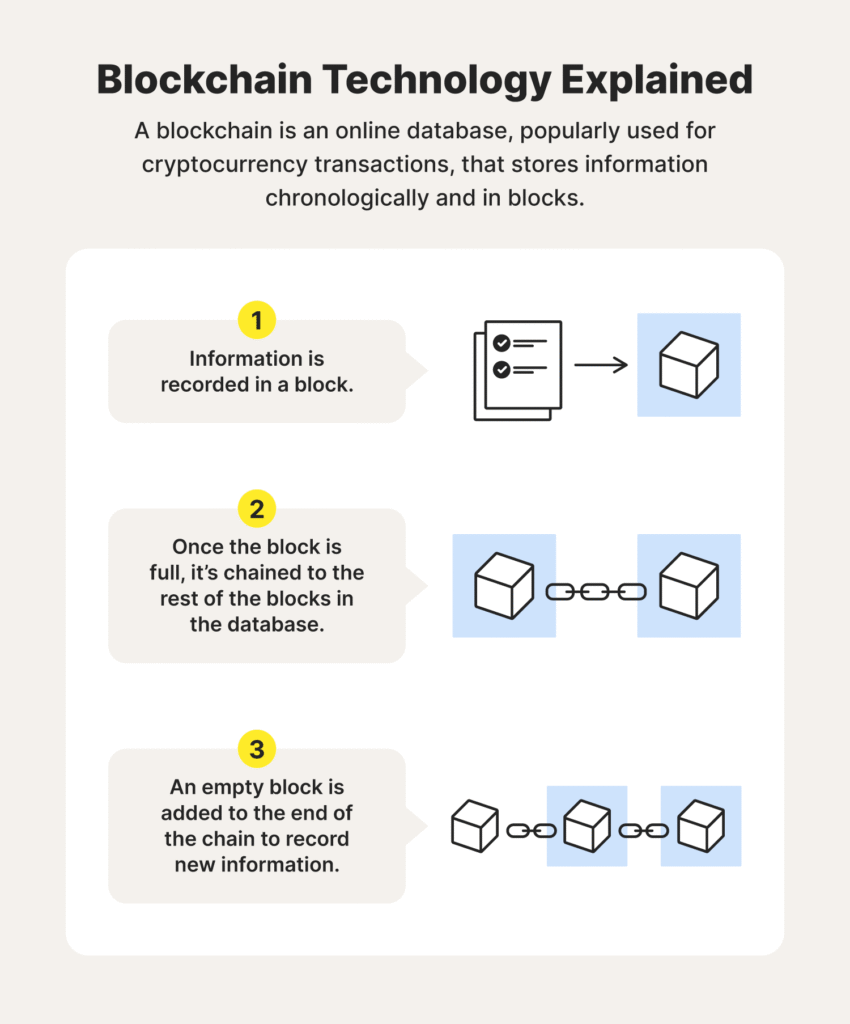
Blockchain networks can vary significantly in terms of accessibility, control, and governance. These differences have direct implications for their security profiles, as various network types present different risks and require different protective measures. In this section, we’ll explore the security differences between public vs. private blockchains and permissioned vs. permissionless blockchains, along with their respective advantages and challenges.
Public vs. Private Blockchains
- Public Blockchains:
Public blockchains are decentralized networks that are open for anyone to participate. They are typically characterized by high levels of transparency and accessibility, making them appealing for global applications such as cryptocurrencies (e.g., Bitcoin, Ethereum).
Security Features:
- Decentralized Security: In public blockchains, security is maintained by a large number of participants (nodes) across the network, each of which verifies transactions. This makes it difficult for any single actor to compromise the network.
- Consensus Mechanisms: Public blockchains typically use consensus models like Proof of Work (PoW) or Proof of Stake (PoS) to validate transactions. These models ensure that only legitimate transactions are added to the blockchain and prevent double-spending.
- Vulnerability: While public blockchains are generally secure, they are not immune to attacks. A 51% attack (where a group controls over 50% of the network’s mining power or staked coins) is still a theoretical vulnerability, though it is highly costly to execute on large networks like Bitcoin and Ethereum.
- Challenges:
- Scalability: The large number of participants in public blockchains can lead to performance and scalability issues. With each transaction needing to be verified by numerous nodes, the system can become slow and inefficient.
- Privacy: Since public blockchains are transparent, all transactions are visible to anyone. While this is a security feature in terms of accountability, it can be a privacy concern for certain applications.
- Scalability: The large number of participants in public blockchains can lead to performance and scalability issues. With each transaction needing to be verified by numerous nodes, the system can become slow and inefficient.
- Private Blockchains:
Private blockchains, on the other hand, are restricted to specific organizations or groups. These networks are more controlled, and participants must be invited or approved to join.
Security Features:
- Access Control: Since only authorized participants can access and validate transactions, private blockchains can provide a higher level of privacy and control over the data.
- Centralized Control: Although private blockchains are often described as decentralized, they still rely on a central authority for governance. This centralized control can provide more efficient decision-making but introduces potential security risks if the central authority is compromised.
- Smarter Security: Private blockchains are more likely to implement security measures like firewalls, encryption, and user authentication for added protection, given the centralized nature of control.
- Challenges:
- Vulnerability to Insider Threats: Since access is limited to known participants, the main security risks come from within. An insider threat can compromise the integrity of the network, making it critical to enforce robust security practices like multi-factor authentication and secure key management.
- Lack of Transparency: With limited visibility into transaction data, private blockchains may face issues with trust among participants. Transparency is often a key security feature in public blockchains, and the lack of it in private blockchains can sometimes lead to concerns about the integrity of the data.
- Vulnerability to Insider Threats: Since access is limited to known participants, the main security risks come from within. An insider threat can compromise the integrity of the network, making it critical to enforce robust security practices like multi-factor authentication and secure key management.
Permissioned vs. Permissionless Blockchains
- Permissionless Blockchains:
In a permissionless blockchain, anyone can join the network and validate transactions without needing approval from a central authority. This decentralized structure promotes openness and encourages innovation.
Security Features:
- No Central Control: Without a central authority, the security of permissionless blockchains depends entirely on the consensus of the network participants. This ensures that the system remains transparent and resilient to censorship.
- Open Validation: Since anyone can join and participate in the network, the blockchain benefits from a diverse range of participants who work together to validate transactions and keep the network secure.
- No Central Control: Without a central authority, the security of permissionless blockchains depends entirely on the consensus of the network participants. This ensures that the system remains transparent and resilient to censorship.
- Challenges:
- Inclusion of Malicious Actors: The open nature of permissionless blockchains allows for the possibility of malicious actors joining the network. Without sufficient screening, bad actors could potentially exploit the network’s consensus mechanism, although this risk is mitigated by strong cryptographic protocols and validation mechanisms.
- Sybil Attacks: In permissionless blockchains, Sybil attacks (where a participant creates multiple fake identities to gain control) can be a concern. Effective consensus models and high participation requirements help mitigate this threat.
- Inclusion of Malicious Actors: The open nature of permissionless blockchains allows for the possibility of malicious actors joining the network. Without sufficient screening, bad actors could potentially exploit the network’s consensus mechanism, although this risk is mitigated by strong cryptographic protocols and validation mechanisms.
- Permissioned Blockchains:
A permissioned blockchain requires participants to be authorized to join the network. In this setup, access is controlled by a central authority, and only trusted individuals or entities are granted permission to validate transactions.
Security Features:
- Controlled Access: Since only trusted participants can access the blockchain, the security risks of malicious actors are reduced. Permissioned blockchains can offer a higher level of confidentiality and privacy since unauthorized participants are blocked from viewing or modifying the data.
- Enhanced Compliance: Permissioned blockchains are ideal for industries with strict regulatory requirements, such as finance and healthcare, as they allow for greater control over who can access sensitive information.
- Challenges:
- Centralization of Control: The main security risk in permissioned blockchains is the potential for abuse by the central authority that governs the network. If the controlling entity becomes compromised, the entire blockchain could be vulnerable.
- Dependence on Trust: Permissioned blockchains rely on trust among participants. The integrity of the system is heavily dependent on the honesty of those granted access. Therefore, robust governance mechanisms and transparency measures are crucial for ensuring security.
- Centralization of Control: The main security risk in permissioned blockchains is the potential for abuse by the central authority that governs the network. If the controlling entity becomes compromised, the entire blockchain could be vulnerable.
READ ALSO: How to Become a Certified Cloud Security Professional (CCSP) in 2025
Common Blockchain Security Threats
Despite the robust security features inherent in blockchain technology, no system is entirely immune to threats. Understanding these risks is crucial for developing effective security measures. In this section, we’ll examine some of the most common security threats faced by blockchain networks and how they can be mitigated.
1. Code Exploitation and Smart Contract Vulnerabilities
One of the most significant vulnerabilities in blockchain networks arises from the code used in smart contracts. Smart contracts are self-executing contracts with the terms of the agreement directly written into code. While they offer automation and transparency, flawed or untested code can lead to devastating exploits.
Real-world Example:
The infamous DAO hack in 2016, where attackers exploited a flaw in a smart contract, resulted in the theft of millions of dollars’ worth of Ether. This event highlighted the importance of smart contract security and the need for thorough code audits and testing before deployment.
Mitigation:
- Regular Audits: Smart contracts should be subject to both automated and manual audits to identify potential vulnerabilities before they are deployed. This should be a standard practice, especially in high-value applications like DeFi (Decentralized Finance).
- Test Networks: Using test networks (testnets) for deploying and testing contracts can significantly reduce the risk of vulnerabilities making it into the mainnet.
2. Phishing Attacks
Phishing remains one of the most common and effective methods for attacking blockchain networks. Cybercriminals use deceptive emails, websites, or messages to trick users into revealing their private keys or transferring funds to fraudulent addresses.
Real-world Example:
Phishing scams often target users of cryptocurrency exchanges or wallets. Attackers create fake login pages or send emails that mimic legitimate services, asking users to enter their private keys or wallet recovery phrases. Once the attacker gains access to the private key, they can steal all assets in the user’s wallet.
Mitigation:
- User Education: The most effective way to combat phishing is through education. Users should be taught to recognize phishing attempts, verify the source of emails or websites, and never share private keys.
- Two-Factor Authentication (2FA): Enabling 2FA on accounts that handle cryptocurrencies can add an extra layer of security, making it harder for attackers to access funds even if they manage to obtain a user’s credentials.
3. 51% Attacks
A 51% attack occurs when a group of miners or validators gains control over 50% of the mining or validation power in a blockchain network. With this control, they can manipulate the blockchain by reversing transactions, double-spending coins, or preventing new transactions from being confirmed.
Real-world Example:
In 2018, the Bitcoin Cash network suffered a 51% attack. The attackers were able to reorganize blocks and double-spend coins, causing significant disruption within the network. While the attack was costly and difficult to execute, smaller networks with less mining power are more vulnerable to this kind of attack.
Mitigation:
- Increase Network Participation: To prevent 51% attacks, networks should aim to have a high number of miners or validators, making it economically unfeasible for any group to control the majority.
- Hybrid Consensus Models: Some blockchains combine different consensus models (e.g., PoW and PoS) to increase the difficulty of orchestrating a 51% attack.
4. Routing Attacks
Routing attacks target the communication channels that transmit blockchain data between nodes. By intercepting or rerouting network traffic, attackers can manipulate the data, steal information, or delay transactions.
Real-world Example:
In a man-in-the-middle attack, hackers may intercept blockchain transaction data while it is in transit, altering the contents before sending it to the network. Although such attacks are rare, they highlight the vulnerabilities in network communication protocols.
Mitigation:
- Secure Communication Protocols: Using SSL/TLS encryption for data transmission and adopting VPNs or private communication channels can prevent unauthorized parties from intercepting blockchain data.
- Multi-path Routing: Employing multi-path routing and redundant connections can minimize the risk of routing attacks by ensuring that there is no single point of failure for data transmission.
5. Sybil Attacks
A Sybil attack occurs when an attacker creates multiple fake identities (or nodes) to gain control over a network. These fake nodes can overwhelm the network’s consensus mechanism and potentially disrupt operations.
Real-world Example:
In permissionless blockchains, an attacker might flood the network with numerous fake identities to gain influence over the consensus process, potentially leading to false validation of transactions or manipulation of the network.
Mitigation:
- Proof of Stake (PoS): PoS-based blockchains are more resistant to Sybil attacks, as creating fake identities would require a significant amount of the cryptocurrency to stake, making it expensive and economically infeasible for an attacker.
- Identity Verification: Implementing identity verification techniques, even in permissionless networks, can help ensure that participants are legitimate and reduce the likelihood of Sybil attacks.
These are just a few of the most common threats facing blockchain networks. As we explore further, we’ll discuss best practices for securing blockchain applications and how developers and users can mitigate these threats through various technical and procedural measures.
SEE MORE: What Does Cloud Network Security Mean in 2025?
Blockchain Security Best Practices
To ensure the security of blockchain networks and prevent attacks, it’s essential to follow industry best practices. Blockchain security is a continuous process that requires vigilance and proactive measures. Here, we’ll outline some of the most effective strategies and tools to strengthen blockchain security and reduce vulnerabilities.
1. Smart Contract Audits
Smart contracts are automated agreements executed on the blockchain, but they can become a significant security risk if their code is not thoroughly audited. Vulnerabilities in smart contract code can be exploited by attackers, leading to financial losses or unauthorized access to data.
Best Practices for Auditing Smart Contracts:
- Automated Testing Tools: Use automated testing tools to scan smart contracts for known vulnerabilities and logic errors. Tools like MythX and Slither can help identify common vulnerabilities such as reentrancy, overflow, and underflow issues.
- Manual Code Review: In addition to automated tests, a manual review by security experts is crucial for identifying complex vulnerabilities that automated tools might miss. Auditors can assess the logic of the contract, ensuring that it performs as expected without unintended side effects.
- Bug Bounty Programs: Consider setting up a bug bounty program where ethical hackers can identify and report vulnerabilities in exchange for a reward. This is an effective way to involve the community in improving the security of the smart contracts.
2. Secure Key Management
In blockchain systems, cryptographic keys are the foundation of security. Losing or compromising private keys can lead to the theft of assets or unauthorized access to critical blockchain resources. Therefore, it’s essential to manage keys securely to avoid breaches.
Best Practices for Key Management:
- Cold Storage: Store private keys in cold storage (offline) to prevent online attacks. Hardware wallets like Ledger or Trezor are excellent options for securely storing keys.
- Multi-Signature Wallets: Implement multi-signature wallets, which require multiple private keys to authorize a transaction. This significantly reduces the risk of a single compromised key leading to a loss of assets.
- Key Rotation: Regularly rotate cryptographic keys and revoke old ones to minimize the impact of a potential compromise. Ensure that users are educated on how to securely manage their keys and back them up safely.
3. Identity and Access Management (IAM)
Managing identities and controlling access are crucial for maintaining the security of permissioned blockchain networks. IAM ensures that only authorized participants can access the network and perform transactions. In the case of private blockchains, strong IAM protocols are necessary to safeguard sensitive data.
Best Practices for IAM:
- Role-Based Access Control (RBAC): Implement RBAC to limit access to blockchain resources based on user roles. Only users with the appropriate permissions should be able to validate transactions or view sensitive data.
- Multi-Factor Authentication (MFA): Use MFA to ensure that only authorized users can access critical blockchain services. This adds an additional layer of security beyond just passwords or private keys.
- Identity Verification: For private or permissioned blockchains, utilize digital identity verification systems to confirm the legitimacy of participants. Techniques such as biometric authentication or two-factor authentication can be incorporated to enhance security.
4. Regular Updates and Patching
Blockchain networks are constantly evolving, and new vulnerabilities are discovered regularly. Keeping the software up to date with the latest security patches is vital for preventing exploitation of known vulnerabilities.
Best Practices for Updates:
- Frequent Patching: Regularly update blockchain protocols and related software to ensure that known vulnerabilities are patched promptly. Developers should monitor and apply updates from trusted sources as soon as they become available.
- Test Updates on Testnets: Before deploying updates on the main blockchain, thoroughly test them on a testnet (a test version of the blockchain) to ensure that they don’t introduce new issues or security vulnerabilities.
- Security Monitoring: Continuously monitor the blockchain network for unusual activities or potential signs of exploitation. Early detection of any suspicious behavior can help mitigate attacks before they cause significant damage.
5. Secure Communication Protocols
Blockchain networks rely on communication between nodes to transfer transaction data. Securing these communications is essential to protect the network from man-in-the-middle attacks and other interception threats.
Best Practices for Secure Communication:
- Encryption: Ensure that all data transmitted across the network is encrypted using strong encryption protocols like SSL/TLS. This prevents attackers from intercepting and manipulating transaction data during transmission.
- Virtual Private Networks (VPNs): Use VPNs to add an additional layer of protection for blockchain communication. This ensures that data is transferred through secure and private channels, making it harder for attackers to intercept or tamper with the data.
- Private Channels: For sensitive transactions, consider using private communication channels that are not exposed to the public internet. This can reduce the risk of routing and DDoS attacks.
These best practices serve as a foundation for building secure blockchain networks. By adhering to these protocols, developers, businesses, and users can significantly enhance the security of blockchain applications and reduce the risks associated with potential attacks.
ALSO: What Coding Language Should I Learn for Cyber Security?
Enterprise Blockchain Security Considerations
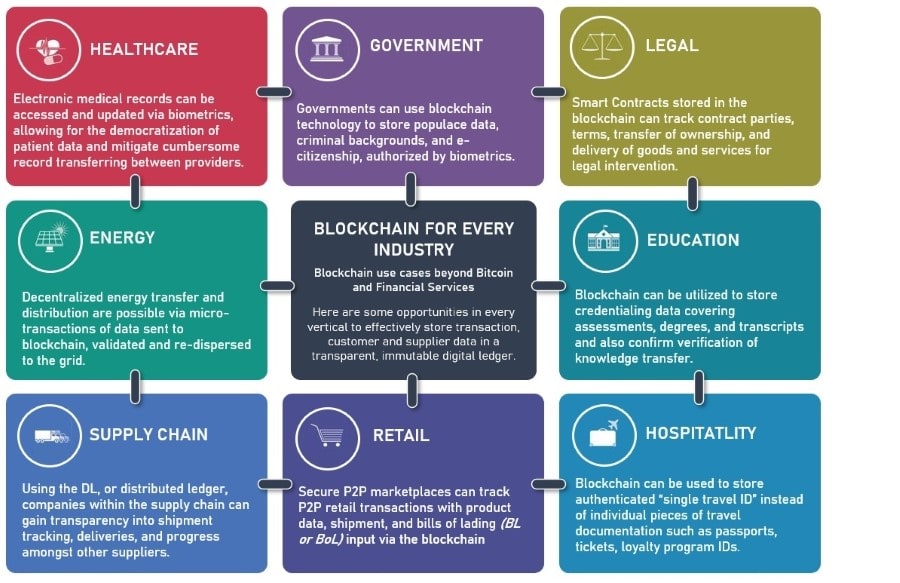
Enterprise blockchain applications are increasingly being adopted across industries like finance, healthcare, and supply chain management. While blockchain offers many benefits, such as decentralization, transparency, and immutability, enterprises must address specific security challenges due to their unique needs, regulatory environments, and requirements for privacy and scalability.
In this section, we’ll explore the security challenges faced by enterprises and the best practices they can implement to secure their blockchain solutions.
1. Unique Security Challenges for Enterprises
Enterprises operate in regulated environments and handle sensitive data, which makes security a paramount concern. The decentralized nature of blockchain may clash with traditional security measures used in centralized systems, requiring businesses to reassess their approach to data governance and access control.
- Regulatory Compliance: Many industries, particularly finance and healthcare, are subject to strict regulatory requirements regarding data privacy, access, and security. Blockchain networks must ensure that they comply with laws such as the General Data Protection Regulation (GDPR), Health Insurance Portability and Accountability Act (HIPAA), and Financial Action Task Force (FATF) guidelines.
- Data Privacy: Enterprises need to balance blockchain’s transparency with the need to protect sensitive data. While blockchain’s public ledger makes transactions transparent, organizations must ensure that private data (e.g., personal identification or financial records) remains confidential and complies with privacy laws.
- Internal Threats: Enterprise blockchain networks are often permissioned, meaning that access is granted only to specific, trusted participants. However, insider threats, such as malicious employees or contractors, can compromise the system if proper access controls and monitoring aren’t in place.
2. Comprehensive Security Framework for Enterprise Blockchains
To address the security challenges specific to enterprise blockchain solutions, businesses must adopt a comprehensive security framework. This framework should include a combination of traditional security controls and blockchain-specific security measures.
- Identity and Access Management (IAM): Implementing robust IAM protocols is critical to ensuring that only authorized individuals can access blockchain data and perform actions on the network. This can include role-based access controls (RBAC), multi-factor authentication (MFA), and identity verification for participants.
- Data Privacy Controls: Privacy-enhancing technologies, such as zero-knowledge proofs (ZKPs), allow for the validation of transactions without exposing sensitive information. For example, in healthcare applications, ZKPs could be used to validate that a patient’s medical data is correct without revealing the details of the diagnosis.
- Smart Contract Security: Enterprises must ensure that smart contracts used in business operations are secure, thoroughly tested, and audited. Automated tools and manual reviews should be employed to detect and fix vulnerabilities before smart contracts are deployed on the blockchain.
- Governance Models: Strong governance frameworks are essential for managing the blockchain network’s security. This includes defining roles, responsibilities, and decision-making processes, especially when it comes to adding new participants or making changes to the blockchain protocol.
3. Real-World Examples of Enterprise Blockchain Security
Several enterprises have already adopted blockchain technology and implemented strong security practices to safeguard their operations. Let’s look at a few case studies:
- Supply Chain Management: Companies like IBM have successfully implemented blockchain to enhance the transparency and security of their supply chains. IBM’s Food Trust Blockchain tracks the movement of food products from farm to table. By using blockchain, stakeholders can ensure the authenticity of products, reduce fraud, and comply with regulations. Security measures include secure data storage and encryption, ensuring that sensitive product information is protected.
- Cross-Border Payments: Ripple, a blockchain-based payment platform, enables banks and financial institutions to conduct real-time cross-border transactions. Ripple’s security model relies on consensus mechanisms to validate transactions and ensure they are tamper-proof. Additionally, it uses secure communication protocols to protect the integrity of data in transit and prevent man-in-the-middle attacks.
- Healthcare: MedRec, a blockchain-based system developed by MIT, allows healthcare providers to securely store and share patient medical records. MedRec uses permissioned blockchain and cryptographic techniques to ensure that only authorized users can access and update patient data, meeting the security and compliance requirements of the healthcare industry.
4. Best Practices for Securing Enterprise Blockchain Solutions
To ensure the success of blockchain applications in enterprise environments, businesses must implement the following security best practices:
- Comprehensive Security Audits: Regular security audits of the blockchain infrastructure, smart contracts, and the underlying code are necessary to identify and mitigate vulnerabilities. This includes testing for logic flaws, security holes, and compliance gaps.
- Network Security: Enterprises should employ advanced network security measures such as firewalls, intrusion detection systems (IDS), and virtual private networks (VPNs) to protect against external threats. Additionally, using a distributed network of nodes can ensure the resilience of the blockchain against attacks.
- Smart Contract Formal Verification: To prevent the deployment of insecure contracts, enterprises should use formal verification methods to mathematically prove that the smart contract behaves as expected under all conditions. This step is essential for high-stakes applications like finance and healthcare.
- Compliance Management: Blockchain solutions must be aligned with industry-specific regulations and standards. For example, financial institutions should ensure that their blockchain solutions meet Anti-Money Laundering (AML) and Know Your Customer (KYC) regulations. Regular compliance checks and audits should be conducted to ensure that the blockchain application adheres to legal requirements.
- Data Backup and Disaster Recovery: Blockchain data should be backed up in secure locations, and disaster recovery plans should be in place to mitigate the risk of data loss due to attacks or technical failures. Since blockchain transactions are immutable, recovering lost data can be complex without proper planning.
Conclusion
Blockchain technology has revolutionized the way we think about digital transactions, providing a decentralized, transparent, and tamper-resistant way of storing and sharing data. However, as with any technology, security remains a critical concern. Ensuring blockchain security involves understanding its core principles, recognizing common threats, and implementing best practices to safeguard the network.
Blockchain security is built upon three foundational pillars: cryptography, decentralization, and consensus mechanisms. Together, these elements ensure that transactions are secure, transparent, and tamper-proof. However, as the blockchain ecosystem grows, new challenges emerge, including smart contract vulnerabilities, phishing attacks, and 51% attacks. These risks underscore the need for proactive security measures, such as thorough audits, secure key management, and robust identity and access controls.
Enterprise applications of blockchain also present unique security challenges. These networks often handle sensitive data, require compliance with regulations, and demand robust access controls. Enterprises must implement comprehensive security frameworks that include secure smart contract practices, IAM protocols, and data privacy measures to mitigate risks and ensure the protection of critical business operations.
Looking to the future, blockchain security is set to evolve with the rise of emerging technologies such as quantum computing and AI, which promise to enhance security measures and help detect threats in real time. Additionally, as regulatory frameworks mature, blockchain networks will need to adapt to ensure compliance with privacy laws and industry standards. The ongoing collaboration within the blockchain community, alongside the development of new security tools and best practices, will be crucial in strengthening the security posture of blockchain systems.
Blockchain security is not a one-time effort but a continuous process of vigilance, adaptation, and innovation. As blockchain technology continues to transform industries worldwide, the importance of robust security cannot be overstated. By embracing emerging technologies, adhering to security best practices, and fostering collaboration within the community, businesses and developers can ensure that blockchain remains a trusted, secure foundation for digital transactions and decentralized applications.
FAQ
What are the 4 types of blockchain?
The four main types of blockchain are:
Public Blockchains: Open to anyone and fully decentralized, where anyone can join and validate transactions (e.g., Bitcoin, Ethereum).
Private Blockchains: Restricted to a specific group of participants or organizations, often used for internal business operations.
Permissioned Blockchains: These require participants to have permission to join, providing more control and privacy than public blockchains (e.g., Hyperledger).
Permissionless Blockchains: Anyone can join and participate without needing approval, allowing for open validation and decentralized governance (e.g., Bitcoin).
How to get into blockchain security?
To get into blockchain security, follow these steps:
Learn the Basics of Blockchain: Start with understanding blockchain fundamentals, cryptography, and consensus mechanisms.
Understand Blockchain Security Risks: Study common threats like smart contract vulnerabilities, 51% attacks, and phishing.
Learn Security Practices: Gain knowledge in security protocols, cryptographic techniques, and key management.
Earn Relevant Certifications: Consider certifications such as Certified Blockchain Security Professional (CBSP) or Certified Information Systems Security Professional (CISSP).
Gain Experience: Work on blockchain projects, participate in hackathons, and contribute to open-source blockchain security projects.
How much do blockchain security people make?
Blockchain security professionals typically earn competitive salaries, with figures depending on experience, location, and expertise:
Average Salary: Blockchain security specialists can earn between $100,000 to $200,000 per year, with the average around $120,000 to $150,000 annually in the U.S.
Senior Roles: More experienced professionals, especially in senior positions, can earn upwards of $200,000+ per year.
Freelance or Contract Work: For freelance blockchain security experts, hourly rates can range from $75 to $150, depending on their skill set and market demand.
Who owns blockchain?
Blockchain is decentralized by nature, meaning no single entity owns the entire blockchain network. Ownership is distributed among all the participants (nodes) in the network. Each participant (whether a miner, validator, or user) has access to the blockchain’s data and validates transactions.
In the case of public blockchains, such as Bitcoin or Ethereum, anyone can join and participate in the network, but no one owns the blockchain itself. For private blockchains, ownership may be controlled by a specific organization or consortium of entities that manage the network.
