
Privileged User Cybersecurity Responsibilities
Privileged User Cybersecurity Responsibilities
In cybersecurity, few roles carry as much weight, or as much risk, as privileged users. These individuals, often system administrators, database managers, or IT specialists, hold elevated access rights that allow them to configure networks, manage critical data, and oversee security controls. In other words, they are the gatekeepers of an organization’s digital infrastructure.
With that power comes enormous responsibility. Misuse of privileged access, whether accidental or intentional, can compromise sensitive data, disrupt operations, and even lead to devastating breaches. From the 2013 Edward Snowden disclosures to more recent insider-led cyber incidents, history has shown that organizations cannot afford to treat privileged access lightly.
This article explains what it means to be a privileged user in today’s threats, why their cybersecurity responsibilities are so critical, and how organizations can balance empowerment with control. By the end, you’ll understand not only the scope of privileged access but also the strategies and safeguards that keep it from becoming a liability.

Start a Life-Changing Career in Cybersecurity Today
Privileged User Cybersecurity Responsibilities and Their Access
At its core, the term privileged user refers to anyone granted administrative or elevated access within an organization’s IT environment. Unlike standard employees who interact with systems at a surface level, privileged users have the ability to make foundational changes that affect how those systems operate. Their responsibilities extend beyond routine use; they oversee, maintain, and in some cases, directly shape the security posture of the organization.
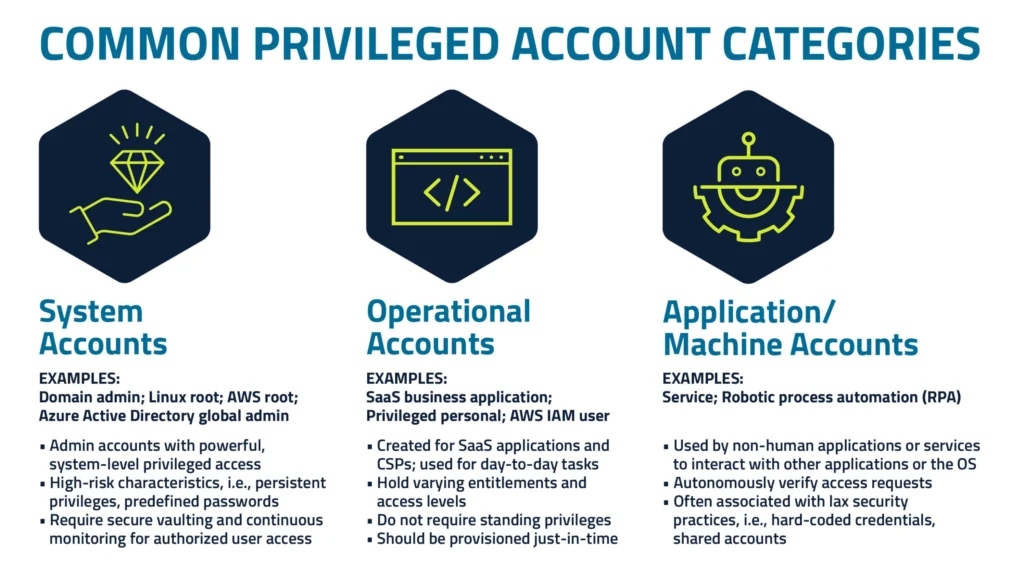
Types of Privileged Accounts
- Administrator Accounts – These accounts hold the broadest powers, including the ability to install software, modify system settings, and manage user permissions. Because of their elevated control, administrator accounts are a primary target for cyber attackers.
- Service Accounts – Often overlooked, these accounts are used by applications to communicate across systems. If not properly secured, they can provide a hidden entry point for attackers who exploit weak or unchanged credentials.
- Emergency Accounts – Sometimes called break glass accounts, these are reserved for critical incidents when rapid intervention is needed to restore systems. Their importance makes them equally critical to secure and monitor.
Scope of Privileged Access
The breadth of these roles gives privileged users a level of control unmatched by most employees. They can bypass typical restrictions, access sensitive data repositories, and alter security configurations. This capacity is both their strength and their greatest risk. A single misstep, intentional or accidental, can ripple across the organization, disrupting operations or exposing sensitive information.
In essence, privileged users are both gatekeepers and potential weak points. Understanding who they are, what they can access, and the weight of their responsibilities is the first step in building a resilient cybersecurity framework.
The Significance of Privileged User Responsibilities
The responsibilities tied to privileged accounts go beyond technical administration. They directly influence the confidentiality, integrity, and availability of organizational systems and data, three pillars of cybersecurity. When fulfilled properly, these responsibilities safeguard critical assets. When neglected, they open the door to significant financial, legal, and reputational harm.
Protecting Sensitive Information
Privileged users often have direct access to the most sensitive data within an organization: financial records, intellectual property, employee files, and customer information. Their duty is to ensure this information remains shielded from unauthorized access or exposure. A single data leak, whether intentional or accidental, can result in costly breaches and long-term damage to trust.
Ensuring System Integrity and Availability
Beyond protecting data, privileged users are central to the smooth functioning of critical infrastructure. From installing security patches to deploying new applications, their actions influence system performance and resilience. A misconfigured server or poorly managed update can disrupt entire networks, demonstrating why precision and adherence to best practices are non-negotiable.
Meeting Compliance and Legal Standards
Many industries, from healthcare to finance, operate under strict regulatory frameworks such as GDPR, HIPAA, or PCI-DSS. Privileged users play a frontline role in compliance, ensuring that sensitive data is processed, stored, and accessed in accordance with legal requirements. Failure to uphold these responsibilities can trigger not only regulatory fines but also lasting reputational damage.
Privileged users carry a dual burden: protecting sensitive information while enabling business continuity. Their ability to balance these demands makes them essential players in modern cybersecurity governance.
RELATED: Risk Analysis in Cyber Security: 2025 Complete Analysis
Common Risks and Threats for Privileged Accounts
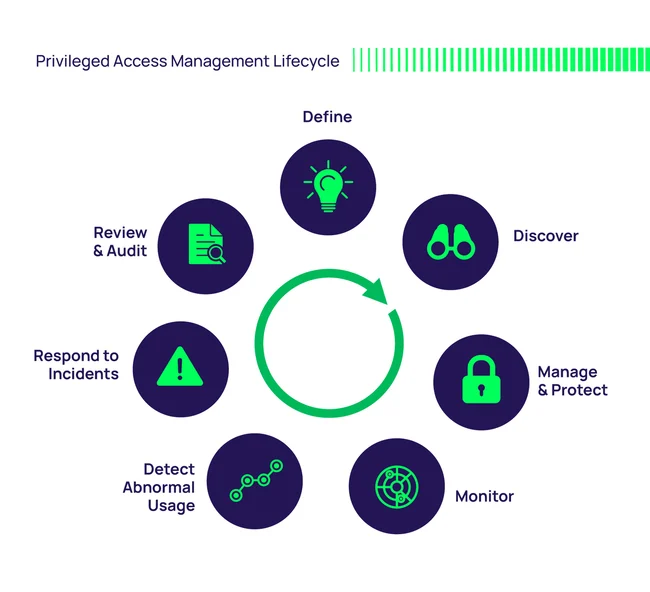
Because privileged accounts provide elevated access to critical systems, they are among the most attractive targets for cybercriminals and among the most vulnerable points within an organization. The risks are not limited to external hackers; insider threats and accidental misuse also play a significant role.
Internal Threats
Insider threats arise when employees with privileged access intentionally abuse their rights or inadvertently cause harm. A disgruntled administrator might delete essential data, while a careless staff member might bypass security policies without realizing the consequences. The potential for damage is amplified by the depth of control these users possess.
External Attacks
Cybercriminals frequently target privileged credentials as a direct path into secure networks. Through phishing campaigns, credential stuffing, or brute force attacks, hackers can impersonate administrators, move laterally across systems, and exfiltrate sensitive data, all without raising immediate suspicion. Breaches like these often go undetected until the damage is severe.
Accidental Misuse
Not all risks stem from malicious intent. Simple mistakes, such as misconfiguring security settings, sharing credentials, or failing to apply patches correctly, can expose systems to exploitation. In many cases, these errors are the result of inadequate training or insufficient oversight.
The combination of internal misuse, external compromise, and accidental errors makes privileged accounts a high-risk category. Organizations that fail to implement strict controls and monitoring mechanisms leave themselves exposed to threats that can escalate quickly and cause widespread disruption.
Best Practices for Managing Privileged User Access
Managing privileged accounts requires more than assigning roles and permissions. It involves building a framework of policies, controls, and oversight mechanisms that balance operational efficiency with security. The following best practices are widely recognized as essential for protecting organizations from misuse of privileged access.
Apply the Principle of Least Privilege
At the foundation of privileged account management is the principle of least privilege (PoLP). Users should only be granted the minimum level of access needed to perform their duties, nothing more. This limits potential exposure in the event of credential theft and reduces the likelihood of accidental misuse.
Strengthen Authentication Measures
Traditional passwords are no longer enough to secure privileged accounts. Multi-factor authentication (MFA), combining something a user knows (password), something they have (token), and something they are (biometric), adds a critical security layer. Organizations adopting MFA across privileged accounts significantly reduce the risk of unauthorized access.
Conduct Regular Audits and Access Reviews
Privileged accounts must not remain unchecked. Scheduled audits ensure that only authorized individuals retain elevated access, while access reviews help align permissions with evolving job roles. For example, when an employee transfers departments or leaves the organization, their access rights must be updated or revoked immediately.
Monitor and Log Activities
Every privileged action, whether creating a new account, modifying security settings, or accessing sensitive data, should be logged and monitored. Continuous monitoring allows security teams to identify unusual patterns of behavior and respond before a potential breach escalates.
By embedding these practices into daily operations, organizations can reduce risks, reinforce compliance, and maintain stronger control over their digital environments.
READ ALSO: Phishing Attacks: Types, Examples, and How to Prevent Them
Strategies to Mitigate Access Vulnerabilities
Even with strong policies in place, privileged accounts remain attractive targets for attackers. To strengthen resilience, organizations need strategies that go beyond static controls and adapt to evolving threats. Several approaches have emerged as effective in mitigating vulnerabilities linked to privileged access.
Just-in-Time Access
One of the most effective safeguards is granting privileged rights only when they are needed, and only for as long as necessary. This just-in-time (JIT) model reduces standing privileges that attackers could exploit if credentials are stolen. By automatically expiring access once a task is complete, JIT access limits the window of opportunity for misuse.
Segregation of Duties
No single individual should have unchecked authority over critical systems. Dividing responsibilities between teams or individuals ensures that oversight is distributed and malicious actions are harder to conceal. For instance, one administrator may approve system changes while another executes them, creating built-in accountability.
Deploying Privileged Access Management (PAM) Tools
Modern Privileged Access Management (PAM) solutions provide centralized control over privileged accounts. These tools enforce strong authentication, manage credentials, and record user activity. More importantly, they give security teams real-time visibility into who is accessing what, allowing suspicious behavior to be flagged and investigated early.
By combining these strategies, organizations not only reduce vulnerabilities but also build a layered defense that strengthens both prevention and detection. In practice, it is this layered approach that offers the greatest protection against insider misuse and external compromise.
Training and Awareness Programs
Technology alone cannot secure privileged accounts. The individuals who hold these roles must be continually trained to recognize risks, follow security protocols, and adapt to evolving threats. Without awareness, even the most advanced technical safeguards can be undermined by human error.
Continuous Education
Privileged users should undergo regular training sessions focused on emerging threats, updated policies, and the consequences of misuse. These sessions reinforce the importance of their role as custodians of sensitive systems and help embed security as part of daily practice rather than an afterthought.
Simulated Threat Exercises
Practical exercises, such as phishing simulations or red-team scenarios, provide hands-on experience in identifying and responding to cyber threats. By replicating real-world attack patterns, organizations can assess how well privileged users react under pressure and identify areas for improvement.
Staying Current with Security Trends
The threat landscape shifts rapidly, with new attack methods and vulnerabilities emerging constantly. Providing privileged users with regular updates, through newsletters, workshops, or security briefings, ensures they remain informed about both technical advances and attacker tactics.
Well-trained privileged users act as a first line of defense. When supported with awareness programs and practical exercises, they are better equipped to make sound decisions, minimize mistakes, and uphold the organization’s overall security posture.
SEE MORE: Cybersecurity Internship Technical Interview Questions
Incident Response and Recovery Plans
Even with strong controls and training, security incidents involving privileged accounts are inevitable. What separates resilient organizations from vulnerable ones is how quickly and effectively they respond. Clear incident response and recovery plans are therefore essential for limiting damage and restoring trust.
Preparation Before Incidents
Privileged users should know their exact responsibilities in the event of a breach. Documented protocols, covering containment, escalation, and communication, provide a roadmap for action. Regular drills ensure that when a real incident occurs, responses are fast, coordinated, and effective.
Effective Response Strategies
When a breach is detected, immediate steps must be taken to contain the threat. This may involve suspending compromised accounts, isolating affected systems, and conducting forensic analysis. Equally important is timely communication with internal stakeholders and, if required, external regulators. Transparency helps maintain credibility even under pressure.
Recovery and Post-Incident Analysis
Recovery goes beyond restoring systems and data. It requires analyzing the root cause of the breach, identifying gaps in controls, and updating security measures accordingly. Lessons learned should be documented and fed back into the organization’s cybersecurity framework to strengthen defenses against future incidents.
Incident response is not simply a reactive measure; it is part of an ongoing cycle of preparation, action, and improvement. For privileged users, knowing how to act during and after an incident can determine whether the organization emerges stronger or faces lasting consequences.
Case Studies and Real-World Examples
Real-world incidents highlight both the value of strong privileged access controls and the risks of failing to enforce them. Examining these cases provides lessons that extend beyond theory and into practical, lived experience.
When Privileged Access Is Misused
The case of Edward Snowden remains one of the most prominent examples of insider misuse. As a contractor for the U.S. National Security Agency (NSA), Snowden leveraged his administrative privileges to exfiltrate vast amounts of classified data. The incident revealed how unchecked access can lead to disclosures with global consequences.
Another example involves Shannon Stafford, a former IT employee at a multinational corporation. After his termination, Stafford retained knowledge of system credentials, which he later used to sabotage networks and delete critical data. This case underscores the importance of immediately revoking access when employees change roles or leave an organization.
Lessons from Strong Controls
Not all stories are failures. Many organizations have successfully prevented breaches through rigorous privileged access management. For instance, financial institutions adopting Privileged Access Management (PAM) tools report significant reductions in insider threats by enforcing multifactor authentication, logging administrator actions, and limiting standing privileges. These success stories show that with the right controls, privileged access can be both powerful and secure.
The contrasting outcomes of these cases reinforce a clear message: privileged access is a double-edged sword. Without oversight, it can facilitate catastrophic breaches. With proper controls, it becomes a cornerstone of organizational resilience.
Conclusion
Privileged users sit at the center of modern cybersecurity. Their elevated access makes them indispensable for maintaining systems, but it also positions them as high-value targets for attackers and potential sources of insider risk. The balance between empowerment and control is delicate, and organizations that fail to strike it leave themselves exposed to financial, operational, and reputational harm.
By applying the principle of least privilege, implementing strong authentication, conducting regular audits, and investing in training, organizations can reduce vulnerabilities tied to privileged accounts. Layered strategies, such as just-in-time access, segregation of duties, and Privileged Access Management (PAM) solutions, further reinforce defenses.
Privileged users must be seen not only as administrators but as stewards of trust. When supported with the right tools, policies, and awareness, they strengthen the security of the digital ecosystem they manage. For organizations navigating today’s evolving threat landscape, safeguarding privileged access is not optional; it is foundational to resilience.
FAQ
What is cybersecurity privileged access?
Privileged access in cybersecurity refers to elevated permissions that allow a user to perform administrative tasks beyond those of a standard user. This includes installing software, configuring systems, creating or deleting accounts, and accessing sensitive data repositories. Because privileged access grants control over critical systems, it is closely monitored and governed by strict security protocols.
What are the 5 C’s of cyber security?
The “5 C’s” serve as a framework for evaluating and strengthening cybersecurity strategies:
Change – adapting security measures to evolving threats.
Compliance – meeting regulatory and industry standards.
Cost – balancing security investments with business priorities.
Continuity – ensuring operations can continue even after an incident.
Coverage – maintaining visibility across all digital assets and access points.
Together, these principles help organizations develop a well-rounded security posture.
What is the difference between a standard user and a privileged user?
A standard user has limited access, typically confined to performing job-specific tasks such as using applications or accessing approved files. A privileged user, on the other hand, can make system-wide changes, configure security settings, and access restricted data. The distinction lies in the scope of authority: standard users interact with systems, while privileged users control them.
Is PAM difficult to implement?
Privileged Access Management (PAM) solutions can be complex to deploy because they often require integration with existing systems, alignment with security policies, and user training. However, modern PAM tools are designed with scalability and usability in mind.
While initial setup may demand time and resources, the long-term benefits, such as reduced insider threats, improved compliance, and stronger visibility, typically outweigh the challenges. Many organizations choose phased implementations to ease the transition.
