
NIST Cybersecurity Framework Vs 800-53: A Comprehensive Comparison
NIST Cybersecurity Framework Vs 800-53: A Comprehensive Comparison
In 2026, organizations across various sectors face an ever-increasing need to bolster their cybersecurity posture as cyber threats continue to evolve. Two of the most widely recognized frameworks for managing these risks are the NIST Cybersecurity Framework (CSF) and NIST Special Publication 800-53 (SP 800-53). Both have their unique strengths, offering different approaches to safeguarding an organization’s data and information systems.
This article will explain deeply, the NIST Cybersecurity Framework Vs 800-53, helping organizations determine which framework best suits their cybersecurity needs. Whether you’re looking to adopt a high-level, flexible approach to risk management or implement detailed security controls, understanding the NIST CSF 2.0 to 800-53 mapping and the latest updates in NIST 800-53 Rev 5 will be crucial.
By the end of this guide, you’ll be equipped to make informed decisions on how to leverage these frameworks to strengthen your cybersecurity strategy, ensuring you stay ahead of emerging threats.

Start a Life-Changing Career in Cybersecurity Today
What is NIST Cybersecurity Framework (CSF)?
The NIST Cybersecurity Framework (CSF) was introduced as a voluntary guideline to help organizations of all sizes improve their ability to manage and reduce cybersecurity risk.
Developed by the National Institute of Standards and Technology, the CSF offers a high-level, flexible approach designed to be applicable to a wide variety of industries and organizational types. Unlike other frameworks that are highly prescriptive, NIST CSF allows for adaptability, which is one of its key strengths.
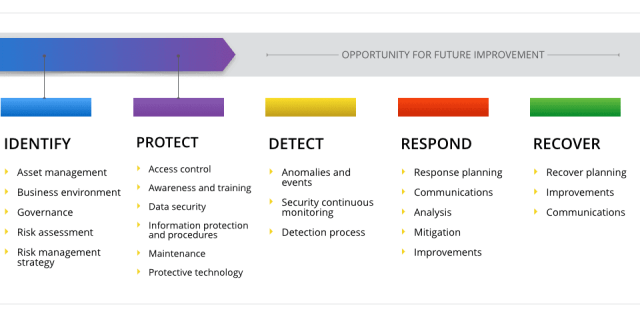
The framework is organized into five core functions that together form a comprehensive strategy for cybersecurity risk management:
- Identify: This function helps organizations understand their environment to manage cybersecurity risks effectively. It covers aspects like asset management, business environment, governance, and risk assessment.
- Protect: This function focuses on safeguarding critical infrastructure. It includes identity management, access control, data security, and protective technologies to ensure that services continue securely.
- Detect: The Detect function involves identifying cybersecurity events promptly. It includes continuous monitoring and detection processes that help organizations identify potential threats before they escalate.
- Respond: When a threat is detected, the Respond function ensures that organizations take the appropriate action to mitigate the damage. This includes response planning, communications, and incident analysis.
- Recover: In the event of a cybersecurity incident, this function focuses on recovery. It helps organizations restore capabilities and services while also ensuring continuous improvements to enhance resilience.
Flexibility and Customization of NIST CSF
One of the most notable aspects of the NIST CSF is its flexibility. Unlike highly prescriptive standards that require organizations to follow specific controls, NIST CSF offers a broader strategic framework that can be customized to meet an organization’s specific needs. This flexibility allows businesses, especially small to medium-sized enterprises (SMEs), to implement the framework without overextending their resources.
NIST CSF is designed to advance with increasing threats. As new vulnerabilities emerge and technologies advance, organizations can adapt their risk management practices accordingly, ensuring that their cybersecurity strategy remains robust and effective.
Global Applicability of NIST CSF
Though initially developed for U.S. critical infrastructure, NIST CSF has gained global recognition. Its voluntary, risk-based approach makes it applicable to organizations worldwide, even in regions outside of the U.S. Its simplicity and adaptability have made it a preferred choice for private sector organizations, government agencies, and even international corporations.
RELATED: Cybersecurity vs Cyber Forensics: Salary, Skills & Career Paths (2026 Guide)
What is NIST SP 800-53?
NIST Special Publication 800-53, often referred to as NIST SP 800-53, is a comprehensive catalog of security and privacy controls developed by the National Institute of Standards and Technology. While NIST CSF provides a flexible framework for managing cybersecurity risks, NIST SP 800-53 is a more detailed, prescriptive set of guidelines that primarily targets federal agencies and their contractors who are responsible for managing federal information systems.
The purpose of NIST SP 800-53 is to provide organizations with a thorough and mandatory set of security controls to protect sensitive information systems from a wide range of cybersecurity threats. This publication plays a vital role in ensuring that federal systems remain secure and compliant with regulations like the Federal Information Security Modernization Act (FISMA).
Additionally, its comprehensive approach has prompted many private sector organizations, especially those in critical industries like finance, healthcare, and energy, to voluntarily adopt it for more robust cybersecurity measures.
Key Components of NIST SP 800-53
NIST SP 800-53 is organized into 20 control families, each addressing specific aspects of cybersecurity and privacy. These control families cover a broad spectrum of security measures, from basic protections to advanced defense strategies. Below are examples of key control families:
- Access Control (AC): Ensures that only authorized individuals can access sensitive information and systems. This includes the management of identities and authentication processes.
- Incident Response (IR): Provides guidelines for responding to cybersecurity incidents, ensuring that organizations have the tools and processes in place to react to and recover from breaches.
- Audit and Accountability (AU): Ensures that systems are auditable, with mechanisms in place to track user actions and detect unauthorized access or activities.
- Risk Assessment (RA): Provides guidelines for assessing and managing risks within the organization, ensuring that security measures are aligned with the organization’s risk profile.
- System and Communications Protection (SC): Focuses on securing the systems and networks that are essential to an organization’s operations, preventing unauthorized access and safeguarding data integrity.
Each of these control families contains multiple detailed controls that define specific actions and requirements to secure federal information systems.
Comprehensive and Prescriptive Nature
Unlike the high-level guidance provided by NIST CSF, NIST SP 800-53 is highly detailed and prescriptive. The framework offers specific security controls that must be implemented in order to ensure comprehensive protection.
With over 1,000 individual security controls, it is one of the most thorough cybersecurity frameworks available. This level of detail is necessary for ensuring the security and privacy of information systems, particularly for those that handle sensitive federal data.
NIST SP 800-53 is updated regularly to address new and emerging threats, and each version of the publication incorporates lessons learned from past incidents and technological advancements. The latest update, NIST 800-53 Revision 5, brings significant updates to the framework, incorporating more comprehensive guidance on issues such as privacy, supply chain risk management, and resilience.
Key Differences Between NIST Cybersecurity Framework (CSF) and NIST SP 800-53
Though both the NIST Cybersecurity Framework (CSF) and NIST SP 800-53 aim to enhance an organization’s cybersecurity posture, they do so in distinct ways that make them suitable for different use cases. Understanding their key differences is crucial for organizations when choosing the right framework for their needs.
1. Flexibility vs. Prescriptiveness
- NIST CSF is highly flexible and designed to be adaptable to organizations of all sizes and sectors. It provides a high-level, strategic framework that allows organizations to tailor their cybersecurity practices based on their unique risk profiles. This flexibility makes it especially suitable for small to medium-sized enterprises (SMEs) and organizations that require a general framework for cybersecurity risk management.
- NIST SP 800-53, in contrast, is much more prescriptive. It provides a detailed set of security controls that organizations must implement to safeguard their information systems. These controls are mandatory for federal agencies and contractors handling federal data, ensuring that all federal systems meet a consistent and rigorous set of security standards. While some private organizations voluntarily adopt this framework, its comprehensive nature requires greater resources to implement effectively.
2. Voluntary vs. Mandatory Compliance
- NIST CSF is voluntary and meant to be used by organizations that want to improve their cybersecurity posture. Organizations can adopt the framework as a whole or tailor its components based on their specific needs and capabilities. The framework’s voluntary nature allows it to be more accessible to a wide range of organizations, from small businesses to large corporations.
- NIST SP 800-53, on the other hand, is mandatory for federal agencies and contractors working with the U.S. government. Compliance with FISMA (Federal Information Security Modernization Act) requires these entities to implement the security controls outlined in NIST SP 800-53. Although it is not mandatory for private-sector organizations, many choose to adopt it for its thoroughness and detailed approach to cybersecurity.
3. Strategic Framework vs. Detailed Security Controls
- NIST CSF focuses on strategic cybersecurity risk management. It emphasizes the five core functions, Identify, Protect, Detect, Respond, and Recover, to guide organizations in managing cybersecurity risks at a high level. The framework is intended to be adapted to the unique risk environment of each organization, making it ideal for organizations looking for general guidelines rather than specific, actionable controls.
- NIST SP 800-53 provides detailed security controls designed to be implemented to protect federal systems from a wide range of threats. The 20 control families cover everything from access control to incident response and system integrity, with each control offering specific requirements that organizations must follow. NIST SP 800-53 is ideal for organizations that require specific, actionable guidelines to secure their systems, particularly those that handle sensitive data.
4. Global Applicability vs. Federal Mandate
- NIST CSF is globally recognized and applicable to organizations across various sectors worldwide. Its voluntary nature and flexibility make it suitable for private-sector businesses, critical infrastructure operators, and government agencies outside the U.S. It’s designed to be adaptable to international contexts, ensuring that organizations can implement it regardless of their geographic location.
- NIST SP 800-53, while also widely adopted in some private sectors, is primarily U.S.-focused. It was created to meet the needs of federal agencies and contractors working with federal information systems. The mandatory compliance requirement ensures that all federal systems adhere to a consistent security standard, which is crucial for maintaining national security.
5. Implementation Complexity and Resources
- NIST CSF is less complex to implement, as it provides high-level guidance that organizations can adapt to their unique needs. Smaller organizations or those with limited resources can start by focusing on the core functions and progressively integrate more components as needed. The framework’s flexibility makes it accessible to organizations with varying levels of cybersecurity maturity.
- NIST SP 800-53, in contrast, requires significant resources to implement. Due to the extensive nature of the controls, organizations must dedicate considerable time and effort to fully integrate them into their systems. Federal agencies and contractors are required to implement all applicable controls, which can be a complex and resource-intensive process.
ALSO READ: Cybersecurity Salary: A Comprehensive Guide
The Role of NIST CSF 2.0 and NIST SP 800-53 Rev 5
As organizations adapt to an increasingly complex and dynamic cybersecurity environment, both the NIST Cybersecurity Framework (CSF) and NIST SP 800-53 have undergone significant updates to enhance their relevance and effectiveness. The NIST CSF 2.0 and NIST SP 800-53 Rev 5 are the most recent versions of these frameworks, and they reflect the growing importance of addressing privacy, supply chain risks, and resilience.
NIST CSF 2.0 Updates: A Step Forward in Flexibility and Privacy
In NIST CSF 2.0, there is a strong emphasis on privacy and supply chain risk management. This version expands the framework’s scope to better address emerging challenges in these areas. As organizations increasingly rely on third-party vendors and partners, managing the risks that come from these external relationships has become a priority. Supply chain risk management is now a key component of the updated framework, guiding organizations to assess and mitigate risks related to their suppliers and vendors.
The introduction of privacy controls in CSF 2.0 also reflects growing concerns over data protection, especially with stringent regulations like GDPR in the EU and CCPA in California. These controls help organizations build privacy protections into their cybersecurity strategies, ensuring that they meet the needs of both cybersecurity and data privacy standards.
NIST CSF 2.0 also improves upon its mapping to other frameworks, making it easier for organizations to integrate it with existing cybersecurity practices, including NIST SP 800-53. The integration between the two frameworks helps organizations establish a more comprehensive cybersecurity posture that aligns with both strategic and detailed requirements.
NIST SP 800-53 Rev 5: Key Updates and Features
The latest revision of NIST SP 800-53, Revision 5 (Rev 5), introduces significant updates that enhance its ability to address contemporary cybersecurity challenges. Some of the key updates include:
- Increased Focus on Privacy:
NIST SP 800-53 Rev 5 integrates privacy controls more thoroughly within the security control families, reflecting the importance of data protection in modern cybersecurity. This update ensures that organizations can better manage both cybersecurity risks and privacy concerns, aligning with global privacy regulations.
- Supply Chain Risk Management:
A critical addition in Rev 5 is a stronger emphasis on supply chain risk management, addressing vulnerabilities that may be introduced by third-party vendors. This update is in response to high-profile cyberattacks, such as the SolarWinds breach, where hackers gained access to systems through compromised software updates.
- Updated Control Families and Controls:
The control families in Rev 5 have been updated to reflect evolving threats and technological advancements. The update includes expanded guidance on cloud security, data integrity, and incident response, helping organizations build resilience and respond effectively to threats.
- Comprehensive and Scalable Controls:
NIST SP 800-53 Rev 5 remains one of the most comprehensive cybersecurity frameworks available. It continues to provide detailed, prescriptive controls, which are especially beneficial for large organizations or federal contractors that must ensure regulatory compliance with standards like FISMA.
NIST CSF 2.0 to 800-53 Mapping: How They Complement Each Other
While NIST CSF provides the strategic vision, NIST SP 800-53 offers the detailed, actionable steps required to implement cybersecurity measures. The integration of NIST CSF 2.0 with NIST SP 800-53 Rev 5 enables organizations to benefit from both frameworks.
For instance:
- NIST CSF’s Protect function aligns with multiple NIST 800-53 control families such as Access Control (AC), System and Communications Protection (SC), and Data Integrity (DI).
- NIST CSF’s Identify function corresponds with NIST 800-53’s emphasis on Risk Assessment (RA) and Governance controls.
By integrating both frameworks, organizations can develop a holistic approach to managing cybersecurity risks. The flexibility of NIST CSF combined with the comprehensive controls of NIST SP 800-53 creates a powerful cybersecurity strategy that is both adaptable and thorough.
SEE MORE: Cybersecurity vs UX Design: Which Career Fits Your Strengths (2025 Guide)
How to Integrate NIST Cybersecurity Framework with NIST SP 800-53
Integrating the NIST Cybersecurity Framework (CSF) with NIST SP 800-53 provides organizations with a comprehensive approach to managing cybersecurity risks. While NIST CSF offers high-level strategic guidance, NIST SP 800-53 provides the detailed, actionable controls that are often necessary for federal compliance or complex cybersecurity environments. By combining these two frameworks, organizations can achieve both strategic oversight and tactical precision.
1. Aligning Core Functions with Control Families
One of the most effective ways to integrate NIST CSF with NIST SP 800-53 is by aligning the core functions of CSF with the control families outlined in NIST SP 800-53. Each of the five core functions in CSF, Identify, Protect, Detect, Respond, and Recover, can be mapped to specific control families in SP 800-53. This integration ensures that organizations maintain both strategic flexibility and detailed security controls in their cybersecurity strategy.
For example:
- Identify (CSF): The Risk Assessment (RA) and System and Services Acquisition (SA) control families in SP 800-53 align with this function, helping organizations identify potential risks and assess their systems.
- Protect (CSF): This maps to several control families, such as Access Control (AC), Data Protection (DP), and System and Communications Protection (SC) in SP 800-53, ensuring that safeguards are in place to protect critical systems and data.
- Detect (CSF): The Continuous Monitoring (CM) and Incident Response (IR) control families in SP 800-53 support this function by enabling organizations to detect cybersecurity events promptly.
- Respond (CSF): Control families like Incident Response (IR), Contingency Planning (CP), and System Recovery (SR) ensure that organizations can respond quickly and effectively to a cybersecurity incident.
- Recover (CSF): The System and Communications Protection (SC) and Contingency Planning (CP) control families in SP 800-53 can be used to ensure recovery processes are in place to restore systems and data.
By using NIST CSF as the strategic framework and NIST SP 800-53 for detailed controls, organizations create a strong cybersecurity posture that’s both comprehensive and scalable.
2. Benefits of Integrating NIST CSF and NIST SP 800-53
Combining the strengths of both frameworks helps organizations in several ways:
- Comprehensive Coverage: By integrating CSF’s broad, risk-based approach with SP 800-53’s detailed, actionable controls, organizations can ensure that they cover all aspects of cybersecurity, from high-level strategy to granular security measures.
- Scalability and Flexibility: NIST CSF’s adaptability makes it a great fit for organizations of all sizes. It allows smaller organizations to use a strategic approach without being overwhelmed by the complexity of SP 800-53, while still enabling larger organizations to implement the detailed controls necessary for robust cybersecurity.
- Improved Compliance: Organizations that need to comply with federal regulations can use NIST SP 800-53 to meet compliance requirements, while still leveraging NIST CSF to maintain flexibility and adaptability in their cybersecurity practices.
- Enhanced Risk Management: The integration of risk management functions from CSF with the security controls from SP 800-53 provides organizations with a comprehensive system to manage risks and respond to threats effectively.
3. Practical Integration: Case Studies
Many organizations have already successfully integrated NIST CSF with NIST SP 800-53 to strengthen their cybersecurity efforts. Here are a few examples:
- Financial Institutions: Banks and other financial organizations use the flexibility of NIST CSF to manage high-level risks, while adopting the detailed controls of NIST SP 800-53 to ensure the security of sensitive financial data and meet regulatory requirements.
- Healthcare Organizations: Hospitals and healthcare providers leverage NIST CSF to manage overall cybersecurity risk, while using NIST SP 800-53 to ensure compliance with healthcare regulations such as HIPAA and to protect patient data.
- Government Contractors: Contractors working with federal agencies adopt NIST CSF to create a flexible cybersecurity strategy while implementing NIST SP 800-53 controls to meet the stringent security requirements for handling federal data.
4. Tools and Resources for Integration
Several tools and resources can assist organizations in integrating NIST CSF and NIST SP 800-53:
- NIST 800-53 Revision 5 (Rev 5) provides updated guidance that aligns with CSF, making integration easier.
- Security and Risk Management Tools: Tools like risk management platforms and compliance management software can help automate and streamline the integration process by mapping CSF functions to SP 800-53 controls.
- Training and Awareness: Organizations should train their cybersecurity teams on both frameworks to ensure a unified approach to managing cybersecurity risks and implementing controls.
ALSO: Enterprise Security vs Cybersecurity: What You Need to Know in 2026
NIST 800-53 Rev 5: Key Features and Controls List
NIST SP 800-53 Revision 5 (Rev 5) represents the most recent update to the comprehensive catalog of security and privacy controls for federal information systems. This latest revision incorporates several critical updates to reflect the evolving nature of cybersecurity threats and technological advancements. Notably, it emphasizes the integration of privacy controls, supply chain risk management, and an overall enhanced focus on resilience.
Key Features of NIST 800-53 Rev 5
- Privacy Controls Integration:
One of the standout features in Rev 5 is the integration of privacy controls within the security control families. This addition underscores the increasing importance of data privacy in today’s cyber landscape. Organizations are now required to implement privacy protections alongside traditional cybersecurity measures, aligning with global privacy regulations such as GDPR and CCPA.
- Supply Chain Risk Management:
Following the rise in supply chain-related cyber incidents, such as the SolarWinds attack, Rev 5 places a stronger emphasis on supply chain risk management. This update introduces new controls and enhancements to help organizations manage risks associated with third-party vendors. Ensuring that external partners don’t introduce vulnerabilities into the organization’s systems is now a crucial aspect of cybersecurity strategy.
- Expanded Control Families:
NIST 800-53 Rev 5 updates the control families to include new and enhanced controls that address emerging technologies and complex security requirements. This includes expanded guidance on topics such as cloud security, data integrity, and incident response, helping organizations improve their overall cybersecurity posture.
- Resilience and Organizational Preparedness:
Rev 5 emphasizes the need for organizations to be prepared for and resilient to cybersecurity incidents. This includes a focus on incident response capabilities, business continuity, and disaster recovery. The goal is not just to prevent incidents but to ensure organizations can quickly recover and continue operating in the face of a breach.
- Universal Applicability:
While earlier revisions of NIST 800-53 were focused primarily on federal systems, Rev 5 has made strides to be more applicable across all sectors, including the private sector. This broader applicability ensures that NIST 800-53 Rev 5 is relevant to industries beyond the federal government, including finance, healthcare, and energy, which are increasingly adopting these standards for their cybersecurity frameworks.
NIST 800-53 Rev 5 Controls List
NIST 800-53 Rev 5 consists of a detailed list of over 1,000 security and privacy controls, divided into 20 control families. Below are some of the core control families:
- Access Control (AC):
This family includes controls to manage and restrict access to sensitive systems and data. Key controls include identity management, authentication protocols, and user access monitoring.
- Incident Response (IR):
This family focuses on how organizations should prepare for, respond to, and recover from cybersecurity incidents. Key controls cover incident detection, response planning, communication strategies, and post-incident analysis.
- Audit and Accountability (AU):
Controls in this family ensure that organizations can track user actions and system activity, making it easier to detect and analyze unauthorized actions. Key controls include event logging, audit trails, and system monitoring.
- Risk Assessment (RA):
This family includes controls for identifying, assessing, and prioritizing risks to information systems. Key controls cover vulnerability management, risk analysis, and threat intelligence.
- System and Communications Protection (SC):
Controls here are aimed at protecting the organization’s systems and networks from external threats. Key controls include firewalls, intrusion detection systems, and encryption protocols.
- Supply Chain Risk Management (SR):
New to Rev 5, this family addresses the risk posed by third-party vendors. Key controls include vendor risk assessments, contractual security requirements, and continuous monitoring of supply chain partners.
- Privacy (PI):
This family focuses on protecting personal and sensitive information. Controls here ensure compliance with data protection laws and include data encryption, data minimization, and data retention policies.
- System and Services Acquisition (SA):
This family includes controls to ensure that third-party services and products meet the organization’s security requirements. Key controls cover vendor selection, contractual obligations, and service-level agreements.
- Personnel Security (PS):
Controls in this family aim to protect the organization from internal threats. Key controls include background checks, security training, and termination procedures.
How NIST 800-53 Rev 5 Enhances Cybersecurity Practices
The updates in NIST 800-53 Rev 5 are designed to ensure that the framework remains relevant and effective in addressing modern cybersecurity challenges. The integration of privacy controls is particularly timely, as organizations face increasing scrutiny regarding the protection of personal data. The focus on supply chain risk management reflects the growing recognition that external partners pose significant risks to an organization’s security.
Additionally, the expanded guidance on cloud security and data integrity helps organizations secure the technologies that are becoming increasingly critical to their operations. The enhanced focus on resilience and organizational preparedness ensures that organizations are not only able to prevent incidents but are also well-equipped to respond and recover quickly when breaches occur.
SEE: Will Cybersecurity Be Automated By 2026?
Choosing the Right Framework for Your Organization
Selecting the appropriate cybersecurity framework is a critical decision for any organization, as it directly impacts your ability to protect data, comply with regulations, and manage cybersecurity risks effectively. When it comes to NIST Cybersecurity Framework (CSF) and NIST SP 800-53, the choice largely depends on the size of your organization, your industry, and whether you need to meet regulatory requirements.
Factors to Consider
Choosing between NIST CSF and NIST SP 800-53 requires a careful evaluation of several factors:
- Industry and Sector
- Federal Agencies and Contractors: If your organization is a federal agency or a contractor working with federal systems, NIST SP 800-53 is mandatory. It provides the detailed controls needed to meet compliance standards such as FISMA (Federal Information Security Modernization Act).
- Private Sector Organizations: For private-sector organizations, particularly in critical infrastructure, finance, healthcare, and other regulated industries, NIST SP 800-53 may be a preferred choice for those seeking detailed security controls to comply with industry-specific regulations. However, many of these organizations may also adopt NIST CSF for its more flexible, strategic approach to cybersecurity.
- Global Organizations: NIST CSF is highly adaptable and globally recognized, making it an excellent option for international organizations or those with diverse cybersecurity needs across multiple regions.
- Federal Agencies and Contractors: If your organization is a federal agency or a contractor working with federal systems, NIST SP 800-53 is mandatory. It provides the detailed controls needed to meet compliance standards such as FISMA (Federal Information Security Modernization Act).
- Size of the Organization
- Small to Medium-Sized Organizations: Smaller organizations often find NIST CSF more practical due to its flexibility. It allows them to start with high-level guidelines and gradually scale their cybersecurity measures as the organization grows. NIST CSF enables smaller organizations to implement risk-based strategies without requiring extensive resources for complex security controls.
- Large Organizations: Larger enterprises, especially those with complex IT environments or those in need of comprehensive security measures, may prefer NIST SP 800-53. Its detailed controls cover every aspect of information security, ensuring that no area is overlooked. These organizations will benefit from the rigorous nature of NIST SP 800-53 for maintaining high security standards.
- Small to Medium-Sized Organizations: Smaller organizations often find NIST CSF more practical due to its flexibility. It allows them to start with high-level guidelines and gradually scale their cybersecurity measures as the organization grows. NIST CSF enables smaller organizations to implement risk-based strategies without requiring extensive resources for complex security controls.
- Compliance Requirements
- Regulatory Compliance: Organizations that must comply with specific regulations (e.g., HIPAA, PCI DSS, SOX) will find NIST SP 800-53 particularly useful, as it provides detailed guidance on how to meet compliance standards. NIST CSF, while also supporting compliance through its risk management approach, is more general and may require integration with other standards for full regulatory alignment.
- Federal Contracts: If your organization deals with federal contracts, compliance with NIST SP 800-53 is a contractual obligation. For example, contractors handling federal data must adhere to the standards laid out in SP 800-53 to ensure data security and privacy protection.
- Regulatory Compliance: Organizations that must comply with specific regulations (e.g., HIPAA, PCI DSS, SOX) will find NIST SP 800-53 particularly useful, as it provides detailed guidance on how to meet compliance standards. NIST CSF, while also supporting compliance through its risk management approach, is more general and may require integration with other standards for full regulatory alignment.
Benefits of NIST CSF for Small to Medium-Sized Organizations
NIST CSF is particularly advantageous for small to medium-sized organizations that may have limited resources. Here’s why:
- Flexibility and Scalability: NIST CSF allows organizations to start small and build out their cybersecurity practices over time. The framework’s high-level guidelines make it easy for organizations to implement in phases, which is ideal for smaller teams with limited resources.
- Risk-Based Approach: The framework’s focus on risk management enables organizations to prioritize their cybersecurity efforts based on their unique risks, rather than trying to meet a one-size-fits-all set of controls.
- Ease of Implementation: With its simple structure and clear functions, NIST CSF is easy for smaller organizations to understand and apply, making it a practical choice for organizations new to formal cybersecurity practices.
Benefits of NIST SP 800-53 for Federal Agencies and Large Organizations
For federal agencies and large organizations, NIST SP 800-53 offers a more comprehensive and structured approach to managing cybersecurity. Here are some key benefits:
- Comprehensive Security Controls: NIST SP 800-53 provides a detailed set of controls that cover every aspect of information security, from access control to incident response and privacy protections. This thorough approach ensures that all security needs are met, particularly for organizations with complex IT systems.
- Regulatory Compliance: NIST SP 800-53 ensures compliance with FISMA and other federal security standards, making it indispensable for federal agencies and contractors. For large organizations in regulated industries, adopting NIST SP 800-53 helps meet industry-specific compliance requirements.
- Robust Security Posture: The depth and specificity of NIST SP 800-53 controls provide a strong foundation for building and maintaining a robust cybersecurity program. This is crucial for organizations handling sensitive data or operating in high-risk environments.
Mixed Approach: How NIST CSF and NIST SP 800-53 Work Together
Organizations don’t always have to choose between NIST CSF and NIST SP 800-53. In fact, many organizations can benefit from integrating both frameworks:
- NIST CSF provides the strategic, risk-based approach to managing cybersecurity, offering flexibility and high-level guidance that can be adapted to any organization.
- NIST SP 800-53 offers detailed security controls that can be applied to areas of the organization that require a more specific, prescriptive approach to security.
For example, an organization could use NIST CSF for overall risk management and cybersecurity strategy, while NIST SP 800-53 is used to implement detailed security controls for sensitive systems or regulatory compliance.
Conclusion
Choosing the right cybersecurity framework is crucial for any organization looking to strengthen its defenses against an ever-evolving landscape of cyber threats. NIST CSF and NIST SP 800-53 are both powerful tools, but they serve different purposes and cater to different needs.
- NIST CSF offers a flexible, high-level framework for managing cybersecurity risks, making it ideal for organizations of all sizes, especially those looking for a strategic, adaptable approach to cybersecurity.
- NIST SP 800-53, on the other hand, provides a detailed set of mandatory security controls, making it essential for federal agencies and contractors that need to meet FISMA compliance, or for large organizations with complex cybersecurity needs.
The latest updates in NIST CSF 2.0 and NIST 800-53 Rev 5, which emphasize privacy, supply chain risk management, and organizational resilience, ensure these frameworks remain relevant and effective in addressing the growing range of cybersecurity challenges.
Integrating both frameworks allows organizations to leverage the strategic flexibility of NIST CSF while implementing the specific security controls offered by NIST SP 800-53, creating a comprehensive cybersecurity strategy that addresses both high-level goals and detailed implementation.
By carefully assessing your organization’s size, industry, and compliance needs, you can choose the framework, or combination of frameworks, that best suits your cybersecurity objectives and ensures long-term resilience.
FAQ
What are the 5 NIST Cybersecurity Frameworks?
NIST has developed several frameworks to guide organizations in improving their cybersecurity practices. The 5 key frameworks include:
NIST Cybersecurity Framework (CSF): Provides a flexible, high-level approach to managing cybersecurity risks through five core functions: Identify, Protect, Detect, Respond, and Recover.
NIST 800-53: A catalog of security and privacy controls specifically for federal information systems and contractors, providing detailed guidance for securing sensitive data and systems.
NIST 800-171: Focuses on protecting Controlled Unclassified Information (CUI) in nonfederal systems and organizations. It’s mainly aimed at contractors and entities working with the federal government.
NIST 800-82: Focuses on securing industrial control systems (ICS), which are critical for infrastructure sectors like energy, water, and transportation.
NIST 800-30: Provides a guide for conducting risk assessments to help organizations identify, estimate, and prioritize risks to their information systems.
What is the difference between NIST 800-171 and NIST 800-53?
NIST 800-171 and NIST 800-53 both provide cybersecurity controls, but they cater to different audiences and contexts:
NIST 800-53 is comprehensive and intended for federal agencies and their contractors, covering a wide range of security and privacy controls across 20 control families.
NIST 800-171, on the other hand, is a simplified version derived from NIST 800-53, specifically designed for nonfederal organizations handling Controlled Unclassified Information (CUI). It is more focused and streamlined than NIST 800-53, making it accessible for smaller entities that need to comply with federal security requirements.
What is the difference between NIST Cybersecurity Framework 2.0 and 800-53?
The main difference between NIST Cybersecurity Framework 2.0 (CSF) and NIST 800-53 lies in their purpose, structure, and level of detail:
NIST CSF 2.0 is a high-level, voluntary framework designed to help organizations manage cybersecurity risks through five core functions (Identify, Protect, Detect, Respond, Recover). It is flexible and adaptable, allowing organizations to tailor it to their needs, and is applicable to a wide range of sectors and sizes.
NIST 800-53 is a detailed, mandatory set of security controls for federal systems and contractors. It provides specific security controls across 20 control families, covering everything from access control to incident response. It’s prescriptive, making it more suitable for organizations that need to comply with federal regulations or require a comprehensive set of controls.
Is NIST 800-53 mandatory?
Yes, NIST 800-53 is mandatory for federal agencies and contractors handling federal information systems. It ensures that all federal systems comply with the Federal Information Security Modernization Act (FISMA).
For federal agencies and contractors, adhering to the guidelines set forth in NIST 800-53 is not optional but a legal requirement. However, private-sector organizations often adopt NIST 800-53 voluntarily, especially if they operate in regulated industries or handle sensitive data.
