
Application Security vs Cybersecurity: A 2025 Complete Guide
Application Security vs Cybersecurity: A 2025 Complete Guide
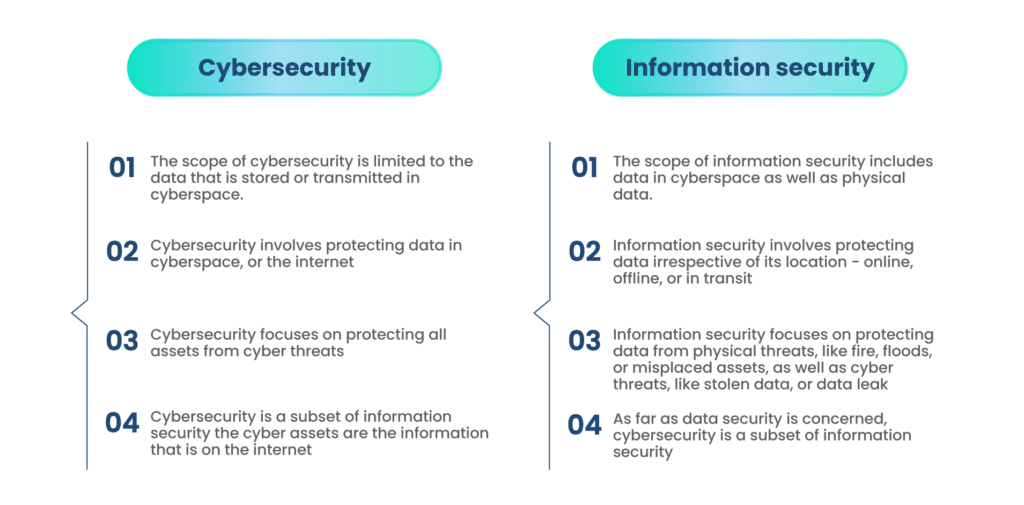
Application security vs cybersecurity should be complementary, not interchangeable. AppSec secures the product, code, pipelines, and runtime services, so vulnerabilities don’t ship.
Cybersecurity secures the enterprise, identity, endpoints, networks, data, and cloud estates, so attacks can’t take root or spread. Mature organizations treat them as two halves of one risk program with clear ownership, shared telemetry, and well-rehearsed hand-offs.
Application Security vs Cybersecurity: Comparison Table
| Dimension | Application Security (AppSec) | Cybersecurity |
| Primary Outcome | Fewer exploitable flaws reach production; safer releases | Fewer successful intrusions; faster detection and recovery |
| Scope | Code, dependencies, CI/CD, APIs, containers/serverless, app runtime | Identity, email, endpoints, networks, SaaS/IaaS, data protection, SOC |
| Operates When | Design → build → test → deploy → runtime (“secure SDLC”) | Prevent → detect → respond → recover (SOC/IR lifecycle) |
| Typical Owners | Product Security, Platform/DevOps, Engineering leads | Security Operations, IT/Infra, GRC, Incident Response |
| Core Signals | Time-to-fix by severity, SBOM/SCA coverage, pre-prod gates | MTTD/MTTR, EDR/IdP coverage, phishing rates, data exfil alerts |

Start a Life-Changing Career in Cybersecurity Today
Where teams go wrong: overspending on scanners without fixing developer workflows; relying on perimeter tools while identity and email remain porous; and failing to connect SOC alerts to product backlogs. The practical north star is risk reduction per dollar while preserving delivery velocity: threat modeling tied to automated CI gates on the AppSec side, and identity-first controls plus EDR/XDR and tested backup/DR on the Cyber side.
The rest of this guide formalizes definitions, threat models, control sets, cloud realities, governance, metrics, and a short decision plan so leaders can invest in the right next three moves.
Definitions & Scope
At first glance, application security and cybersecurity seem to overlap. Both aim to keep data safe, both guard against attackers, and both rely on layered defenses. The real difference lies in where they operate and what they protect.
Application Security (AppSec)
AppSec is about protecting the software itself. It secures applications at every stage, design, coding, testing, deployment, and ongoing maintenance. Its focus is narrow but deep: prevent flaws in code, block exploits against APIs, and ensure that applications don’t become an attacker’s entry point.
Tools here include secure coding practices, SAST/DAST scanners, software composition analysis (SCA), threat modeling, and runtime application protections like web application firewalls. Ownership typically sits with product security teams, developers, or DevOps engineers who integrate security directly into the development lifecycle.
Cybersecurity
Cybersecurity is the broader umbrella that covers an entire organization’s digital environment. It extends beyond applications to include identity, networks, endpoints, cloud platforms, and even physical systems tied into IT infrastructure. A cybersecurity program deals with phishing campaigns, ransomware, insider threats, and data breaches that may affect multiple layers of technology.
Its practitioners include SOC analysts, IT security engineers, risk managers, and compliance teams. Controls often involve identity and access management (IAM), endpoint detection and response (EDR), network segmentation, encryption, and incident response planning.
Side by Side
- AppSec focuses on products (code, APIs, pipelines).
- Cybersecurity focuses on the enterprise (people, processes, technology as a whole).
- AppSec is precise, code-centric, and embedded in the development lifecycle.
- Cybersecurity is systemic, risk-centric, and embedded in organizational resilience.
Understanding this distinction is crucial: investing only in AppSec may still leave your organization open to phishing or ransomware, while focusing only on cybersecurity may miss the flaws hidden inside applications that customers use every day. Both layers must align under a single governance framework to be effective.
Threat Models: What Each Discipline Actually Defends Against
Security means anticipating what could go wrong. Application security and cybersecurity each face their own category of threats, shaped by where they sit in the technology stack. Understanding these threat models helps organizations prioritize defenses effectively.
Application Security Threats
Application security threats are tightly linked to the code and logic of software. Attackers exploit flaws in design, development, or configuration to gain access or manipulate data. The most recognized examples come from the OWASP Top 10, which highlights recurring weaknesses across industries:
- SQL Injection & NoSQL Injection: Malicious queries that pull or alter sensitive data.
- Cross-Site Scripting (XSS): Injected scripts that hijack user sessions or steal data.
- Broken Authentication & Session Management: Exploits that let attackers impersonate users.
- Insecure APIs: Overly permissive or poorly validated endpoints leaking data.
- Software Supply Chain Risk: Vulnerabilities in third-party packages or open-source components that developers unknowingly import.
- CI/CD Pipeline Attacks: Compromise of build or deployment processes, where attackers insert malicious code before release.
These threats are often subtle and hidden until code reaches production, which makes early detection in the SDLC essential.
Cybersecurity Threats
Cybersecurity threats are broader, targeting applications and the entire enterprise ecosystem. They often exploit human behavior, weak identity systems, or underprotected infrastructure. Key examples include:
- Phishing & Social Engineering: Tricks to steal credentials or deliver malware through email and messaging platforms.
- Ransomware: Malicious software that encrypts organizational data until payment is made.
- Business Email Compromise (BEC): Fraudulent use of executive accounts to redirect payments or extract sensitive information.
- Distributed Denial of Service (DDoS): Overwhelming systems with traffic to disrupt services.
- Credential Theft & Identity Attacks: Stolen or brute-forced passwords used to gain unauthorized access.
- Insider Threats: Malicious or careless insiders who misuse privileges or expose sensitive data.
- Lateral Movement: Attackers spreading across networks to escalate privileges and access critical systems.
The Bridge Between the Two
Identity and access threats illustrate where AppSec and Cybersecurity converge. An insecure login mechanism in an app (AppSec flaw) can become the foothold for a broader ransomware campaign (Cybersecurity incident). Likewise, a compromised Active Directory account (Cyber threat) may be used to exploit application APIs (AppSec risk).
Organizations that silo these two areas often fail to recognize how attackers chain weaknesses together. A mature security program maps out these interdependencies and ensures product teams and SOC teams share a common threat picture.
RELATED: What Is Blockchain Security? A Comprehensive Breakdown
Controls & Tooling
The best way to understand the divide between application security and cybersecurity is to look at the controls and tools each uses day-to-day. Both aim to reduce risk, but they operate at different levels of the stack.
Application Security Controls
Application security tools live inside the software lifecycle. They are designed to catch weaknesses before attackers do.
- Secure Coding Standards: Guidelines for developers to avoid risky practices, such as hardcoding passwords or using outdated libraries.
- Static and Dynamic Testing (SAST/DAST): Automated scans that detect vulnerabilities in source code (SAST) or in running applications (DAST).
- Software Composition Analysis (SCA): Tools that scan open-source and third-party libraries for known flaws.
- Threat Modeling: Workshops where developers map out “what could go wrong” before code is written.
- Runtime Protections: Firewalls for apps (WAF/WAAP) and runtime shields (RASP) that block malicious traffic in production.
- SBOM (Software Bill of Materials): An inventory of all software components, used to track and patch vulnerabilities quickly.
These tools prioritize prevention and precision. The goal is to release code that is safe by default and can be trusted once in production.
Cybersecurity Controls
Cybersecurity tools operate at the infrastructure and enterprise level, protecting the organization as a whole.
- Identity and Access Management (IAM): Central systems that enforce multi-factor authentication (MFA), role-based access, and least-privilege permissions.
- Endpoint Detection and Response (EDR/XDR): Agents that watch laptops, servers, and cloud instances for suspicious behavior.
- Network Security: Firewalls, intrusion detection systems (IDS), intrusion prevention systems (IPS), and segmentation to contain breaches.
- Email Security: Filters and AI-based tools that block phishing campaigns before users click.
- Security Information and Event Management (SIEM/SOAR): Central dashboards that collect logs, detect anomalies, and automate incident response.
- Data Loss Prevention (DLP): Tools that stop sensitive data (like PII) from being leaked, whether through email, downloads, or cloud storage.
- Cloud Posture Management (CSPM/CNAPP): Services that identify risky cloud configurations and enforce security policies.
These controls emphasize detection and resilience. They assume some attacks will get through, so the focus is on spotting them quickly and containing damage.
The Contrast
- AppSec tools speak the language of developers—code, builds, APIs.
- Cybersecurity tools speak the language of operations—logs, alerts, users, networks.
- AppSec aims for secure by design.
- Cybersecurity aims for secure in operation.
When organizations buy tools without clarifying which domain they serve, they risk overlap, blind spots, or wasted spend. The smartest programs design a balanced toolkit where AppSec gates prevent bad code from shipping, and Cyber controls detect and respond if anything slips through.
READ ALSO: Will Cybersecurity Be Automated By 2026?
Lifecycle & Processes: How Work Flows Differ
Security is about tools, including when and how work happens. Application security and cybersecurity follow different lifecycles, shaped by their scope and responsibilities.
Application Security Lifecycle
AppSec aligns with the software development lifecycle (SDLC). Its mission is to prevent vulnerabilities from ever leaving the build pipeline.
- Design Reviews: Before coding starts, engineers and AppSec specialists run threat modeling sessions to identify risks.
- Code Reviews & Static Analysis: Developers apply secure coding guidelines, while automated tools scan for flaws early.
- Automated Security Gates: In CI/CD pipelines, scans like SAST, DAST, or SCA must pass before code is deployed.
- Pre-Production Testing: Penetration tests and bug bounty programs simulate attacks on staging environments.
- Runtime Monitoring: Web application firewalls (WAFs) and runtime security agents guard live applications.
- Continuous Feedback: Lessons from incidents are fed back into coding standards and developer training.
The philosophy here is shift left, push security controls as far upstream as possible so issues are cheaper and faster to fix.
Cybersecurity Lifecycle
Cybersecurity follows a broader defense and response cycle that runs 24/7, across people, processes, and technology.
- Prevention: Hardening systems, enforcing MFA, segmenting networks, and applying patches.
- Detection: Security Operations Centers (SOCs) continuously monitor logs, alerts, and behavioral signals.
- Response: When an incident is detected, analysts investigate, contain, and remediate threats following runbooks.
- Recovery: Systems are restored from backups, lessons are documented, and response processes are refined.
- Preparedness: Tabletop exercises, red-team drills, and regular audits ensure teams are ready for the next attack.
The philosophy here is assume breach, no matter how strong your defenses, prepare to detect and respond as if attackers are already inside.
The Cultural Divide
- AppSec is often embedded with developers, using agile sprints and automation.
- Cybersecurity is often centralized in SOC or IT teams, using 24/7 monitoring and incident response playbooks.
- AppSec speaks in terms of vulnerabilities and defect rates.
- Cybersecurity speaks in terms of incidents and response times.
Bridging these lifecycles is one of the toughest challenges organizations face. For example, if a SOC detects malicious API traffic, who owns the fix: the operations team or the developers who wrote the API? Without clear hand-offs, problems fall between the cracks.
The trend in 2025 is to “shift everywhere,” not just left. That means embedding security across the entire lifecycle, design, code, operations, and response, so application security and cybersecurity reinforce each other instead of operating in silos.
Overlap & Hand-Offs (Where Teams Usually Drop the Ball)
The line between application security and cybersecurity isn’t a wall; it’s a seam. And like any seam, if it’s not stitched tightly, things slip through. Many breaches happen not because one team failed outright, but because no one owned the space in between.
Shared Primitives
Certain controls cut across both domains:
- Identity & Access: Applications need secure login flows, while enterprise IAM systems enforce multi-factor authentication (MFA) and least privilege.
- Secrets Management: Developers must keep API keys out of code, while cybersecurity teams ensure those secrets aren’t exposed in logs or cloud services.
- Telemetry & Logging: AppSec generates logs on vulnerabilities and runtime behavior, while cybersecurity aggregates those logs in SIEM/SOAR for threat detection.
Without shared standards, logs go unread, credentials leak, and alerts drown in noise.
Where the Ball Drops
- API Abuse: A web app team spots abnormal API calls but doesn’t escalate to the SOC. Weeks later, attackers use those same endpoints for data exfiltration.
- Vulnerability Management: The SOC flags a critical CVE from external threat intel, but engineering doesn’t prioritize patching because it’s not tied into their backlog system.
- Incident Response: During a breach, the SOC isolates compromised endpoints but lacks visibility into application-layer exploits, leaving gaps in remediation.
The Ownership Question
A recurring tension is: who fixes what? For example, if an attacker exploits an application misconfiguration spotted during runtime monitoring, should the SOC handle containment or should developers deploy the code fix? Too often, this leads to delays and finger-pointing.
The Integration Trend
Leading organizations are solving this by:
- Embedding security champions in engineering teams.
- Creating joint runbooks that specify exactly when SOC incidents trigger development action.
- Using unified dashboards that merge AppSec findings (like vulnerable libraries) with cybersecurity telemetry (like abnormal network flows).
The message is simple: attackers don’t care about your org chart. They exploit overlaps. Organizations that align AppSec and cybersecurity as one continuum, rather than two silos, close those gaps before adversaries can find them.
SEE MORE: Comptia Security+ vs Google Cybersecurity Certification: 2025 Comparison
Cloud Reality Check (SaaS, PaaS, IaaS)
The cloud has erased the neat boundaries between application security and cybersecurity. What used to live in on-premises servers is now spread across SaaS apps, cloud platforms (PaaS), and infrastructure services (IaaS). This shift has created both opportunities and new blind spots.
Application Security in the Cloud
Modern applications are often cloud-native, built from microservices, APIs, containers, and serverless functions. This expands the AppSec threat surface:
- API Exploits: Poorly secured endpoints become easy targets for attackers.
- Container Vulnerabilities: Outdated base images or insecure configurations create pathways for compromise.
- Infrastructure as Code (IaC) Risks: Misconfigured templates can provision insecure resources by default.
- Supply Chain Exposure: Open-source packages and third-party services introduce vulnerabilities that move faster in a cloud pipeline.
AppSec in the cloud focuses on embedding security into DevOps (DevSecOps): automated scans in CI/CD pipelines, IaC security tools, runtime protection for containers, and strong API governance.
Cybersecurity in the Cloud
From a cybersecurity perspective, the cloud extends the perimeter—and often dissolves it entirely. Key risks include:
- Misconfigured Storage: Exposed S3 buckets or blob storage leaking sensitive data.
- Overprivileged Identities: Weak IAM policies that grant far more access than necessary.
- Shadow IT: Unapproved SaaS applications handling sensitive company data.
- Multi-Tenant Risks: Shared infrastructure in cloud environments can be abused if isolation fails.
Cybersecurity teams rely on Cloud Security Posture Management (CSPM), Cloud Native Application Protection Platforms (CNAPP), and identity-first strategies (MFA, Just-In-Time access, conditional policies) to lock down sprawling cloud estates.
Shared Responsibility Model
A critical point organizations often miss: cloud providers don’t secure everything.
- Providers secure the infrastructure (datacenters, networks, hardware).
- Customers secure the workloads (apps, data, configurations, user access).
If your app exposes an API without authentication or if your team leaves a database open to the internet, that’s not on AWS, Azure, or Google Cloud; it’s on you.
Reality Check for 2025
The fastest-growing breaches today stem from misconfigurations and unsecured APIs in cloud environments. These are not failures of technology, but of coordination. Application teams must write secure code and provision safe infrastructure, while cybersecurity teams must monitor, enforce, and respond. Without that alignment, the promise of cloud scalability turns into a liability.
Compliance & Governance

Security doesn’t exist in a vacuum; it must be demonstrated, documented, and aligned with external expectations. This is where compliance and governance enter the picture. Both application security and cybersecurity play roles here, but they speak slightly different dialects of the same language.
Application Security and Compliance
Application security efforts often provide the evidence auditors are looking for around software assurance. For example:
- Secure SDLC Documentation: Proof that code is reviewed, scanned, and tested before release.
- Vulnerability Management: Metrics showing critical issues are remediated within defined SLAs.
- SBOMs (Software Bill of Materials): Inventories of open-source and third-party dependencies, now required under U.S. Executive Order 14028 and increasingly by regulators worldwide.
- Testing Artifacts: SAST/DAST scan results, penetration test reports, and secure design reviews.
Frameworks like OWASP SAMM, PCI DSS, and ISO/IEC 27034 expect evidence that AppSec is built into development pipelines, not bolted on afterward.
Cybersecurity and Governance
Cybersecurity provides the policies, controls, and oversight that bind an organization’s defenses together. This includes:
- Risk Registers: Formal documentation of risks, ownership, and mitigation strategies.
- Security Policies & Standards: Company-wide rules on access control, encryption, logging, and data handling.
- Vendor Risk Management: Assessing third-party suppliers and SaaS providers for their security posture.
- Incident Response Plans: Playbooks and exercises to prove readiness.
- Compliance Frameworks: Mapping controls to NIST CSF 2.0, ISO/IEC 27001, SOC 2, HIPAA, GDPR, and others.
Here, governance means accountability. Boards, regulators, and customers all want assurance that security risks are identified, measured, and addressed systematically.
Why Language Matters
Confusion often arises when AppSec findings and cybersecurity policies don’t align. A developer may log an “XSS vulnerability,” while a risk officer only recognizes categories like “data breach risk.” Bridging this gap requires a common risk language. Many organizations now use frameworks like MITRE ATT&CK to map technical vulnerabilities (AppSec domain) to higher-level threats and business impacts (Cyber domain).
Governance ties together the tactical work of AppSec and the strategic oversight of Cybersecurity. Without it, AppSec looks like endless tickets in Jira, and Cybersecurity looks like endless alerts in a SIEM. With governance, both contribute to a clear story: we know our risks, we’re reducing them, and here’s the proof.
READ: Risk Analysis in Cyber Security: 2025 Complete Analysis
Metrics That Matter (Executive & Engineering Views)
Security programs rise or fall on their ability to show impact. Leaders need metrics that justify investment, while engineers need signals that guide day-to-day improvements. Application security and cybersecurity measure success differently, but both must connect to the same business outcomes: reduced risk and sustained productivity.
Application Security Metrics
AppSec metrics focus on the health of the software pipeline. They help product teams see if vulnerabilities are shrinking and if fixes are accelerating. Common measures include:
- Time-to-Fix by Severity: How quickly critical and high-severity vulnerabilities are remediated once identified.
- Vulnerability Recurrence Rate: Whether the same types of flaws (e.g., XSS, SQLi) keep resurfacing in releases.
- Coverage of Security Testing: Percentage of code scanned by SAST/DAST tools, penetration tests, or dependency checks.
- SBOM Completeness: How thorough the organization is at cataloging and tracking its third-party and open-source components.
- Blocked Deployments: Number of builds stopped by security gates in CI/CD pipelines.
These metrics resonate with engineering leaders because they tie directly to developer velocity, secure code shipped faster, with fewer late-breaking surprises.
Cybersecurity Metrics
Cybersecurity metrics track the defensibility of the enterprise. They are broader and often operational, aligning with SOC, IT, and governance functions. Key measures include:
- Mean Time to Detect (MTTD): Average time it takes to identify a potential incident.
- Mean Time to Respond (MTTR): How quickly incidents are contained and resolved once detected.
- Incident Count by Class: Breakdown of phishing, ransomware, insider threat, and other categories.
- Identity Hygiene: Percentage of accounts with MFA, number of dormant or overprivileged accounts, frequency of password resets.
- Endpoint & Cloud Coverage: Percentage of devices and cloud workloads protected by EDR/XDR or CSPM tools.
- Phishing Resilience: Failure rates in simulated phishing campaigns across staff.
Executives care about these metrics because they show whether the organization can withstand attacks and bounce back quickly.
The Alignment Challenge
Problems arise when these two sets of metrics live in silos. A CISO may report improved MTTR, while engineering still struggles with critical bugs shipping to production. The fix is a shared scorecard that links software-level security (AppSec) with enterprise-level defense (Cybersecurity). For example:
- A reduced time-to-fix in AppSec correlates with fewer production incidents reported to the SOC.
- Improved MFA adoption correlates with fewer compromised application sessions.
North-Star View
The ultimate measure is risk reduction per dollar spent without slowing down the business. If AppSec metrics show fewer exploitable flaws, and Cybersecurity metrics show faster recovery, together they prove security is enabling, not obstructing, innovation.
SEE: What Coding Language Should I Learn for Cyber Security?
Cost & Staffing: Where to Invest First
Security budgets are finite, and teams are always understaffed. The challenge for leaders is not whether to fund security, it’s where the first dollar should go. Application security and cybersecurity each require investment, but the sequence often depends on organizational size, maturity, and risk profile.
For Small Organizations
Startups and small businesses rarely have the luxury of large security teams. Here, the priority is to cover the highest-exposure areas with minimal overhead.
- AppSec Focus: Automate scans in the CI/CD pipeline with open-source or affordable tools (SAST/SCA). This ensures obvious vulnerabilities don’t ship.
- Cyber Focus: Identity-first defenses (MFA, single sign-on) and endpoint protection for laptops and servers. These prevent the most common entry points, weak credentials, and malware.
- Staffing: A single security engineer or a DevOps lead with security responsibilities can handle this stage. Outsourcing SOC monitoring to a managed service may be cost-effective.
For Mid-Market Companies
Mid-sized organizations face pressure from regulators, customers, and investors to formalize their security. At this stage, the priority shifts to scaling visibility and governance.
- AppSec Focus: Dedicated product security engineers to embed secure coding practices, establish SBOM processes, and enforce security gates in CI/CD.
- Cyber Focus: Stand up a SOC (in-house or hybrid) to monitor threats, integrate SIEM/SOAR platforms, and establish an incident response plan.
- Staffing: A small AppSec team (1–3 engineers) paired with a SOC team (analysts, incident responders) reporting into the CISO. Compliance specialists may also be needed to manage audits.
For Large Enterprises
Enterprises operate at a different scale, where threats are more complex and the attack surface is enormous. Here, the challenge is coordination across silos.
- AppSec Focus: Specialized teams for threat modeling, penetration testing, and supply-chain security. Continuous bug bounty programs and red teams become standard.
- Cyber Focus: Full SOC with tiered analysts, threat hunters, digital forensics teams, and cloud security architects. Enterprise-wide risk management functions link technical findings to board-level reporting.
- Staffing: Separate but connected teams—Product Security under Engineering, Cybersecurity Operations under IT or Security. Governance and GRC functions unify them through shared reporting structures.
Build vs. Buy Decisions
- Buy when speed matters: managed SOC services, cloud security platforms, or vulnerability scanners.
- Build when customization matters: secure SDLC processes, threat modeling, and integrations that match internal workflows.
Bottom Line
No organization can fund everything at once. The smartest path is staged:
- Cover the basics: identity, endpoints, automated code scans.
- Add visibility: SOC, SIEM, AppSec dashboards.
- Scale and specialize: dedicated product security and threat-hunting teams.
The sequencing may differ, but the principle is the same: fund controls that reduce the most risk for your size, then grow into more advanced practices as complexity demands it.
Case Miniatures (Concrete, Non-Hyped Examples)
Abstract talk about controls is useful, but real-world stories illustrate how application security and cybersecurity play out differently—and how they often reinforce one another. Here are two concise examples from each side.
Application Security in Action
- SBOM + SCA to Stop a Vulnerable Library Rollout
A fintech startup relied heavily on open-source libraries. During a routine software composition analysis (SCA) scan, the build pipeline flagged a critical vulnerability in a widely used JSON parser. Because the team maintained a living Software Bill of Materials (SBOM), they immediately identified every service using that library. Instead of shipping insecure code, engineers patched the dependency across services and redeployed within 24 hours. Result: no customer exposure, no scramble after release, and a confidence boost in their secure development process.
- MFA in Mobile Healthcare App
A healthcare provider built a mobile app for patients to access records and book appointments. Initially, login was password-only. AppSec specialists raised concerns about stolen credentials, so the provider added multi-factor authentication (MFA) using biometric checks. Weeks later, attackers tried credential stuffing with leaked email/password combos—but failed. MFA blocked unauthorized access, protecting sensitive health data and reducing legal liability.
Cybersecurity in Action
- Identity-First Strategy Foils Ransomware
A mid-sized manufacturer faced phishing attempts targeting finance staff. Instead of relying solely on email filters, the cybersecurity team rolled out phishing-resistant MFA and restricted admin privileges. When attackers eventually tricked one employee into clicking a malicious attachment, the malware was contained, no lateral movement, no encryption of shared drives. The incident was closed in hours instead of weeks.
- EDR Detects Abnormal Endpoint Activity
An e-commerce company invested in endpoint detection and response (EDR) after seeing peers hit by ransomware. The system flagged unusual behavior on a developer laptop: rapid encryption of local files. The SOC isolated the endpoint remotely, preventing the ransomware from spreading into production servers. Post-incident review showed that the attack was stopped before customer data was touched.
Each case shows a single discipline doing its job, but also highlights how both domains are stronger together. SBOM discipline is useless if attackers gain privileged access through weak credentials. MFA loses value if a vulnerable app leaks tokens. The real win is in integration: application security reduces the flaws attackers can target, while cybersecurity limits the blast radius if anything slips through.
Decision Guide: Picking the Next Three Moves
Every org can progress with three concrete steps, chosen by current risk and maturity. Use the lane that matches you best.
If you’re product-led (shipping fast, cloud-native):
- Institutionalize threat modeling on epics and major features; record risks and mitigations in the backlog.
- Automate CI/CD gates (SAST, SCA, secrets scanning, IaC checks) with severity thresholds that block deploys.
- Stand up SBOM + dependency hygiene (ownership, patch SLAs, emergency update playbook).
If you’re breach-worried (recent incidents or audit pressure):
- Identity hardening: phishing-resistant MFA, SSO, least privilege, dormant account cleanup.
- EDR/XDR everywhere with 100% endpoint coverage and weekly gap reports.
- Backup/DR proof: immutable backups, recovery runbooks, quarterly restore tests.
If you’re cloud-heavy (multi-account, multi-cloud):
- CSPM/CNAPP baseline: fix public storage, overbroad IAM, exposed management ports.
- API posture: inventory, auth/authorization standards, abuse rate-limits, WAF/WAAP in front.
- IaC guardrails: enforce approved modules; block risky configs at PR time.
If you’re scaling the program (mid-market to enterprise):
- Joint runbooks linking SOC detections to engineering fixes (who triages, who patches, SLA tiers).
- Unified telemetry: route AppSec findings and SOC alerts into one dashboard with shared severities.
- Metrics cadence: monthly exec scorecard (MTTD/MTTR, time-to-fix, MFA coverage, SBOM completeness).
One-page checklist (print and pin):
- Owners named for AppSec and Cyber, with a shared escalation path.
- Blocking gates in CI/CD and 24/7 detection in SOC (no gaps).
- Identity, endpoints, cloud, and APIs each have a minimum control set.
- Evidence ready for auditors: secure SDLC, incident logs, recovery tests.
When trade-offs arise, prioritize controls that shrink blast radius and stop known classes of failure, identity, code gates, and recovery. Everything else is sequencing.
Conclusion
Application security and cybersecurity may look like overlapping fields, but in practice, they solve different problems at different layers of an organization’s digital ecosystem. AppSec ensures that the software shipped to customers is resilient against vulnerabilities, while cybersecurity protects the broader environment, people, networks, identities, and data from compromise.
The two are not rivals but partners. When treated as silos, they leave gaps attackers can exploit. When integrated, through shared threat models, unified telemetry, and joint playbooks, they reinforce one another, shrinking risk and improving resilience without slowing the business down.
The landscape ahead is clear: AI-driven code, identity-first defenses, software supply chain assurance, and zero trust architectures will reshape how both AppSec and Cybersecurity are practiced. Organizations that adopt a balanced, integrated approach now will be better prepared for the next generation of threats, regulatory pressures, and customer expectations.
Secure the product, secure the enterprise, and stitch the seam between them. That is the path to sustainable digital trust in 2025 and beyond.
FAQ
Is application security a part of cyber security?
Yes. Application security is considered a subset of cybersecurity, but with a specialized focus. Cybersecurity is the umbrella discipline concerned with protecting an organization’s entire digital estate, networks, endpoints, data, identity, and cloud systems. Application security narrows that scope to the software layer: securing code, APIs, pipelines, and applications against exploits such as injection attacks, authentication flaws, and supply chain risks.
While cybersecurity teams handle broad defenses like firewalls, EDR, and incident response, application security integrates into the software development lifecycle. The two are interconnected: if applications are insecure, they become easy entry points for attackers, undermining enterprise-wide cybersecurity. In practice, strong security requires treating AppSec as a dedicated component of cybersecurity strategy.
Is AppSec a good career?
Yes. Application security (AppSec) is an increasingly attractive career path due to the rapid growth of software-driven businesses and cloud-native development. Organizations across finance, healthcare, e-commerce, and government face pressure to release secure software, making AppSec engineers and analysts highly sought after.
According to salary benchmarks, U.S. AppSec engineers often earn between $95,000 and $150,000 annually, with senior roles exceeding $175,000. Beyond compensation, the role offers career diversity: specialists may move into product security leadership, DevSecOps, penetration testing, or even CISO positions.
The demand is long-term; every new application, API, or AI-driven service introduces potential risks that require skilled professionals to manage. For individuals with a mix of coding knowledge and security mindset, AppSec is both a stable and rewarding career choice.
Is AI replacing cyber security jobs?
Not entirely. Artificial intelligence is reshaping, not replacing, cybersecurity roles. AI-driven tools already detect anomalies in network traffic, identify vulnerabilities in code, and automate routine monitoring tasks faster than humans could. However, these tools still need human oversight for context, judgment, and decision-making. For example, AI can flag suspicious activity, but analysts must investigate, confirm, and respond.
What’s changing is the nature of cybersecurity jobs: less time spent on repetitive tasks, more focus on strategy, risk assessment, and incident response. The workforce will need to adapt, with hybrid skills in AI tool management and security operations. Rather than eliminating jobs, AI is expected to create new categories of roles around threat modeling for AI systems, algorithm auditing, and securing AI-driven applications.
Will cybersecurity be in demand in 2030?
Yes, if anything, demand will intensify. Industry reports project that global cybersecurity job vacancies could surpass 3.5 million unfilled positions by 2030, continuing a trend of chronic talent shortages. Several factors drive this growth:
– Increased digitization across industries, from healthcare to finance.
– Expansion of cloud infrastructure and IoT ecosystems.
– Rising sophistication of cyber threats, including AI-powered attacks.
– Stricter regulations requiring companies to prove security compliance.
By 2030, cybersecurity will likely evolve toward identity-first, AI-assisted, and compliance-driven models, but human expertise will remain essential. Roles such as cloud security architects, AppSec engineers, and governance/risk analysts will be especially in demand. For individuals entering the field today, cybersecurity offers job security, upward mobility, and global relevance well into the next decade.
