
Vendor Risk Management (VRM) in 2025
Vendor Risk Management (VRM) in 2025
In 2025, most businesses depend on third-party vendors more than ever, from IT service providers and cloud platforms to marketing contractors and logistics partners. But while these partnerships help organizations scale faster and operate more efficiently, they also introduce new risks, especially when it comes to data security, regulatory compliance, and business continuity.
A single breach caused by a vendor could expose customer data, halt operations, or trigger regulatory penalties. And that’s not theory, it’s happening every month across industries. That’s why Vendor Risk Management (VRM) has shifted from a compliance checkbox to a business-critical strategy.
Vendor Risk Management is the process of identifying, assessing, and mitigating the potential risks that third-party vendors pose to your organization. And it doesn’t just apply to massive enterprises. Whether you’re a fintech startup in Lagos or a healthcare provider in Atlanta, your vendors are part of your extended risk surface.
In this guide, we’ll walk you through everything you need to know to build a smart, modern VRM program. You’ll learn the different types of vendor risks, how to assess them, and what tools and frameworks help you manage them, plus how platforms like Trust Exchange, UpGuard, and ExcelMind are leading the way in the vendor risk space.
Let’s begin by breaking down what Vendor Risk Management (VRM) really means, and why it’s no longer optional.

Start a Life-Changing Career in Cybersecurity Today
What Is Vendor Risk Management (VRM)?
Vendor Risk Management (VRM) refers to the structured process of identifying, assessing, and reducing the potential risks posed by third-party vendors, suppliers, and service providers. These external partners, while essential to modern business operations, can introduce serious vulnerabilities if not properly managed.
Whether a vendor has access to your financial systems, customer data, or internal infrastructure, they become part of your risk ecosystem. This is especially true for sectors like fintech, healthcare, and education, where vendors often handle sensitive information or power critical backend services.
Why It’s Important
A weak link in your vendor chain can result in data breaches, regulatory violations, reputational harm, or operational downtime. And in today’s global environment, that weak link can be located thousands of miles away, operating in a completely different regulatory framework.
VRM provides the structure to manage those risks, ensuring that each vendor is properly vetted, monitored, and held to a security and compliance standard that matches your organization’s risk appetite.
The VRM Process at a Glance
At its core, VRM isn’t just about vetting a vendor once and forgetting about them. It’s a full lifecycle process that includes:
- Pre-engagement due diligence
- Contractual protections
- Ongoing monitoring and audits
- Performance and security reviews
- Offboarding procedures
For example, ExcelMind, a Nigerian edtech platform, runs a vendor risk checklist before granting third-party platforms access to student data. They don’t just stop at approval; vendors are continuously monitored for changes in data handling policies, system vulnerabilities, and regulatory shifts like NDPR (Nigeria Data Protection Regulation).
The Goal of VRM
Vendor Risk Management helps you answer a simple but critical question: Is this vendor a risk or an asset to my business?
A well-run VRM program protects your company from the hidden costs of outsourcing, giving you control over third-party interactions, ensuring compliance, and preserving your business reputation.
RELATED: What Is Enterprise Risk Management (ERM)? Types, Pillars, Stakeholders
Types of Vendor Risks: What You Need to Watch Out For
Working with third-party vendors brings undeniable benefits, cost savings, specialization, faster operations. But those benefits also come with risks that can hit hard if overlooked. An effective Vendor Risk Management (VRM) program starts with knowing what can go wrong.
Below are the five most common types of vendor risks every organization should assess and prepare for:
1. Legal Risk
This involves the potential for a vendor to violate laws or breach contracts in a way that exposes your organization to liability.
For instance, if a vendor mismanages customer data and violates data privacy laws like Nigeria’s NDPR or the U.S. HIPAA regulations, your organization could be held responsible, even if you weren’t directly involved.
Why It Matters:
Poorly written contracts or unclear responsibilities can leave you with limited legal recourse. That’s why strong vendor contracts with clear service level agreements (SLAs), data-sharing terms, and “right to audit” clauses are foundational to legal protection.
2. Reputational Risk
A vendor’s actions can quickly damage your organization’s public image. It could be a data breach, employee misconduct, or poor service delivery that customers trace back to you, not your vendor.
Example:
A school using an education platform like ExcelMind could lose parent trust if a partner vendor leaks student results or mismanages fee transactions. Even though the school didn’t cause the issue, it bears the brunt of the backlash.
Why It Matters:
Brand perception is fragile. Even one negative headline can cost millions in lost trust and future revenue.
3. Financial Risk
Financial risk emerges when a vendor cannot deliver services as promised due to instability, poor financial management, or bankruptcy.
Key Considerations:
- Does the vendor have a stable financial history?
- Can they fulfill long-term obligations?
- Are there hidden costs in over-dependency?
Why It Matters:
Over-reliance on a single vendor with shaky finances can disrupt business continuity, especially if they provide core services like cloud storage or payment processing.
4. Cybersecurity Risk
This is often the most dangerous and least predictable type of risk. If a vendor’s systems are compromised, threat actors can use them as a gateway into your network.
What to Watch For:
- Weak password policies
- Unpatched systems
- Poor encryption standards
- Limited incident response plans
Why It Matters:
Cyber incidents tied to vendors are on the rise, and damage isn’t limited to data loss. It could mean regulatory fines, lawsuits, or a complete shutdown of critical services.
5. Fourth-Party Risk
Yes, your vendor’s vendors matter too. This risk refers to vulnerabilities introduced by subcontractors or third-party tools your vendor depends on.
Why It Matters:
Most organizations don’t map their full vendor ecosystem. That makes them blind to threats introduced by companies two or three degrees removed, until a breach makes it obvious.
Example:
If your HR software vendor uses a cloud provider that gets hacked, your employee data could be compromised, without your knowledge or consent.
In Summary:
Each vendor brings different types of risk. Some are visible upfront (like financial records), while others emerge over time (like cybersecurity threats or fourth-party weaknesses). A successful VRM program should account for all five, and develop a strategy that prevents, detects, and responds effectively.
READ ALSO: Cybersecurity vs Cloud Computing: A Comprehensive Comparison
The Vendor Risk Management Lifecycle (VRM Workflow)
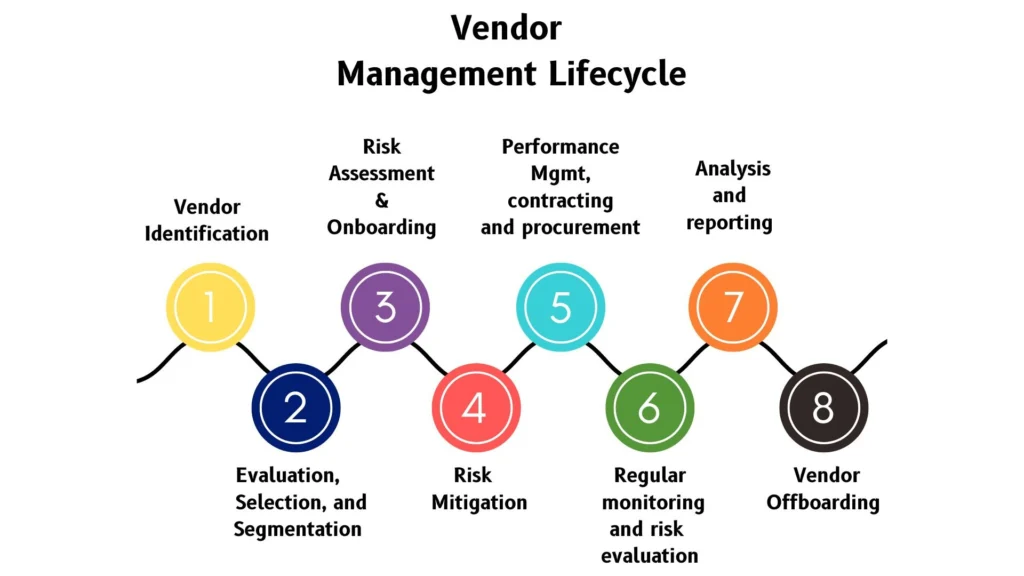
Vendor Risk Management (VRM) is a lifecycle. From the moment a vendor is considered to the day the relationship ends, each stage plays a critical role in protecting your business from unnecessary risk.
Below is a breakdown of the full VRM lifecycle that modern organizations follow in 2025:
Step 1: Define Business Needs and Risk Appetite
Before sourcing a vendor, clarify:
- What service or product is needed?
- What level of risk is acceptable?
- What data will the vendor access?
By aligning with your organization’s internal security, legal, and procurement teams at this stage, you avoid missteps later in the process.
Step 2: Vendor Screening and Due Diligence
This is your first defense against risky partnerships.
Conduct:
- Background checks
- Financial audits
- Cybersecurity posture reviews
- Reputation research
- Certification validation (e.g., ISO 27001, SOC 2)
Tip: Use a pre-vetting questionnaire tailored to the vendor type, ExcelMind, for example, uses different vetting processes for local internet providers vs. cloud service providers handling student records.
Step 3: Risk Assessment and Tiering
After initial vetting, categorize vendors by their risk level. Common tiers include:
- Tier 1: Critical vendors (access to sensitive data or core systems)
- Tier 2: Important vendors (non-core but still essential)
- Tier 3: Low-risk vendors (minimal data access or service dependency)
This helps you allocate resources wisely, more scrutiny for Tier 1 vendors, streamlined oversight for Tier 3.
Step 4: Contract Negotiation and Risk Control Measures
Once you’ve selected a vendor, formalize the relationship with a contract that includes:
- SLAs (Service Level Agreements)
- Data protection clauses
- Regulatory compliance expectations
- “Right to audit” provisions
- Incident response requirements
- Termination protocols
Best Practice: Use templated contracts reviewed by legal and compliance teams to ensure nothing is missed.
Step 5: Onboarding and Access Controls
Give the vendor only the access they need—and no more. Limit exposure by:
- Creating temporary accounts
- Enabling MFA (Multi-Factor Authentication)
- Restricting file or system access by role
Ensure they receive onboarding materials that explain how to handle data responsibly according to your company’s standards.
Step 6: Continuous Monitoring and Performance Review
The biggest mistake companies make? Thinking risk ends once a vendor is onboarded.
Your VRM workflow must include:
- Quarterly or biannual risk re-assessments
- Cybersecurity monitoring tools (e.g., UpGuard or Trust Exchange)
- Vendor performance tracking against agreed KPIs
- SLA enforcement and accountability measures
Step 7: Offboarding and Post-Contract Review
When a vendor relationship ends:
- Revoke all system access
- Retrieve or delete shared data
- Conduct an exit audit to ensure compliance
- Review lessons learned from the engagement
This final step ensures there are no loose ends that could pose a risk later—especially with sensitive data that may still be in the vendor’s possession.
Summary:
Think of Vendor Risk Management like a relay race, not a sprint. Each step passes the baton to the next, with risk controls in place every step of the way. By following this lifecycle, organizations avoid costly mistakes and build secure, high-trust vendor relationships.
ALSO SEE: HR vs Cybersecurity: Which Career Path Offers More Opportunity in 2025?
Essential Components of a Strong VRM Strategy

A well-designed Vendor Risk Management (VRM) strategy is more than a checklist; it’s a framework that keeps your organization secure, compliant, and resilient. Every organization, whether large or small, needs a structure that governs how it interacts with third parties across the vendor lifecycle.
Below are the non-negotiable components of a modern, effective VRM strategy in 2025:
1. Clear Contracts and Service-Level Agreements (SLAs)
Your first layer of protection is the contract. It should:
- Define each party’s responsibilities
- Outline security and data handling expectations
- Specify SLAs with measurable performance standards
- Include termination clauses and penalties for non-compliance
Why It Matters:
A vague contract creates room for risk and confusion. Strong contracts, on the other hand, offer legal protection and clarity when things go wrong.
2. Defined Data Access and Handling Policies
Know exactly:
- What data your vendor will access
- Who within the vendor’s team has that access
- How the data will be stored, used, and deleted
Best Practice:
Include a data classification matrix in your onboarding documents. This helps vendors know what kind of data they’re dealing with and what safeguards are expected.
3. Cybersecurity Posture Evaluation
Don’t assume vendors secure their systems like you do. Evaluate their:
- Security architecture
- Use of encryption and MFA
- Incident response procedures
- History of breaches or audit failures
Tools to Help:
Use platforms like UpGuard or BitSight to generate real-time vendor security scores. This gives you continuous visibility beyond the onboarding phase.
4. Compliance with Regulatory Standards
Whether it’s Nigeria’s NDPR, the U.S. HIPAA law, or GDPR in Europe, vendors must comply with all data and industry-specific regulations. Your VRM strategy should:
- Require compliance documentation (certificates, audit reports)
- Assign a compliance officer to track changes in regulation
- Embed compliance checks in periodic vendor reviews
Real-World Example:
Edtech platforms like ExcelMind integrate compliance training into their vendor onboarding program, especially when vendors process student records, which fall under child data protection laws.
5. Vendor Performance Monitoring
Risk isn’t always about data; it’s also about delivery. Performance issues can signal underlying financial, operational, or ethical risks.
What to monitor:
- On-time delivery rates
- Quality control issues
- Missed SLAs
- Customer complaints or helpdesk tickets tied to the vendor
Tip:
Track vendor KPIs in a dashboard that both your internal team and the vendor can access. This creates transparency and mutual accountability.
6. Incident Response Alignment
Your vendors need to know how to respond when things go wrong—and how to notify you.
Your strategy should include:
- Escalation protocols
- Notification timelines
- Data breach playbooks
- Points of contact during emergencies
Why It Matters:
In the event of a cyber incident, minutes matter. An aligned incident response plan minimizes damage and ensures legal obligations are met.
7. Exit and Offboarding Protocols
When a contract ends, it’s not just a goodbye. You must:
- Remove vendor access to internal systems
- Retrieve or destroy shared data
- Reassign business functions internally or to a new vendor
- Conduct a post-engagement risk review
Checklist Tip:
Create a reusable offboarding checklist that is mandatory for every vendor exit, whether planned or abrupt.
Summary:
A strong VRM strategy is about managing risk. By building these components into your VRM process, you reduce blind spots, gain visibility, and stay in control of the vendor relationships that power your business.
READ: Accounting vs Cybersecurity: Everything You Need to Know
Building a Vendor Risk Assessment Framework
Not all vendors present the same level of risk. Some may have access to sensitive customer data, while others simply provide one-time support services. That’s why having a structured Vendor Risk Assessment Framework is essential. It allows you to measure, compare, and prioritize vendors based on the level of risk they pose to your organization.
Here’s how to build a smart, scalable framework that works, whether you’re a fintech startup or a multinational.
Step 1: Determine Risk Categories
Start by defining the areas where vendor-related risk can occur. The most common categories include:
- Cybersecurity Risk
- Financial Risk
- Operational Risk
- Compliance Risk
- Reputational Risk
- Data Access Risk
- Fourth-Party Risk
Each of these categories will have its own set of risk indicators or “flags.”
Step 2: Identify Risk Indicators
For each category, outline specific questions or metrics that will help you assess the vendor’s risk level.
For example, under Cybersecurity Risk, ask:
- Does the vendor have a documented incident response plan?
- Do they use encryption for data at rest and in transit?
- Have they had any reported breaches in the last 24 months?
Under Financial Risk, consider:
- Is the vendor profitable or backed by stable funding?
- Do they have liability insurance?
- Are there any red flags in their credit history?
Use these questions to build a questionnaire or scoring system.
Step 3: Score and Tier Vendors
Assign scores to each risk category based on the vendor’s answers or documentation provided. For instance:
| Risk Category | Weight | Vendor Score | Weighted Score |
| Cybersecurity Risk | 30% | 7/10 | 2.1 |
| Financial Risk | 20% | 5/10 | 1.0 |
| Compliance Risk | 25% | 9/10 | 2.25 |
| Data Access Risk | 25% | 4/10 | 1.0 |
| Total | 6.35/10 |
After calculating the total score, classify the vendor into risk tiers:
- Low-Risk (8–10): Minimal monitoring required
- Medium-Risk (5–7.9): Standard monitoring and reviews
- High-Risk (0–4.9): Requires continuous monitoring or reconsideration
Step 4: Tailor Controls to the Risk Tier
Your assessment results should directly inform your oversight strategy. For example:
- Low-Risk Vendor: Annual reviews, standard contract
- Medium-Risk Vendor: Bi-annual reviews, enhanced contract clauses
- High-Risk Vendor: Monthly monitoring, restricted access, audit rights
This approach prevents overloading your team by applying heavy oversight to every vendor, and instead focuses your effort where it matters most.
Step 5: Use Tools for Automation
Manual assessments can be slow and error-prone, especially as your vendor list grows. Instead, use tools like:
- Trust Exchange for centralized documentation tracking
- Prevalent or UpGuard for real-time security scoring
- Vendor risk management software for automated questionnaires and follow-ups
Automation makes your assessment framework scalable and keeps data up to date without constant manual checks.
Step 6: Re-Assess Regularly
Vendor risk is not static. Business conditions, cyber threats, and compliance obligations evolve.
Set re-assessment intervals based on the vendor’s risk tier:
- Low-risk: Reassess annually
- Medium-risk: Every 6 months
- High-risk: Quarterly or ongoing monitoring
Don’t just assess once and forget; risk grows in silence.
Summary:
An effective Vendor Risk Assessment Framework helps your organization:
- Make smarter vendor decisions
- Prioritize resources
- Meet compliance obligations
- Reduce surprises from hidden threats
By making your assessments structured, repeatable, and scalable, you move from reactive risk management to strategic control.
SEE: GRC Analyst vs SOC Analyst: Everything You Need To Know
How to Continuously Monitor Vendor Risks in 2025
Vendor risk doesn’t disappear after onboarding. In fact, most issues, data breaches, compliance failures, financial instability emerge after the contract is signed. That’s why continuous monitoring is now a foundational requirement of any mature Vendor Risk Management (VRM) program.
In 2025, the smartest organizations are no longer relying on annual check-ins or static risk reports. They’ve adopted real-time monitoring tools, automated alerts, and integrated dashboards that help them spot and respond to risks before they escalate.
Here’s how to implement a continuous monitoring process that keeps your vendor ecosystem secure and compliant:
1. Use Security Rating Tools
Platforms like UpGuard, BitSight, and SecurityScorecard automatically assess your vendors’ cybersecurity health using external signals, like SSL configurations, leaked credentials, or vulnerability disclosures.
These tools assign vendors a live security score (e.g., A–F or 0–100), which allows you to:
- Get alerted to sudden score drops
- Track risk trends over time
- Compare vendors against industry benchmarks
Why it matters:
Instead of waiting for an audit, you can respond to weaknesses the moment they appear.
2. Integrate SLA and KPI Tracking
Performance issues often signal deeper risks. If a vendor starts missing deadlines, making errors, or underperforming against SLAs, you may be witnessing the early signs of:
- Financial strain
- Staffing issues
- Operational breakdown
Set up automated performance dashboards to track:
- Uptime/downtime
- Delivery timeframes
- Error rates
- Support ticket resolution speeds
Example:
ExcelMind tracks response times of its SMS delivery partner in real-time. If there’s a delay, the team is notified within minutes, not weeks.
3. Monitor Compliance and Certification Status
Regulatory environments change fast. Vendors who were compliant a year ago might not be anymore.
Track the status of:
- ISO 27001 / SOC 2 / PCI DSS certifications
- NDPR, GDPR, HIPAA compliance
- Expired licenses or insurance documents
- Legal or regulatory actions reported publicly
Tool Tip:
Use platforms like Trust Exchange or Prevalent to centralize document collection and expiration alerts.
4. Stay Alert to Fourth-Party Risk
In today’s vendor ecosystem, your vendor might outsource parts of their work to their vendors, called fourth parties.
To monitor this layer:
- Ask vendors for a list of their key subcontractors
- Use automated mapping tools to discover fourth-party connections
- Track known vulnerabilities from fourth-party suppliers
Why it matters:
In several recent breaches, the entry point wasn’t the direct vendor, but their forgotten cloud service provider or payment processor.
5. Set Up Real-Time Alerts and Workflows
Whether it’s a security score drop or a missed SLA, your team needs to be notified in real time.
Build notification workflows that:
- Alert vendor managers to new incidents
- Automatically open investigation tickets
- Trigger internal escalations for high-risk vendors
- Document actions taken for audit purposes
Best Practice:
Don’t overwhelm your team with noise. Focus alerts on Tier 1 vendors and incidents above a certain risk threshold.
6. Conduct Periodic Manual Reviews
Technology helps, but human judgment is still crucial. Schedule:
- Quarterly reviews with critical vendors
- Annual full risk re-assessments
- Surprise audits or penetration tests (where applicable)
These reviews offer qualitative insight you won’t get from scorecards alone.
Summary:
Continuous monitoring transforms VRM from a once-a-year checkbox into a live, responsive system. It gives your team ongoing visibility into a vendor’s security posture, performance, and compliance, allowing you to act on emerging risks before they become real problems.
In a world where threats evolve daily, staying still means falling behind.
MORE: CompTIA Security Vs Google Cybersecurity Certification
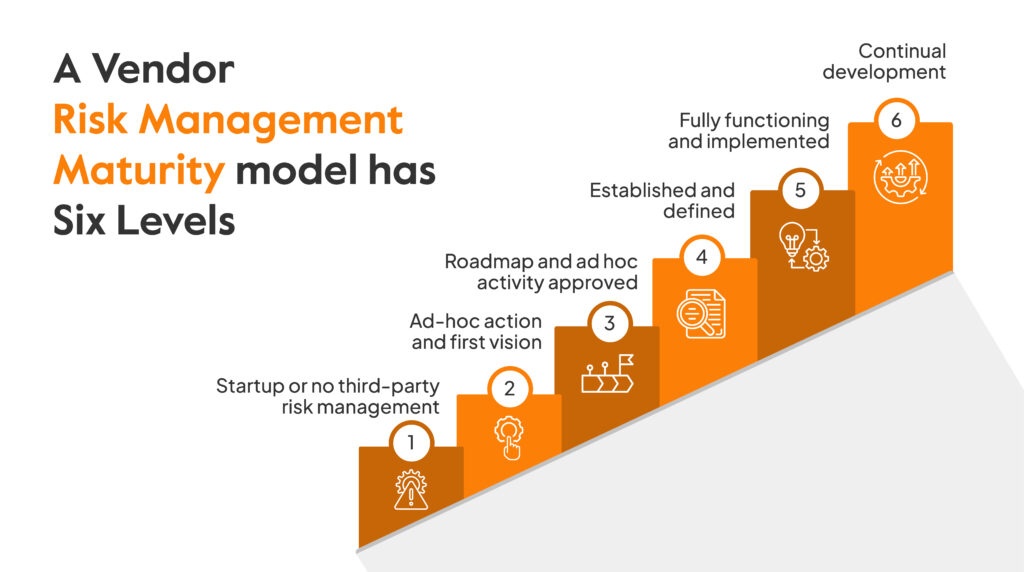
Vendor Risk Management Maturity Model (VRMMM): Where Do You Stand?
Just having a VRM process doesn’t guarantee protection. What matters is how mature that process is. The Vendor Risk Management Maturity Model (VRMMM) is a tool organizations use to measure the depth, efficiency, and effectiveness of their vendor risk efforts, and to map a clear path for growth.
Whether you’re just beginning or optimizing a multi-vendor ecosystem, this model helps answer a crucial question: Are we managing vendor risk the way we should?
What Is a VRMMM?
A Vendor Risk Management Maturity Model outlines the different stages of a VRM program’s development, from ad hoc and reactive to fully operational and continuously improving.
It evaluates areas such as:
- Cybersecurity oversight
- Regulatory compliance
- Vendor onboarding and offboarding
- Performance and incident management
- Cross-functional accountability
Organizations can use the VRMMM to:
- Benchmark their current stage
- Set improvement goals
- Justify VRM investments to leadership
- Identify process gaps before incidents happen
The 6 Maturity Levels
Level 1: No Formal Program (Start-Up Phase)
There’s no documented VRM process. Vendors are engaged on a need basis without structured assessments or monitoring.
- Quick vendor onboarding
- No risk analysis or documented policies
- No accountability framework
Example: A startup relies on freelance developers without checking for data security measures.
Level 2: Ad Hoc and Reactive
Some risk management activities occur, but inconsistently. Processes depend on individual teams, not organization-wide standards.
- Some due diligence for critical vendors
- No formal assessments or tracking
- Limited to no audit trails
Level 3: Defined and Documented
There’s an established process for evaluating and onboarding vendors. Risk assessments are conducted, but may not be enforced or standardized across departments.
- Standard onboarding forms and SLAs
- Basic cybersecurity assessments
- Inconsistent enforcement and monitoring
Level 4: Operationalized and Scalable
The VRM process is fully integrated across the organization. All departments follow the same protocol, and automation tools are used for assessments, alerts, and documentation.
- Vendor risk tiering system in place
- Real-time monitoring tools in use
- Compliance and performance metrics tracked
- Limited improvement cycles or benchmarking
Level 5: Optimized and Continuously Improving
At this level, vendor risk is a strategic function. The organization uses data and analytics to predict, prevent, and respond to risk. Regular internal audits and external benchmarking are routine.
- AI-enhanced monitoring tools
- Quarterly re-assessments and board-level reporting
- Risk exposure tied to business objectives
- Industry-leading best practices embedded
Example: A global fintech firm continuously tracks all third- and fourth-party vendors using automated GRC platforms and adjusts thresholds based on geopolitical or economic shifts.
How to Use the Model
- Diagnose Your Level: Based on the descriptions above, identify where your organization fits today.
- Set Goals: Choose which maturity level to aim for within the next 12–18 months.
- Build a Roadmap: List what needs to be done to close the gaps—people, processes, and tools.
- Measure Progress: Use periodic self-assessments or third-party evaluations to track improvement.
Summary:
You can’t fix what you don’t measure. The VRMMM offers a clear, progressive structure to help organizations elevate their vendor risk practices, from informal beginnings to fully optimized systems. No matter your current level, the goal is always the same: reduce risk, improve performance, and gain full control of your vendor relationships.
Conclusion
In 2025, vendor risk isn’t something companies might face; it’s something they must plan for. As organizations deepen their reliance on third parties for critical operations, cloud infrastructure, customer engagement, and more, the boundaries of risk expand beyond internal walls.
From data breaches to compliance penalties, service disruptions to reputational fallout, the consequences of overlooking third-party risk are real and expensive.
That’s where a proactive Vendor Risk Management (VRM) strategy makes all the difference.
A strong VRM program:
- Protects your business from legal, financial, and reputational damage
- Builds trust with customers, investors, and regulators
- Keeps your organization compliant in a fast-changing regulatory landscape
- Ensures service continuity through vendor performance and redundancy planning
- Gives you clear visibility into risks before they escalate
But beyond protection, VRM is also about empowerment. It allows organizations to make better decisions about who they work with, how they work together, and what level of risk is acceptable in the pursuit of growth.
Whether you’re a startup managing five vendors or a large enterprise managing five hundred, your VRM efforts will define how confidently you scale and how securely you operate.
The tools, frameworks, and practices outlined in this guide are not just recommendations; they’re the new standard for risk-aware, future-ready organizations.
FAQ
What are the 4 classifications of risk?
The four common classifications of risk in business and compliance are:
Strategic Risk: Related to long-term goals and decisions, such as market changes or poor business planning.
Operational Risk: Stemming from internal processes, systems, or human errors (e.g., supply chain disruptions).
Financial Risk: Linked to monetary loss, includes credit risk, liquidity risk, and investment volatility.
Compliance/Legal Risk: Resulting from violations of laws, regulations, or contractual obligations.
These classifications help organizations assess risk across every function—from operations to third-party vendors.
What are the three main types of risks?
The three main types of risks often referenced in enterprise risk management are:
Business/Operational Risk: Internal failures in processes, people, or systems.
Financial Risk: Exposure to monetary loss due to instability, fraud, or economic shifts.
Reputational Risk: Damage to the organization’s public image, often triggered by incidents like vendor breaches or unethical practices.
While these can overlap, understanding them individually helps in creating targeted mitigation strategies.
Who is a low-risk customer in KYC?
In Know Your Customer (KYC) procedures, a low-risk customer is someone whose identity, financial behavior, and business activities are considered transparent and unlikely to pose money laundering or fraud risks.
Typical low-risk profiles include:
– Salaried employees in government or well-known companies
– Customers with long-standing banking relationships
– Individuals living in countries with strong AML (Anti-Money Laundering) enforcement
– Entities with clear ownership structures and no red flags in background checks
These customers may qualify for simplified due diligence under certain regulatory frameworks.
What are the 5 levels of risk rating?
Risk rating systems often use five levels to classify the severity or likelihood of a threat:
Very Low Risk – Minimal potential for harm or disruption
Low Risk – Unlikely to cause significant issues, manageable without formal controls
Moderate Risk – Requires monitoring or mitigation; may cause some impact
High Risk – Likely to cause operational, financial, or reputational damage
Critical/Severe Risk – Demands immediate attention; could cause major losses or compliance failures.
Organizations often apply this scale during vendor assessments, cybersecurity reviews, and compliance audits to guide decision-making.
Th
