
IoT vs Cybersecurity: 2026 Careers, Challenges, and Certifications
IoT vs Cybersecurity: 2026 Careers, Challenges, and Certifications
The Internet of Things (IoT) is no longer a futuristic concept; it’s a rapidly expanding ecosystem that connects everyday devices, from smart thermostats to industrial sensors, into a seamless digital network.
By 2025, there will be an estimated 75 billion connected devices worldwide, driving efficiency, automation, and new opportunities across industries. Yet, this unprecedented connectivity brings an equally unprecedented risk: every IoT device can be a potential entry point for cyberattacks.
As organizations integrate IoT solutions, understanding IoT vs cybersecurity becomes critical. While IoT focuses on connectivity and automation, cybersecurity ensures the protection of data, systems, and networks from advanced threats. Professionals in both domains are in high demand, with salaries reflecting the critical nature of their roles.
This guide explores the intersection of IoT and cybersecurity, providing insights on career paths, certifications, emerging technologies, including blockchain, and practical steps for securing IoT systems.
Whether you’re evaluating IoT or cyber security which is easy, exploring hands-on IoT cybersecurity projects, or considering specialized IoT cybersecurity courses, this article will equip you with the knowledge to navigate this complex, high-growth field.

Start a Life-Changing Career in Cybersecurity Today
Understanding IoT and Its Role in Modern Technology
The Internet of Things (IoT) refers to the network of physical objects, devices, vehicles, buildings, and other items, equipped with sensors, software, and connectivity capabilities that allow them to collect, share, and analyze data. By linking the physical and digital worlds, IoT enables real-time insights, automation, and efficiency improvements across multiple sectors.
What Is IoT?
IoT devices range from consumer products like smart home assistants and fitness trackers to industrial equipment and medical monitoring systems. These devices communicate with each other and central systems, allowing for streamlined operations, predictive analytics, and improved decision-making.
For example, a smart thermostat can adjust heating based on occupancy patterns, while industrial sensors can monitor machinery performance to prevent costly downtime.
The application of IoT is vast: smart cities leverage sensors to optimize traffic and energy usage, healthcare facilities monitor patient vitals remotely, and manufacturers improve production efficiency with connected machinery. Such innovations demonstrate the transformative potential of IoT when implemented strategically.
Growth and Economic Impact
IoT adoption has accelerated rapidly, with global connected devices projected to surpass 75 billion by 2025. This expansion drives substantial economic benefits. Companies leveraging IoT can reduce operational costs, optimize resource utilization, and create new revenue streams.
Logistics firms, for instance, use IoT-enabled tracking to improve supply chain visibility, while energy providers deploy smart grids and meters to manage consumption and integrate renewable sources effectively.
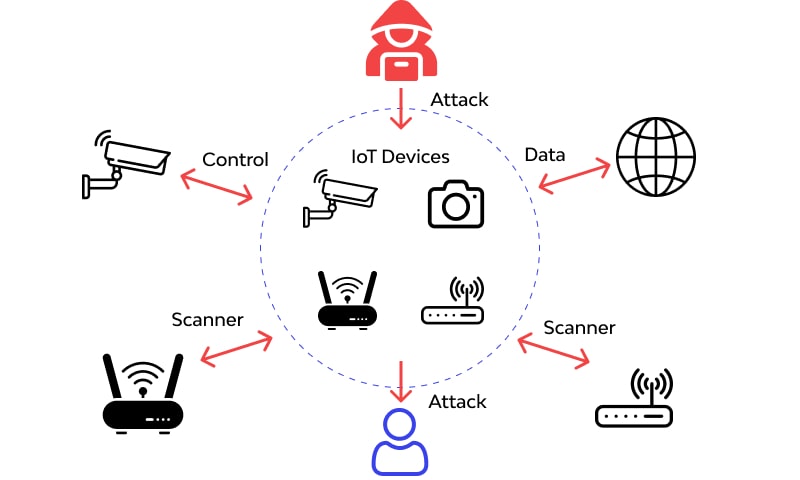
However, as IoT devices proliferate, security becomes more complex. Each connected device introduces a potential vulnerability, making robust cybersecurity an essential component of IoT deployment. Without proper safeguards, breaches can compromise personal data, disrupt industrial operations, and even endanger lives in critical sectors like healthcare.
IoT Cybersecurity Explained
As the adoption of IoT devices grows, so does the need to protect them from cyber threats. IoT cybersecurity refers to the practices, tools, and frameworks designed to secure connected devices, networks, and data.
Unlike traditional cybersecurity, which primarily focuses on software and network protection, IoT cybersecurity must account for physical devices that operate in diverse and sometimes uncontrolled environments.
Defining IoT Cybersecurity
IoT cybersecurity encompasses all measures taken to prevent unauthorized access, data breaches, and operational disruptions across IoT ecosystems. This includes implementing strong authentication protocols, encrypting communications, and continuously monitoring devices for anomalies.
Because IoT devices often handle sensitive data, such as patient health information in hospitals or operational metrics in industrial settings, the stakes are particularly high.
Key Challenges in Securing IoT Devices
Securing IoT devices is uniquely complex due to several factors:
- Outdated Software: Many devices run legacy systems or outdated firmware, leaving them vulnerable to known exploits.
- Weak Passwords and Authentication: Default credentials or simple passwords are common, making brute-force attacks easier.
- Physical Access Risks: Devices installed in unmonitored or public areas can be tampered with or stolen.
- Device Diversity: A single IoT ecosystem may include hundreds of device types with different software, hardware, and communication protocols, complicating uniform security measures.
- Supply Chain Vulnerabilities: Security breaches can occur during manufacturing or distribution, even before deployment.
High-profile incidents, such as the Mirai botnet attack in 2016 and the Stuxnet worm targeting industrial systems, highlight the potential consequences of compromised IoT devices, from massive distributed denial-of-service (DDoS) attacks to industrial sabotage.
Emerging Solutions and Technologies
To mitigate these risks, organizations are implementing innovative solutions and adopting new technologies:
- AI and Machine Learning: These tools analyze device behavior to detect anomalies and predict potential threats in real time.
- Blockchain Integration: IoT and Cyber Security, including Blockchain Technology, provides secure, transparent data exchange, making tampering more difficult.
- Zero Trust Security Models: Treat every device and user as untrusted by default, requiring continuous verification.
- Edge Computing: Processing data closer to where it is generated reduces latency and limits exposure to network-based attacks.
- Automated Incident Response: Rapid isolation of compromised devices prevents attacks from spreading across networks.
These measures are increasingly integrated into IoT cybersecurity projects, ensuring that connected systems remain resilient and secure as IoT adoption scales across industries.
RELATED: Enterprise Security vs Cybersecurity: What You Need to Know in 2026
IoT vs Cybersecurity Career Path Comparison
With the rapid expansion of connected devices and the rising threats, careers in IoT and cybersecurity are increasingly lucrative and in demand. Understanding the differences between these career paths can help professionals make informed decisions about education, skill development, and certifications.
Job Roles and Opportunities
IoT and cybersecurity offer distinct yet overlapping opportunities:
- IoT Roles: Positions include IoT developer, IoT security specialist, and IoT systems engineer. These roles focus on designing, deploying, and securing connected devices across industries such as healthcare, manufacturing, and smart cities.
- Cybersecurity Roles: Careers include cybersecurity analyst, penetration tester, security consultant, and incident response specialist. Professionals safeguard networks, software, and data from cyber threats across all sectors.
The demand for both paths is rising, but the focus differs: IoT roles require deep understanding of hardware-software integration and IoT protocols, whereas cybersecurity careers prioritize threat analysis, network defense, and compliance.
Salary Comparison
Compensation reflects demand, expertise, and specialization:
- IoT Professionals: Average salaries for IoT developers and security specialists range from $85,000 to $130,000 annually in the U.S., with senior roles exceeding $150,000.
- Cybersecurity Professionals: Roles such as cybersecurity analysts or penetration testers typically earn $90,000 to $140,000, with CISSP-certified specialists or consultants earning over $160,000.
Educational Requirements and Certifications
Education paths overlap but diverge in focus:
- IoT Path: Often requires knowledge of embedded systems, sensor networks, programming, and security protocols. Recommended certifications include Certified IoT Security Practitioner (CIoTSP) and CompTIA IoT+.
- Cybersecurity Path: Emphasizes network security, threat detection, and risk management. Certifications such as CISSP, CEH, and CISM are widely recognized.
- Many universities now offer IoT cybersecurity courses that combine both disciplines, preparing students for hybrid roles in emerging industries.
Which Path Is Easier?
Professionals often ask: IoT or cyber security, which is easy? The answer depends on one’s background and interests:
- IoT: Suited for individuals interested in device engineering, programming, and system integration. Requires comfort with hardware and software interplay.
- Cybersecurity: Suited for those who enjoy network analysis, digital forensics, and threat mitigation. Often requires continuous learning to stay ahead of evolving threats.
While neither path is inherently easy, combining knowledge from both fields, especially in IoT security, can create high-value, niche expertise.
READ ALSO: NIST Cybersecurity Framework Vs 800-53: A Comprehensive Comparison
How to Get Started in IoT and Cybersecurity
Embarking on a career in IoT or cybersecurity requires a combination of education, practical experience, and continuous skill development. Professionals who strategically plan their learning paths can enter this high-demand field with confidence and position themselves for long-term growth.
Recommended Certifications and Courses
Certifications are essential for validating expertise and demonstrating credibility to employers. Key options include:
- Certified IoT Security Practitioner (CIoTSP): Focuses on securing IoT devices and networks, covering authentication, encryption, and incident response.
- CompTIA IoT+: Provides foundational knowledge on IoT design, deployment, and maintenance.
- CISSP and CEH Certifications: Although primarily cybersecurity-focused, these credentials are valuable for IoT security roles, especially when dealing with network protection and threat mitigation.
- IoT Cybersecurity Courses: Many universities and online platforms offer specialized programs that combine IoT device management with cybersecurity principles, preparing students for hybrid roles.
These credentials help aspiring professionals build both technical knowledge and industry-recognized qualifications, giving them a competitive advantage.
Hands-On Projects and Research
Practical experience is crucial in IoT cybersecurity. Engaging in IoT cybersecurity projects allows learners to apply theoretical knowledge to real-world scenarios:
- Simulated IoT Networks: Create test networks with smart devices to identify vulnerabilities and implement security measures.
- Open-Source Projects: Contribute to projects on GitHub that focus on IoT device security or cybersecurity tooling.
- Research Papers and Case Studies: Reviewing IoT in cyber security research papers helps professionals understand emerging threats, mitigation strategies, and industry trends.
Hands-on projects reinforce skills and provide tangible proof of expertise for resumes and job applications.
Continuous Learning and Industry Trends
The fields of IoT and cybersecurity evolve rapidly, making ongoing education essential:
- Workshops and Webinars: Industry conferences and webinars provide insights into the latest technologies and threat landscapes.
- Professional Communities: Joining forums, LinkedIn groups, or cybersecurity communities allows networking with peers and staying updated on emerging trends.
- Advanced Technologies: Familiarity with AI, blockchain, and edge computing enhances your ability to secure complex IoT systems and positions you as a forward-thinking professional.
By combining formal education, hands-on projects, and continuous learning, aspiring professionals can build a strong foundation for a rewarding career in IoT and cybersecurity.
SEE: Will Cybersecurity Be Automated By 2026?
The Future of IoT and Cybersecurity
The future of IoT and cybersecurity is being shaped by rapid technological innovation, evolving threats, and increasingly stringent regulatory standards. As connected devices proliferate, organizations must adopt advanced strategies to secure networks, protect data, and ensure operational resilience.
Emerging Technologies and Trends
Several technologies are transforming the way IoT systems are secured:
- Artificial Intelligence (AI) and Machine Learning (ML): AI and ML analyze massive volumes of IoT data in real time, identifying anomalies and potential threats faster than traditional monitoring systems. These tools enable predictive security measures, reducing the risk of breaches.
- Blockchain Integration: IoT and Cyber Security, including Blockchain Technology, ensures transparent and tamper-proof data exchange across devices, providing decentralized security solutions that are harder to compromise.
- Edge Computing: Processing data closer to the source reduces latency and limits exposure to network attacks, enhancing IoT security and performance.
- Zero Trust Security Models: Treating every device and user as untrusted by default, zero trust approaches require continuous verification, minimizing the risk of lateral movement during attacks.
- Automated Incident Response: Automation enables rapid containment of compromised devices, limiting damage and maintaining system integrity.
Legislation and Global Standards
Regulations play a critical role in shaping IoT cybersecurity practices:
- Current Frameworks: Laws such as GDPR and CCPA impose strict requirements on data protection and privacy, impacting IoT device management globally.
- Future Regulations: As IoT adoption expands, governments are expected to introduce minimum security standards for connected devices, promoting safer deployment and interoperability.
- Global Cooperation: Cybersecurity threats transcend borders, making international collaboration vital. Shared threat intelligence and global standards help organizations anticipate attacks and implement best practices consistently.
The Role of Research and Continuous Learning
The rapidly evolving IoT landscape emphasizes the importance of ongoing research:
- Engaging in IoT in cyber security research papers allows professionals to track emerging threats, innovative security solutions, and industry benchmarks.
- Participating in IoT cybersecurity projects fosters practical expertise, ensuring that theoretical knowledge translates into effective real-world security strategies.
- Continuous learning, through courses, certifications, and professional communities, prepares professionals to adapt to new technologies such as AI-driven threat detection, blockchain-based security protocols, and edge computing applications.
By embracing these technologies, adhering to evolving regulations, and investing in education and research, organizations and professionals can secure IoT ecosystems and capitalize on their potential safely and efficiently.
Conclusion
The intersection of IoT and cybersecurity presents both immense opportunities and complex challenges. As connected devices continue to shape industries from healthcare to manufacturing and smart cities, understanding iot vs cybersecurity is essential for professionals and organizations alike. Careers in both fields offer competitive salaries, high demand, and opportunities to work on cutting-edge technologies, including AI, blockchain, and edge computing.
Investing in the right education, certifications, and hands-on IoT cybersecurity projects is critical for building expertise. Whether pursuing IoT cybersecurity courses, gaining industry-recognized credentials, or contributing to research, professionals who combine practical experience with continuous learning are best positioned to succeed.
Start exploring your path today: enroll in a specialized IoT or cybersecurity course, participate in real-world projects, and join professional communities to stay ahead of emerging trends. By equipping yourself with knowledge, skills, and certifications, you can secure connected systems, protect critical data, and thrive in this high-growth industry.
FAQ
Is IoT used in cybersecurity?
Yes. IoT is integral to modern cybersecurity because connected devices can be both targets and tools in network security. IoT devices generate vast amounts of data that cybersecurity systems monitor to detect anomalies, unauthorized access, or potential threats.
Implementing IoT cybersecurity measures ensures that smart devices, industrial sensors, and networked systems are protected from breaches and attacks, making IoT both a risk area and a critical component of security strategies.
What are the 4 types of IoT?
IoT can be categorized into four main types based on application and environment:
Consumer IoT: Smart home devices, wearables, and personal gadgets.
Industrial IoT (IIoT): Machinery, factory automation, and logistics sensors.
Commercial IoT: Retail, healthcare monitoring devices, and smart buildings.
Infrastructure IoT: Smart city systems, energy grids, traffic monitoring, and environmental sensors.
Can IoT sensors work without Internet?
Yes, IoT sensors can operate in offline or edge-computing modes, collecting data locally and storing it until a network connection becomes available. Some sensors can perform limited functions autonomously, such as monitoring temperature or triggering alarms, even without continuous Internet access. However, full functionality, like real-time data sharing or cloud analytics, requires connectivity.
How does IoT make money?
IoT generates revenue through multiple streams:
Product Sales: Selling connected devices and smart solutions.
Subscription Services: Offering cloud platforms, remote monitoring, and analytics dashboards.
Data Monetization: Aggregating anonymized data for insights, marketing, or operational optimization.
Operational Efficiency: Businesses save costs via predictive maintenance, resource optimization, and automated processes, which indirectly increases profitability.
