The Three Main Pillars of Information Security: Complete 2026 Guide
The Three Main Pillars of Information Security: Complete 2026 Guide
Today, organizations face an unprecedented volume of threats to their sensitive data. From ransomware attacks that lock critical systems to breaches exposing customer records, the stakes have never been higher. A single lapse can result in financial loss, reputational damage, and regulatory penalties.
At the heart of a strong security strategy are the three main pillars of information security, confidentiality, integrity, and availability, collectively known as the CIA triad. These principles provide a structured framework for protecting data, ensuring it remains secure, trustworthy, and accessible when needed. Understanding these pillars is essential not only for IT teams but also for business leaders, compliance officers, and anyone responsible for safeguarding information.
While modern frameworks may expand to include additional elements, like the 5 pillars of information security or the 8 components of information and cyber security, the CIA triad remains the foundation for all effective security practices. By mastering these three pillars, organizations can reduce risk, strengthen compliance, and maintain operational resilience in the face of evolving cyber threats.
This guide will analyse each pillar in depth, providing practical examples, challenges, and best practices to help organizations apply these principles effectively. By the end, you’ll understand not only what the three pillars of information security are but also how they interact to form a comprehensive defense against modern cyber threats.

Start a Life-Changing Career in Cybersecurity Today
Confidentiality: Protecting Data from Unauthorized Access
Confidentiality is the first and perhaps most critical pillar of information security. At its core, confidentiality ensures that sensitive information is accessible only to authorized individuals. Without robust confidentiality measures, personal data, proprietary business information, and critical operational records can be exposed, leading to identity theft, financial loss, or strategic disadvantages.
Maintaining confidentiality requires more than just password-protected files. Organizations must implement layered security measures that protect data both at rest and in transit. Encryption, access controls, and secure communication protocols form the backbone of effective confidentiality strategies.
For example, data encryption converts readable information into coded formats, ensuring that even if intercepted, the information cannot be understood without the correct decryption key. Similarly, multi-factor authentication (MFA) strengthens access control by requiring multiple verification steps before granting access to sensitive resources.
Real-World Example: Early in 2024, vulnerabilities in Microsoft Exchange servers allowed attackers to access sensitive government and corporate emails. This breach highlighted how quickly unauthorized access can compromise confidential data and why organizations must continuously assess and update their security protocols.
Challenges:
- Balancing security with accessibility: Employees need access to information to perform their jobs efficiently. Restrictive controls can slow operations if not designed carefully.
- Evolving threats: Cybercriminals continually develop sophisticated methods to bypass security measures, requiring ongoing monitoring and updates.
Best Practices:
- Implement Strong Authentication Methods: MFA, biometric verification, and role-based access controls reduce the risk of unauthorized access.
- Regular Security Audits: Periodic assessments help identify vulnerabilities and ensure compliance with confidentiality standards.
- Data Masking: Obscuring sensitive information in databases prevents exposure during internal testing or analytics processes.
Integrity: Ensuring Data Accuracy and Trustworthiness
Integrity is the second pillar of information security, focused on maintaining the accuracy, consistency, and reliability of information. While confidentiality keeps unauthorized users out, integrity ensures that authorized users cannot inadvertently or maliciously alter critical data. Without integrity, organizations risk relying on corrupted or inaccurate information, which can lead to operational errors, financial losses, and compromised decision-making.
Maintaining data integrity involves protecting information from tampering, unauthorized modifications, and accidental corruption throughout its lifecycle, from creation to deletion. Organizations employ a combination of policies, processes, and technologies to monitor, verify, and safeguard data.
Practical Measures:
- Digital Signatures: Cryptographic tools that verify data authenticity and detect any alterations.
- Hash Functions: Generating unique digital fingerprints for files to ensure they remain unmodified. Any change in the data alters the hash, signaling potential tampering.
- Access Controls and Logging: Restricting who can modify data and maintaining detailed records of all changes to track accountability.
Real-World Example: In the financial sector, unauthorized modification of transaction records can have devastating consequences. Attackers altering account balances or transaction histories can hide fraudulent activity, potentially leading to regulatory fines and significant financial loss. Organizations like Cybereason use behavior-centric threat detection to monitor for suspicious activities that could compromise data integrity, stopping attacks before they escalate.
Challenges:
- Detecting subtle or sophisticated alterations that appear legitimate.
- Ensuring end-to-end integrity across multiple systems and platforms, especially in distributed cloud environments.
Best Practices:
- Implement Cryptographic Verification: Digital signatures and hash checks should be standard to detect tampering.
- Regular Monitoring and Audits: Continuously review data changes to identify unauthorized modifications.
- Clear Policies for Data Modification: Define who can edit data, under what conditions, and enforce strict logging of all changes.
RELATED: GRC Analyst Roles and Responsibilities: Career Path, Skills, Salary & Interview Guide
Availability: Ensuring Access to Data and Systems When Needed
Availability is the third pillar of information security, ensuring that data and systems remain accessible to authorized users whenever required. Even the most secure and accurate information loses value if it cannot be accessed in time. For organizations, maintaining availability is critical for operational continuity, customer satisfaction, and compliance with service-level agreements.
Availability challenges arise from both technical failures and malicious attacks. Systems can become unavailable due to hardware malfunctions, software errors, natural disasters, or cyberattacks such as Distributed Denial of Service (DDoS) and ransomware, which specifically target availability by locking users out of critical systems until a ransom is paid. Understanding which pillar of information security ransomware affects most underscores why availability must be a priority for every organization.
Practical Measures:
- Disaster Recovery Plans: Developing comprehensive, regularly tested plans to restore systems and data after an outage.
- Redundancy and Failover Systems: Implementing backup servers, cloud services, and failover mechanisms to ensure uninterrupted access.
- Regular Backups: Frequent backups of critical data safeguard against loss from cyberattacks, corruption, or system failures.
Real-World Example: Ransomware attacks on healthcare systems have highlighted the consequences of compromised availability. Clinics and hospitals have faced temporary shutdowns of patient management systems, delaying care and causing operational chaos.
Companies like Cybereason deploy multi-layered anti-ransomware strategies combining behavioral analytics, machine learning, and intelligence-driven detection to prevent disruptions and maintain system uptime.
Challenges:
- Mitigating DDoS attacks that flood networks with traffic, rendering systems inaccessible.
- Rapid recovery from unexpected disruptions without losing data integrity or compromising confidentiality.
Best Practices:
- Multi-Layered Security Measures: Firewalls, intrusion detection systems, and anti-DDoS solutions protect systems against attacks.
- Regular Disaster Recovery Testing: Ensure recovery plans are effective and executable under pressure.
- System Updates and Patching: Keeping software up to date prevents vulnerabilities that could impact availability.
How the Three Pillars of Information Security Work Together
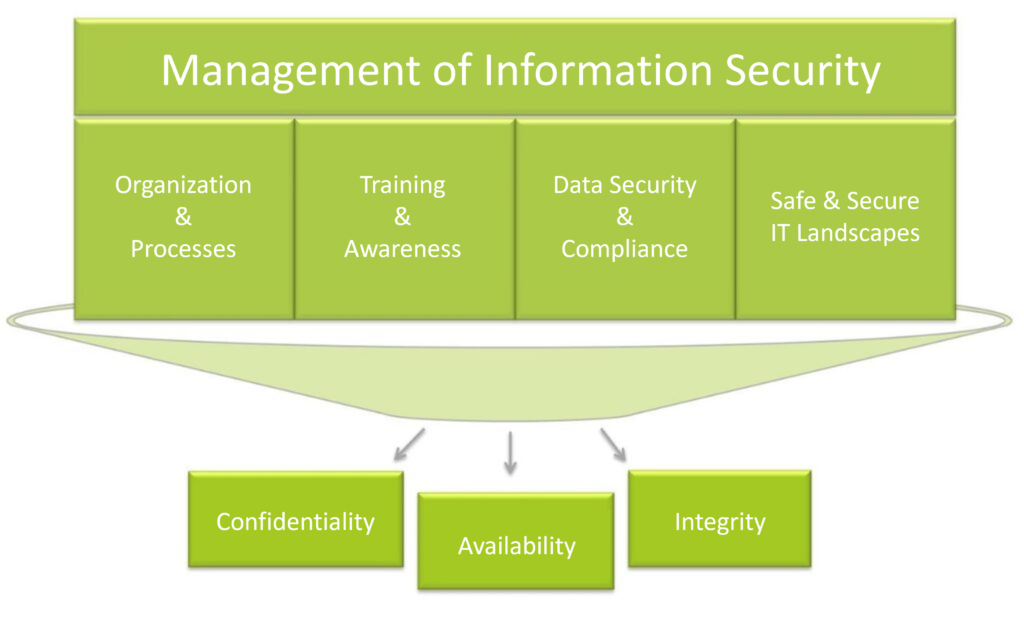
While confidentiality, integrity, and availability are distinct principles, they are inherently interdependent and must work in synergy to create a comprehensive security framework.
Weakness in one pillar can compromise the effectiveness of the others, leaving organizations vulnerable to data breaches, cyberattacks, and operational disruptions. By integrating these pillars into a cohesive strategy, organizations can build a robust defense against a wide array of threats.
For example, if confidentiality is compromised through a breach that exposes sensitive data, this may also undermine the integrity of that data if attackers alter or manipulate the exposed information. On the other hand, availability can be severely impacted if a ransomware attack locks users out of systems, making critical data inaccessible, regardless of how securely it’s been stored or protected.
Confidentiality ensures that data is protected from unauthorized access, but without integrity, the data could be altered or corrupted, leading to potentially disastrous decisions based on incorrect information. Similarly, without availability, even the most secure and accurate data becomes useless if users cannot access it when needed.
Real-World Example: A financial institution might implement strong encryption (confidentiality) and digital signatures (integrity) to safeguard customer records, but if their systems are not available due to a cyberattack or natural disaster, clients will be unable to access their accounts or transactions. The balance between these pillars is crucial for delivering a reliable and secure service.
Challenges in Integration:
- Ensuring a balanced approach to all three pillars: Overemphasizing one can lead to neglecting others. For example, focusing too much on confidentiality might result in strict access controls that hinder availability.
- Complex environments: Modern businesses use a mix of on-premise, cloud, and hybrid infrastructures, making it challenging to integrate all three pillars across different platforms and technologies.
Best Practices for Integration:
- Comprehensive Security Policies: Develop policies that address all three pillars, ensuring that data is protected, accurate, and accessible across all systems.
- Layered Security Controls: Employ multiple security technologies, such as firewalls, encryption, and multi-factor authentication, that collectively address confidentiality, integrity, and availability.
- Continuous Monitoring and Incident Response: Implement 24/7 monitoring to detect threats and ensure quick recovery from incidents that affect any of the three pillars.
ALSO READ: How to Start a Cybersecurity Firm
Expanded Frameworks: Beyond the CIA Triad
While the CIA triad (Confidentiality, Integrity, and Availability) remains the cornerstone of information security, many organizations implement expanded frameworks that introduce additional pillars and components.
These frameworks are designed to address the evolving landscape of cybersecurity, offering a more granular approach to safeguarding information and ensuring robust security practices across all aspects of an organization’s operations.
The 5 Pillars of Information Security
The 5 pillars of information security expand on the traditional CIA triad by adding Authentication and Non-repudiation. Together, these five pillars provide a more comprehensive view of the security landscape, addressing both the technical and operational needs of modern organizations.
- Confidentiality
As discussed, confidentiality protects sensitive data from unauthorized access or disclosure, ensuring that only authorized individuals can access specific information.
- Integrity
Integrity ensures the accuracy and reliability of data, safeguarding it from unauthorized modifications, whether accidental or malicious.
- Availability
Availability guarantees that information and systems are accessible when needed, supporting business continuity and user access at all times.
- Authentication
Authentication verifies the identity of users, devices, or systems attempting to access a network or resource. By ensuring that only legitimate users or systems can interact with sensitive data, authentication plays a crucial role in maintaining confidentiality and integrity.
- Non-repudiation
Non-repudiation ensures that the sender of data cannot deny their actions. This is achieved through mechanisms such as digital signatures and secure logging. Non-repudiation strengthens integrity by providing verifiable proof of actions, helping prevent fraud, and ensuring accountability.
Real-World Example: Financial institutions often use multi-factor authentication (MFA) as a form of authentication, while digital signatures ensure non-repudiation during financial transactions. These practices not only enhance confidentiality and integrity but also prevent fraud and unauthorized access.
The 8 Components of Information Security
For organizations seeking an even more detailed framework, the 8 components of information security provide a comprehensive approach to securing all facets of an organization’s information systems. These components build on the CIA triad, adding additional layers of security to address more specific needs.
- Confidentiality
As always, confidentiality remains central to protecting sensitive data.
- Integrity
Ensuring that data remains trustworthy and unaltered.
- Availability
Protecting data from disruption or denial of access.
- Authentication
Verifying the identity of users and systems to ensure authorized access.
- Authorization
Authorization ensures that authenticated users have appropriate permissions to access specific resources, reinforcing confidentiality and integrity by limiting access based on roles and privileges.
- Accountability
Accountability tracks user actions to ensure they can be held responsible for their activities. This often involves detailed logging and auditing, which helps detect suspicious behavior and maintain the integrity of systems.
- Auditing and Monitoring
Regular audits and continuous monitoring provide real-time insights into security activities. They help identify vulnerabilities, detect incidents early, and ensure compliance with security policies.
- Non-repudiation
As mentioned earlier, non-repudiation ensures that actions are verifiable and traceable, preventing denials of responsibility.
Real-World Example: In healthcare, authorization ensures that only medical professionals have access to patient records, while accountability and auditing help track access and modifications to patient data, ensuring compliance with regulatory frameworks such as HIPAA (Health Insurance Portability and Accountability Act).
Why These Expansions Matter
The 5 pillars of information security and the 8 components of information security provide a more nuanced approach to managing cybersecurity threats. As businesses become more complex and digital infrastructures grow, these frameworks help cover the gaps left by the CIA triad alone.
By incorporating additional pillars such as authentication, authorization, and accountability, organizations can better defend against emerging threats and ensure a more robust security posture.
Expanding beyond the basic triad helps organizations build comprehensive security strategies that address everything from data access to system auditing, ensuring that all potential vulnerabilities are accounted for and mitigated.
SEE MORE: Cybersecurity Threats for LLM-Based Chatbots: 2026 Update for Professionals
Implementing the Three Pillars of Information Security
The principles of Confidentiality, Integrity, and Availability (CIA triad) are not just theoretical concepts; they are actionable frameworks that organizations across various industries must implement to protect data, ensure operational continuity, and comply with regulations.
Let’s explore how the three pillars of information security apply in healthcare, finance, and retail, where the consequences of data breaches can be severe.
Healthcare: Protecting Patient Data and Ensuring Availability in Emergencies
In the healthcare industry, data security is not just about protecting patient privacy; it directly impacts patient care and safety. Confidentiality is paramount when handling personal health records (PHR) and medical data, as unauthorized access can lead to breaches of privacy and legal repercussions.
Integrity ensures that patient data is accurate and unaltered, which is critical for accurate diagnosis, treatment, and decision-making. Availability guarantees that patient data is accessible at all times, especially during emergencies when rapid access to medical history can be a matter of life or death.
Example:
Hospitals and clinics implement encryption and access control systems to ensure confidentiality of patient records. Digital signatures and hash functions maintain integrity, ensuring that patient data is not altered without authorization.
Additionally, availability is maintained through disaster recovery plans, redundant systems, and cloud-based backups, ensuring healthcare providers can access critical information when it matters most.
Challenges:
- Balancing the need for accessible data with the requirement to keep it secure, especially in emergency situations.
- Ensuring data integrity across multiple platforms and devices used by healthcare providers.
Best Practices:
- Encryption: Encrypt sensitive patient data both at rest and in transit.
- Access Control: Use role-based access control (RBAC) to limit access to sensitive information.
- Redundancy: Implement failover systems to guarantee data availability even during system failures.
Finance: Safeguarding Transaction Data and Preventing Fraud
In the finance sector, the three pillars of information security are critical for ensuring that financial transactions are secure, accurate, and accessible. Confidentiality protects customer information, such as account details and personal identification data, from unauthorized access.
Integrity ensures the accuracy of financial records, preventing fraudulent activities or errors that could lead to substantial financial loss. Availability ensures that banking systems are always online, allowing customers to access their accounts and complete transactions without interruption.
Example:
A large bank uses multi-factor authentication (MFA) to ensure confidentiality when customers access online banking. Digital signatures and hash functions are used to ensure integrity of transaction records, making it impossible for attackers to alter financial data without detection. Finally, the bank ensures availability by using redundant systems and conducting regular disaster recovery drills to ensure business continuity during unforeseen events.
Challenges:
- Preventing sophisticated fraud attempts that bypass security measures.
- Ensuring system availability in a 24/7 global financial ecosystem.
Best Practices:
- Encryption: Use end-to-end encryption to protect sensitive financial data.
- Real-time Monitoring: Continuously monitor for suspicious activity to detect fraudulent transactions early.
- Redundancy: Set up geographically distributed data centers to ensure availability even during a regional outage.
Retail: Protecting Customer Data and Ensuring Uptime for Online Shopping
In the retail sector, particularly for e-commerce businesses, confidentiality and availability are paramount. Customer payment information must be kept secure to avoid breaches that could expose credit card details and other personal data. Integrity ensures that transaction records are accurate, preventing issues like double charges or altered invoices that could erode customer trust.
Example:
An e-commerce company uses encryption to protect payment information and tokenization to obscure sensitive data during transactions, ensuring confidentiality. The retailer uses digital signatures to maintain integrity, ensuring that order details cannot be tampered with. To ensure availability, the business employs cloud-based redundancy, ensuring that their website remains accessible even during high-traffic periods or DDoS attacks.
Challenges:
- Preventing data breaches in online transactions.
- Ensuring the website remains online and functional during high-demand events (e.g., Black Friday sales).
Best Practices:
- Tokenization: Replace sensitive payment data with randomly generated tokens that can’t be traced back to real customer data.
- Intrusion Detection: Implement intrusion detection and prevention systems (IDPS) to identify malicious activity.
- Cloud Hosting: Use scalable cloud infrastructure to handle traffic spikes without downtime.
Key Takeaways from Industry Applications
Across industries, Confidentiality, Integrity, and Availability play crucial roles in protecting sensitive data, maintaining trust, and ensuring smooth operations. The implementation of these pillars, while essential for protecting against security threats, must be tailored to the specific needs of each sector.
- Healthcare focuses on ensuring patient data is secure, accurate, and available during emergencies.
- Finance emphasizes securing financial transactions, ensuring they are accurate, and maintaining uptime for customer access.
- Retail concentrates on protecting customer payment information and ensuring e-commerce platforms are always accessible.
READ: IoT vs Cybersecurity: 2026 Careers, Challenges, and Certifications
Common Threats and Which Pillars They Affect
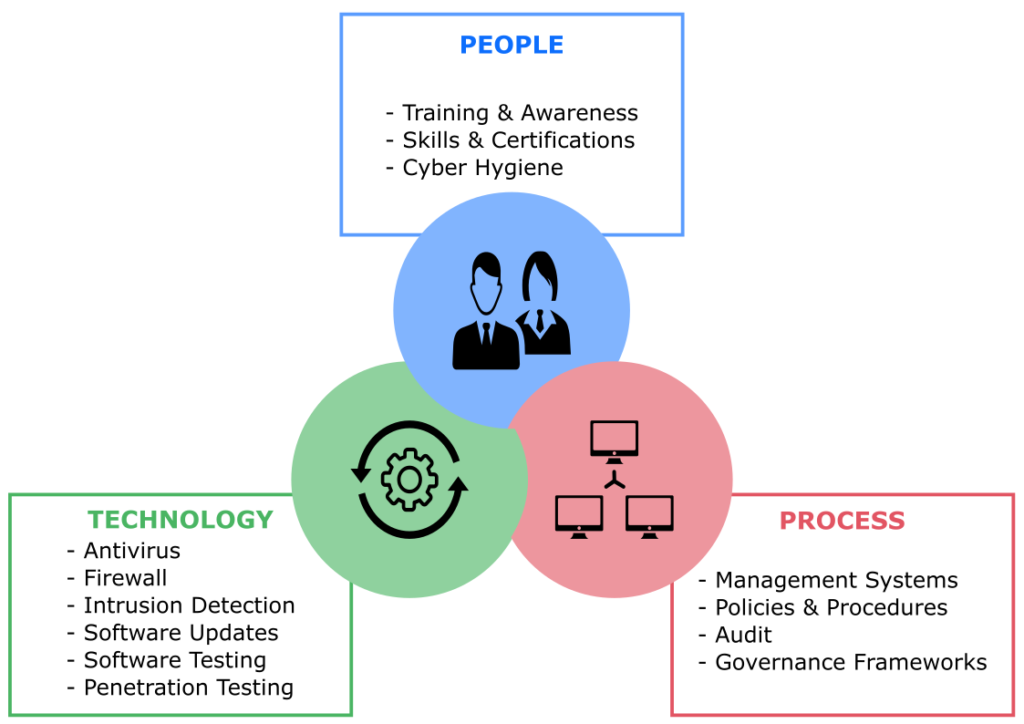
In the rapidly evolving landscape of cybersecurity, understanding how different threats impact the three pillars of information security, Confidentiality, Integrity, and Availability (CIA triad), is essential.
Cybercriminals employ a wide variety of tactics to exploit vulnerabilities in these pillars, leading to data breaches, system disruptions, and financial losses. Below, we explore several common threats and identify which pillars they most heavily affect.
1. Ransomware: Primarily Affects Availability
Ransomware attacks encrypt a victim’s data, making it inaccessible until a ransom is paid. These attacks primarily target availability, as they render data and systems unusable, disrupting business operations.
However, ransomware can also affect confidentiality and integrity. For example, if attackers exfiltrate data before encrypting it, they can use it for further exploitation, compromising confidentiality. Additionally, the encryption of critical files without proper decryption can lead to the corruption of data, compromising its integrity.
Real-World Example:
In 2020, the WannaCry ransomware attack affected thousands of organizations globally, including the UK’s National Health Service (NHS). The attack locked critical patient data, halting hospital services and emergency care. It disrupted operations and put lives at risk, highlighting how ransomware can devastate availability in highly sensitive environments like healthcare.
Best Practices for Mitigating Ransomware Impact:
- Backup Systems: Ensure frequent backups of critical data to minimize disruption during an attack.
- Endpoint Protection: Use advanced malware detection tools to prevent ransomware from gaining a foothold.
- User Education: Train employees to recognize phishing emails that often serve as the initial attack vector.
2. Insider Threats: Affects Confidentiality and Integrity
Insider threats are one of the most dangerous types of cyber threats. Whether through malicious intent or negligence, insiders, employees, contractors, or business partners can gain unauthorized access to sensitive data, compromising both confidentiality and integrity. These threats often occur when employees with privileged access manipulate, steal, or leak data for personal gain or to harm the organization.
Real-World Example:
In 2021, a former Tesla employee was accused of stealing proprietary data related to Tesla’s Autopilot system and sharing it with competitors. This incident not only compromised the confidentiality of Tesla’s intellectual property but also threatened the integrity of the company’s product development efforts.
Best Practices for Mitigating Insider Threats:
- Access Control: Implement least privilege access policies to limit what data employees can access based on their roles.
- Regular Audits: Conduct regular audits of data access logs and user activities to detect suspicious actions.
- Employee Training: Educate employees about security best practices and the risks of mishandling sensitive information.
3. DDoS Attacks: Primarily Affects Availability
Distributed Denial-of-Service (DDoS) attacks overwhelm a network or website with massive traffic, causing legitimate users to be unable to access services. These attacks primarily target availability, as they render online services and websites inaccessible.
While the direct impact is often on availability, DDoS attacks can also disrupt the availability of critical information by preventing users from accessing it, even if the underlying data is still secure and intact.
Real-World Example:
In 2016, the Dyn DDoS attack took down major internet platforms, including Twitter, Reddit, and Spotify, by targeting the Domain Name System (DNS) provider. The attack impacted millions of users and disrupted services for several hours, demonstrating the potential damage to availability in the digital world.
Best Practices for Mitigating DDoS Attacks:
- Traffic Filtering: Use advanced traffic filtering tools that can detect and mitigate large volumes of traffic.
- Cloud-Based Protection: Leverage cloud services like AWS Shield or Cloudflare to distribute traffic and prevent overload.
- Network Redundancy: Implement failover systems to ensure service continuity during a DDoS attack.
4. Data Breaches: Affects Confidentiality and Integrity
A data breach occurs when unauthorized individuals gain access to sensitive information, such as personal records, financial data, or intellectual property. Data breaches primarily target confidentiality, as they expose private data to unauthorized parties.
However, breaches can also affect integrity if attackers modify or corrupt the data during the breach, leading to misinformation or a loss of trust in the data.
Real-World Example:
In 2017, the Equifax data breach exposed personal information, including social security numbers, of over 147 million individuals. This breach not only compromised the confidentiality of sensitive data but also led to widespread concerns about the integrity of the data, as it was unclear how the stolen information would be used or manipulated.
Best Practices for Preventing Data Breaches:
- Encryption: Encrypt sensitive data both in transit and at rest to ensure that even if data is breached, it remains unreadable.
- Multi-Factor Authentication (MFA): Use MFA to protect accounts from unauthorized access.
- Data Minimization: Only collect and store the data necessary for business operations to reduce exposure in case of a breach.
5. Phishing Attacks: Affects Confidentiality and Integrity
Phishing attacks are social engineering attacks that deceive individuals into providing sensitive information, such as login credentials or financial details. These attacks primarily affect confidentiality, as attackers gain access to private data, but they can also affect integrity if stolen credentials are used to modify or tamper with systems or data.
Real-World Example:
In 2020, a sophisticated phishing attack targeted employees of a prominent US-based healthcare provider, leading to the theft of sensitive patient data. The attackers used legitimate-looking emails to trick employees into revealing their login credentials, which were then used to access and exfiltrate confidential medical records.
Best Practices for Preventing Phishing Attacks:
- Employee Education: Conduct regular training on how to recognize phishing emails and suspicious links.
- Email Filtering: Use advanced email filtering tools to detect and block phishing attempts.
- Zero-Trust Model: Implement a zero-trust security model where no user or device is trusted by default, even if it’s within the corporate network.
Best Practices for Implementing the Three Pillars of Information Security
Implementing the three pillars of information security, Confidentiality, Integrity, and Availability, requires a strategic and comprehensive approach that integrates both technical controls and organizational processes.
By embedding these pillars into every aspect of operations, organizations can protect sensitive data, ensure system reliability, and build trust with stakeholders. Below are some best practices to help organizations effectively implement and maintain the CIA triad across their security frameworks.
1. Comprehensive Security Policies and Procedures
A robust information security program starts with comprehensive policies that address all three pillars. These policies should outline how the organization handles sensitive data, ensures data integrity, and guarantees system availability. The policies must be clear, enforceable, and regularly updated to keep up with evolving security threats and technologies.
- Confidentiality Policies: Define who can access sensitive data and under what conditions. Implement role-based access control (RBAC) to ensure that only authorized personnel can access confidential information.
- Integrity Policies: Establish guidelines for maintaining data accuracy and preventing unauthorized modifications. Implement controls to monitor and detect unauthorized changes to critical data.
- Availability Policies: Ensure that data and systems are accessible when needed. Create disaster recovery and business continuity plans that outline how the organization will maintain availability during disruptions.
2. Multi-Layered Security Controls
To protect data and systems effectively, organizations should adopt a multi-layered security approach. This strategy involves using various security measures at different levels to protect against a wide range of threats. Each pillar of the CIA triad requires specific security technologies and tools:
- Confidentiality: Use encryption to protect sensitive data both in transit and at rest. Implement multi-factor authentication (MFA) to prevent unauthorized access, and ensure that access control policies are consistently enforced.
- Integrity: Employ digital signatures, hash functions, and versioning to detect and prevent unauthorized data modifications. Regularly conduct integrity checks to ensure data has not been tampered with.
- Availability: Implement redundancy and failover systems to ensure that critical systems remain operational during disruptions. Regularly back up data to ensure quick recovery, and use intrusion detection systems (IDS) to monitor for malicious activities that could disrupt availability.
3. Employee Training and Awareness
Human error remains one of the most significant vulnerabilities in cybersecurity. Employees must be educated about the importance of confidentiality, integrity, and availability, as well as how to recognize and respond to potential threats. Regular training and awareness programs are essential for building a security-conscious culture within the organization.
- Confidentiality Training: Teach employees about the importance of safeguarding personal and organizational data. Reinforce the need to avoid sharing sensitive information and recognize phishing attempts.
- Integrity Training: Explain the importance of data integrity and the potential consequences of making unauthorized changes to data. Encourage employees to follow proper data handling procedures and report any suspicious activities.
- Availability Training: Educate staff on the importance of system uptime and the steps to take in the event of system failures or data access issues. Simulate disaster recovery scenarios to prepare employees for real-world events.
4. Continuous Monitoring and Auditing
Implementing continuous monitoring and auditing practices is critical for maintaining all three pillars. Regular monitoring helps identify threats early, enabling organizations to take prompt action before breaches or disruptions occur. Auditing ensures that systems are being used appropriately and that data integrity is maintained.
- Confidentiality Monitoring: Monitor access to sensitive data to detect unauthorized access attempts. Use data loss prevention (DLP) tools to track and prevent unauthorized data transfers.
- Integrity Monitoring: Set up automated alerts to detect unauthorized changes to critical data. Regularly audit logs to verify that data has not been altered.
- Availability Monitoring: Implement uptime monitoring tools to track system availability in real time. Use automated failover systems to ensure service continuity in case of a system failure or DDoS attack.
5. Incident Response and Recovery Planning
Every organization should have a well-defined incident response plan that outlines the steps to take when a security breach or disruption occurs. The plan should address how to preserve confidentiality, integrity, and availability during and after an incident.
- Confidentiality: Immediately isolate compromised systems to prevent further data exposure. Notify affected individuals and organizations if their data has been breached, following legal and regulatory requirements.
- Integrity: Verify the integrity of all systems and data after an attack. If data has been tampered with, restore it from clean backups and audit all changes to ensure no further alterations have occurred.
- Availability: Activate disaster recovery protocols to restore access to critical systems as quickly as possible. Use backup systems to maintain availability during the recovery process.
6. Regular Vulnerability Assessments and Penetration Testing
Regular vulnerability assessments and penetration testing help identify weaknesses in security systems before attackers can exploit them. By simulating cyberattacks, organizations can assess how well their security measures address the three pillars and make necessary improvements.
- Confidentiality Testing: Test the robustness of encryption and access control systems to prevent unauthorized data access.
- Integrity Testing: Simulate attacks that could compromise data integrity, such as SQL injection or cross-site scripting (XSS) attacks, and verify the effectiveness of integrity checks.
- Availability Testing: Conduct DDoS simulations to test the resilience of systems under high traffic and identify potential weaknesses in availability.
Conclusion
The three pillars of information security, Confidentiality, Integrity, and Availability, form the backbone of any successful cybersecurity strategy. By ensuring that data remains secure, accurate, and accessible when needed, organizations can protect themselves from a wide range of cyber threats, from ransomware attacks to insider breaches.
Understanding and implementing the CIA triad is not just a technical requirement; it is a strategic approach that can drive trust, improve operational efficiency, and help organizations stay ahead of evolving threats.
Whether you are in healthcare, finance, or retail, these foundational principles are essential for safeguarding sensitive data, maintaining system uptime, and preventing malicious alterations to critical information.
The integration of these pillars into your organization’s security framework will help mitigate risks and ensure that your data remains protected against an increasingly complex threat landscape. Remember, a strong security posture is built on the foundational principles of the CIA triad, and continuous monitoring, training, and improvement are key to maintaining that security.
FAQ
What are the three main components of information security?
The three main components of information security are Confidentiality, Integrity, and Availability, commonly referred to as the CIA triad.
Confidentiality ensures that sensitive information is accessible only to authorized individuals.
Integrity guarantees that data remains accurate, consistent, and unaltered.
Availability ensures that systems and data are accessible when needed by authorized users.
Together, these components form the foundation for protecting organizational data and systems against cyber threats.
What are the three types of information security?
The three main types of information security focus on different aspects of protecting data:
Physical Security: Measures that protect physical assets, such as servers, data centers, and devices, from unauthorized access or damage.
Technical (Logical) Security: Security measures applied to digital systems, including encryption, firewalls, access controls, and intrusion detection systems.
Administrative Security: Policies, procedures, and training that govern how information is accessed, handled, and protected within an organization.
These three types work together to ensure comprehensive protection of sensitive information.
What is the 3 triad in cybersecurity?
The 3 triad in cybersecurity refers to the CIA triad: Confidentiality, Integrity, and Availability. It serves as the foundational framework for designing, implementing, and evaluating information security programs.
By addressing these three areas, organizations can safeguard sensitive data, prevent unauthorized access or modification, and maintain reliable access to critical systems. The CIA triad remains the most widely recognized model in cybersecurity and forms the basis for modern security standards and frameworks.
